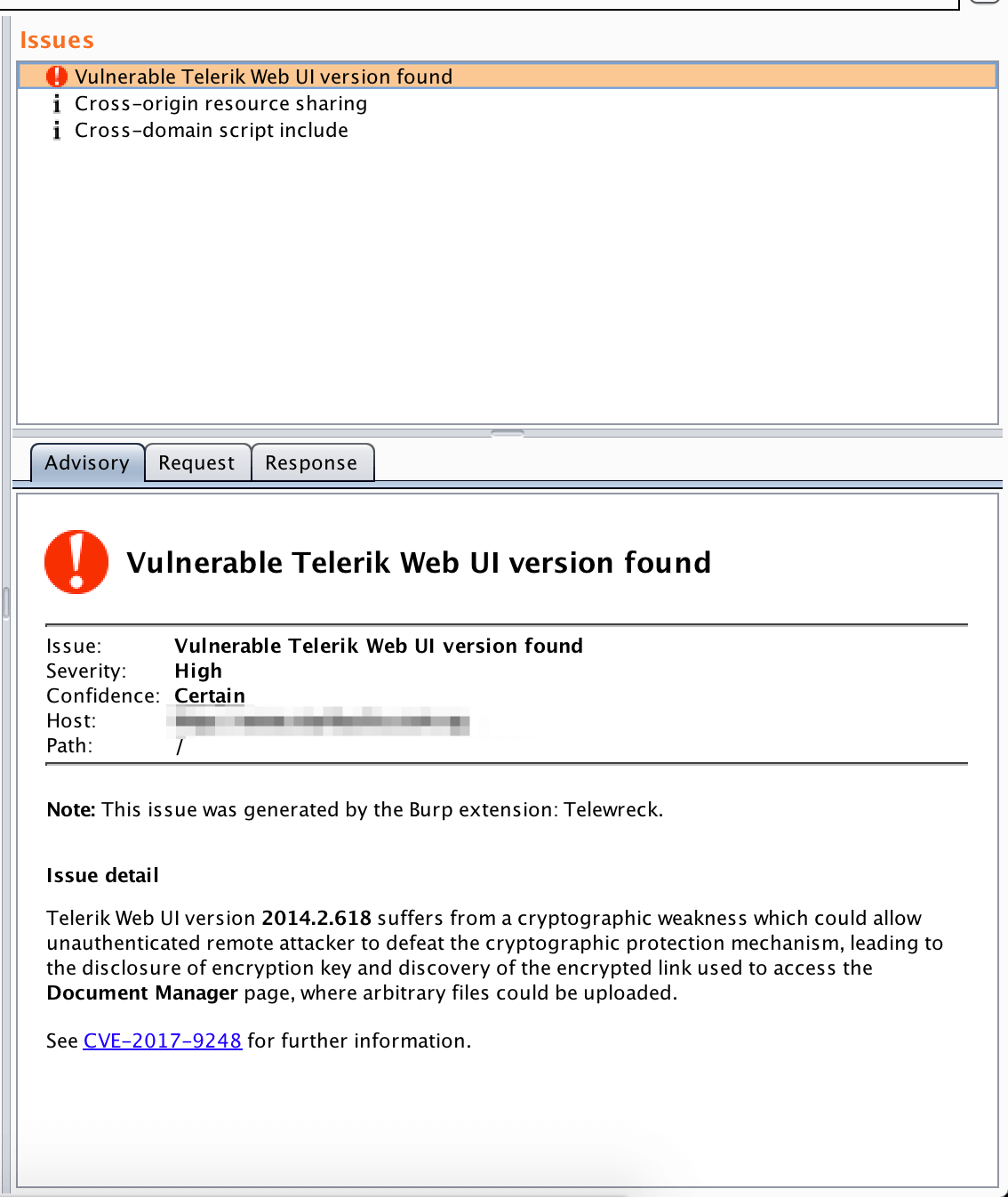
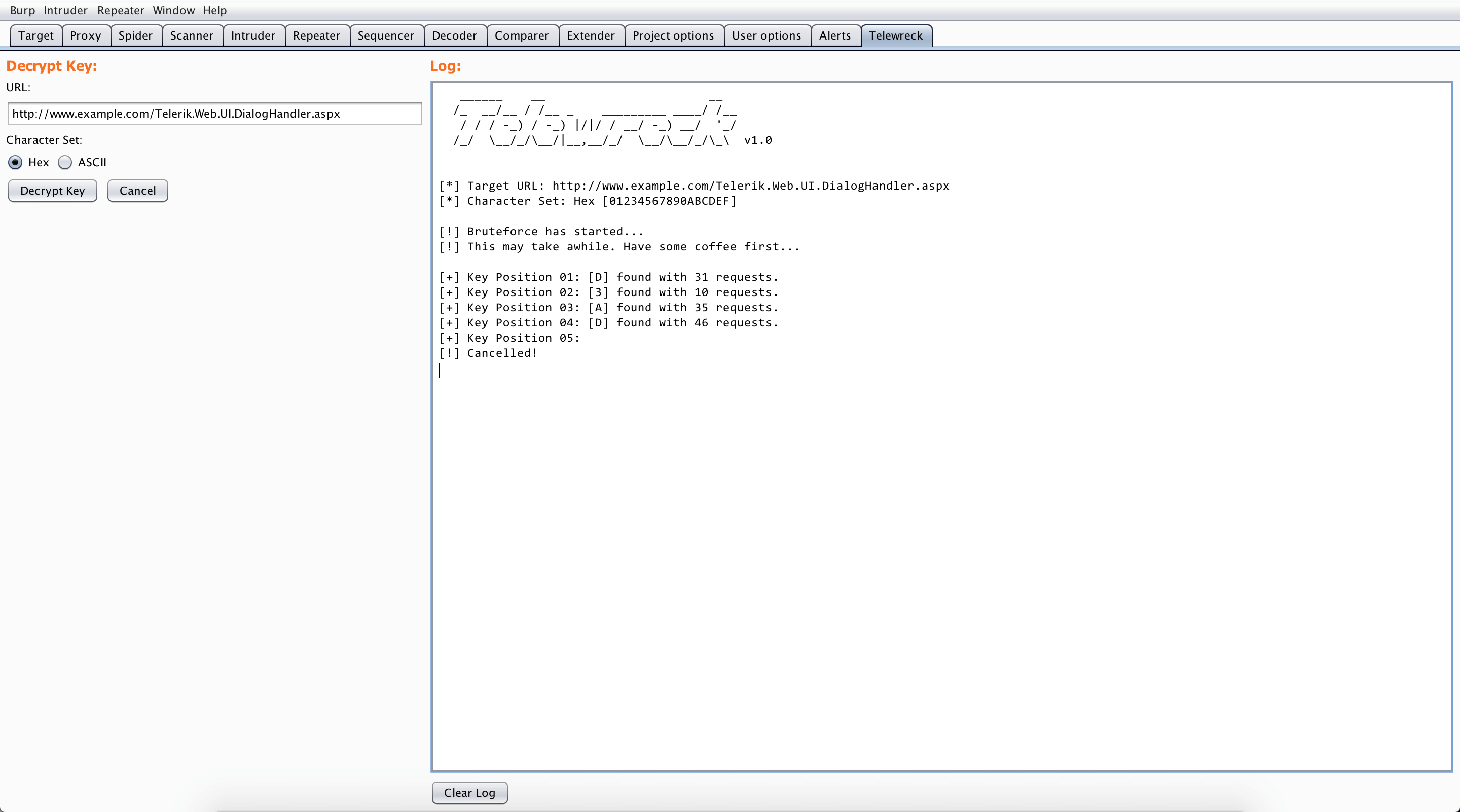
Telewreck is a Burp extension to detect and exploit versions of Telerik Web UI vulnerable to CVE-2017-9248.
Telewreck Attribute
- Detect vulnerable versions of Telerik Web UI during passive scans.
- Bruteforce the key and discover the “Document Manager” link just like the original exploit tool.
Requirements
- Locate Telerik.Web.UI.DialogHandler.aspx
- This extension requires Python’s requests module. Just run
pip install requeststo install it. - The text area under Telewreck tab doesn’t function as a console. So,
stoudandstderroutputs cannot be seen there. However, you can view them under the Output and Errors sections of the Extender tab. - Before running another bruteforce, cancel the current process first by clicking the Cancel button.
- If the key can’t be bruteforced, then probably the key has been set up securely and/or the application is not using a default installation of Telerik.
- If the key can’t be bruteforced and/or there are some issues, it’s recommended to fall back to the original exploit tool.
Also Read SQLMap – SQL Injection & Database Automatic Takeover Tool
Installation Process
- Download telewreck.py to your machine.
- Install Python’s requests module using
sudo pip install requests. - On your Burp, go to Extender > Options tab. Then under the Python Environment section, locate your jython-standalone-2.7.0.jar file (1) and the directory where Python’s requests module is located (2).
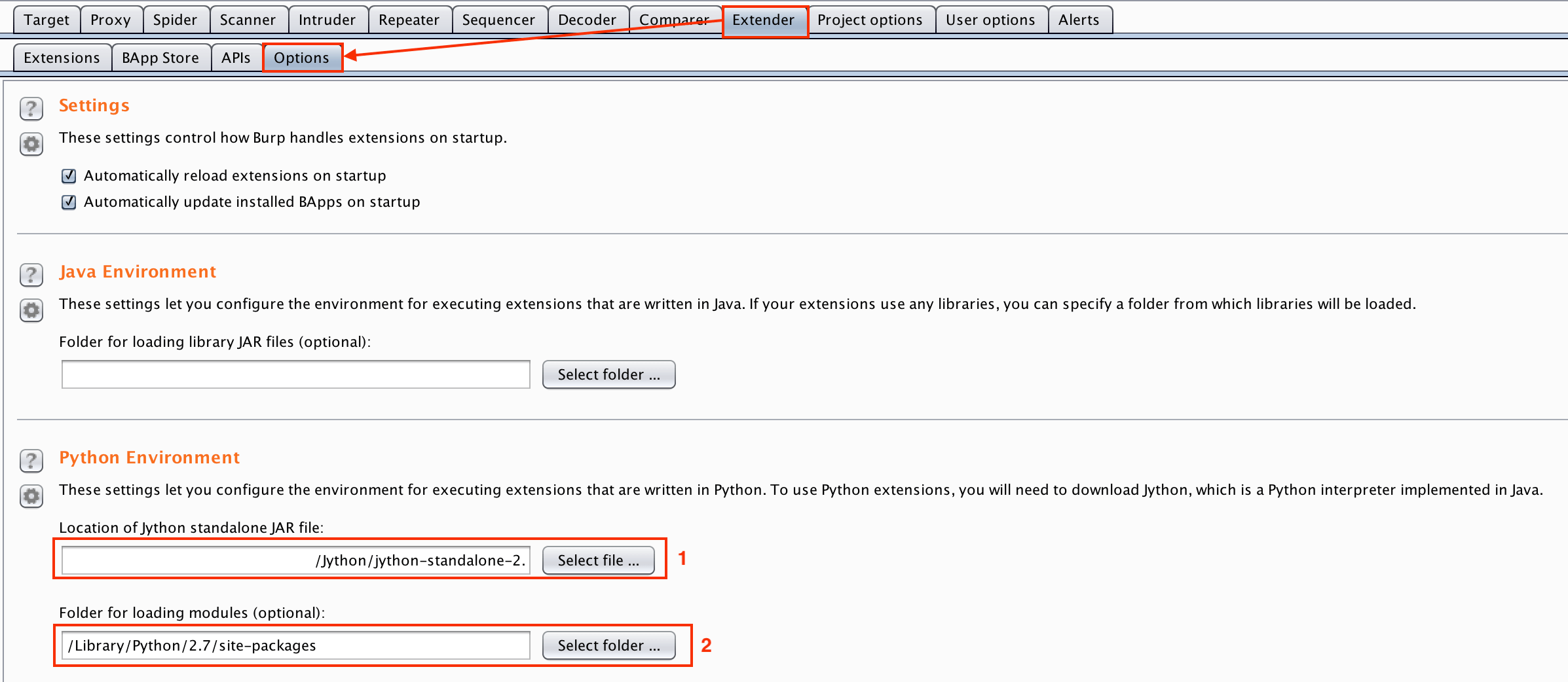
- Go to Extender > Extensions tab, then click on the Add button. On the new window, browse the location of telewreck.py and click the Next button.
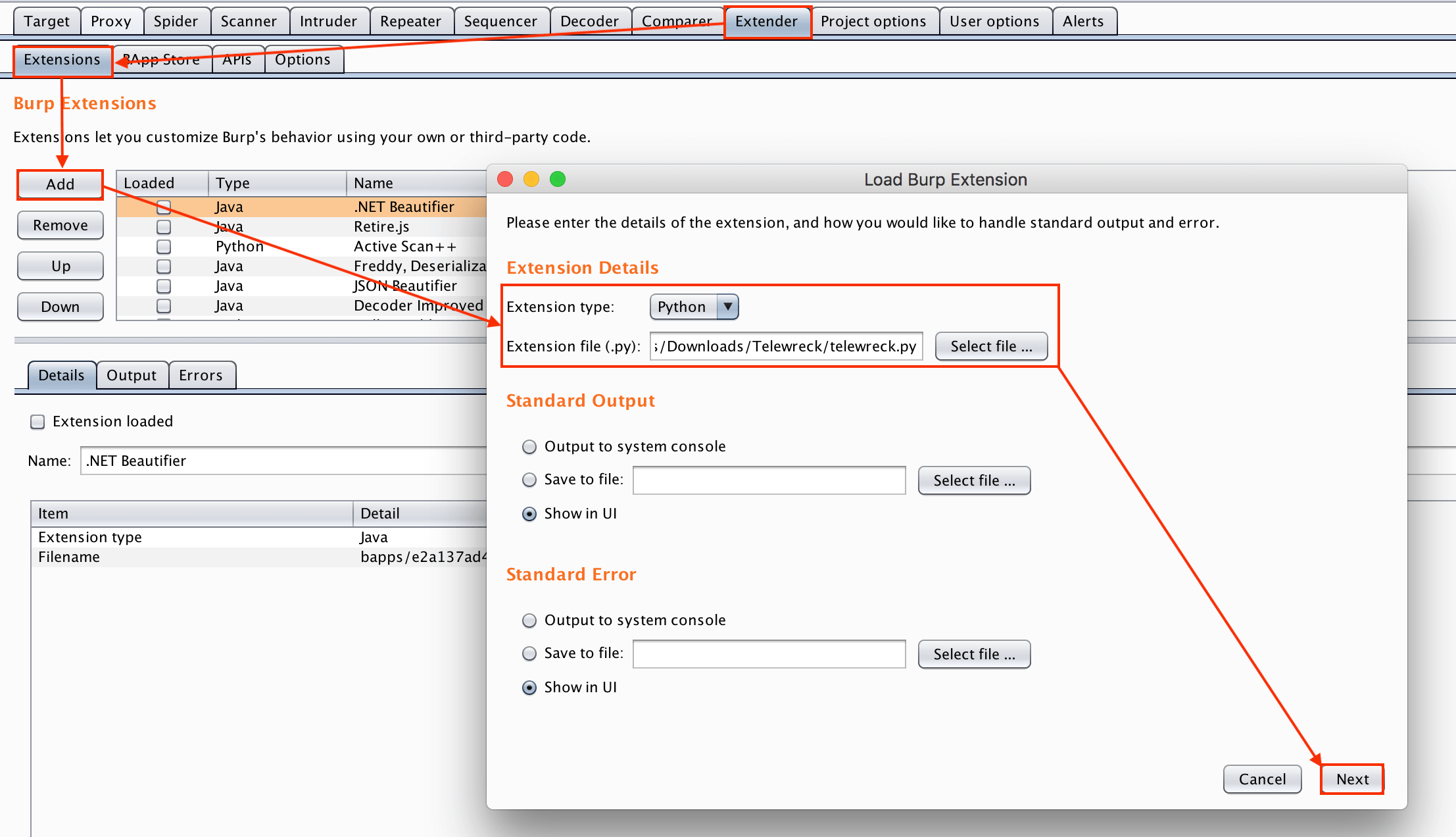
- If there’s any error, the Telewreck tab would appear in your Burp.
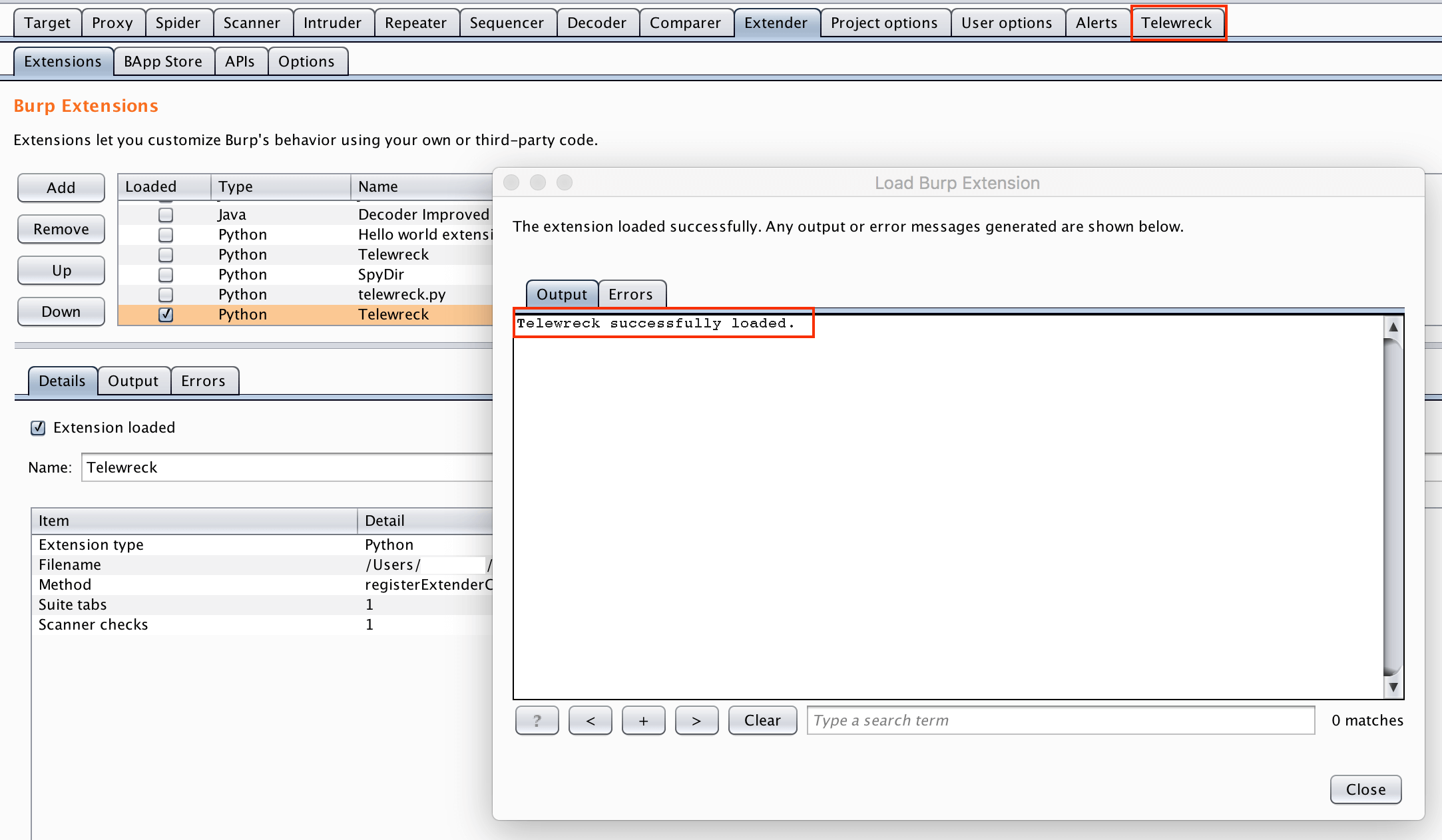
Screenshots
Disclaimer
This tool is created for educational purposes only.
![]() Credit : Paul Taylor (@bao7uo)
Credit : Paul Taylor (@bao7uo)