Simple Bluetooth Discovery with Bluelog
Bluelog is a simple Bluetooth scanner that is designed to essentially do just one thing, log all the discoverable devices in the area. It is intended to be used as a site survey tool, identifying the number of possible Bluetooth targets there are in the surrounding environment. This tool only shows visible devices like PCs, phones printers etc. This doesn’t show devices whose visibility is OFF.
Note: Make sure you are not testing this tool on a VM, or if you are, you need to plugin in a USB bluetooth device and attach it to your VM. Also make sure that the device is turned on. Read on for further guidelines.
Options
Syntax: bluelog -i <interface> <options>
Basic Options:
-i <interface> Sets scanning device, default is “hci0”
-o <filename> Sets output filename, default is “devices.log”
-v Verbose, prints discovered devices to the terminal
-q Quiet, turns off nonessential terminal outout
-d Enables daemon mode, Bluelog will run in background
-k Kill an already running Bluelog process
-l Start “Bluelog Live”, default is disabled
Logging Options:
-n Write device names to log, default is disabled
-m Write device manufacturer to log, default is disabled
-c Write device class to log, default is disabled
-f Use “friendly” device class, default is disabled
-t Write timestamps to log, default is disabled
-x Obfuscate discovered MACs, default is disabled
-e Encode discovered MACs with CRC32, default disabled
-b Enable BlueProPro log format, see README
Advanced Options:
-r <retries> Name resolution retries, default is 3
-a <minutes> Amnesia, Bluelog will forget device after given time
-w <seconds> Scanning window in seconds, see README
-s Syslog only mode, no log file. Default is disabled
Bluelog Homepage: http://www.digifail.com/software/bluelog.shtml
Lab1 : Scan all Bluetooth Devices and log them to a file.
In this lab we simply scan for all Bluetooth devices around and log them into a file. First we need to check our Bluetooth interfaces. As I said earlier, make sure to be on a physical machine with bluetooth device turned ON. In some laptops, the hotkeys for turning ON/OFF devices doesn’t work well if you are running kali linux. Then you might have to add additional kernel modules to solve the issue. For the following 2 labs, I have used a Lenovo Notebook, which had some issues in the begining running kali linux. Anyway lets proceed.
Step 1: Ensure your bluetooth device is working and get it’s MAC.
Command:hciconfig
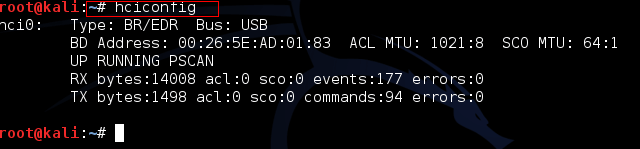
From this we can see the Bluetooth device present in our system/machine. Here we have an interface which is hci0.
Step 2: Start scanning
Command: bluelog -i hci0 -o /root/Desktop/btdevices.log –v
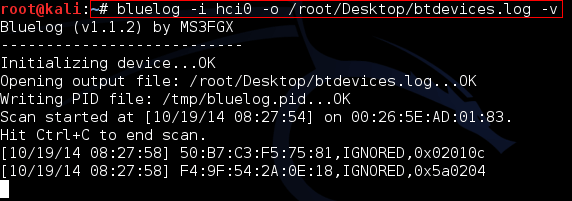
Check the file after btdevices.log after a 10 minutes. You can see all the devices which are nearby you/your working machine.
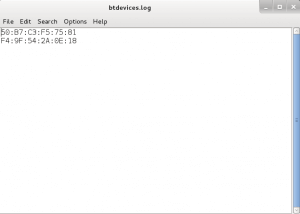
Lab 2 : Logging Additional Information
In this lab, we log additional information l manufacturer, broadcast names and device class.
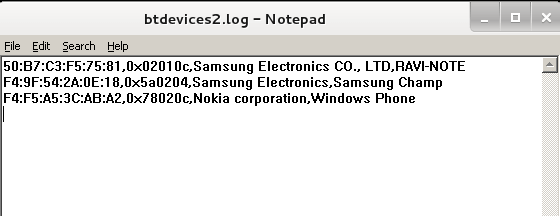
Command: bluelog -i hci0 -mnc -o /root/Desktop/btdevices2.log –v
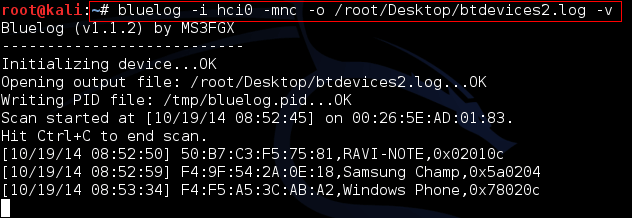
Then Check the file btdevices2.log
Note: Remember scanning is a time consuming process. The more patience you have the better are the results. Also this procedure resembles the process of wardriving. If you have a portable device and can get it around, add up some of your social engineering skills, you get great results.








