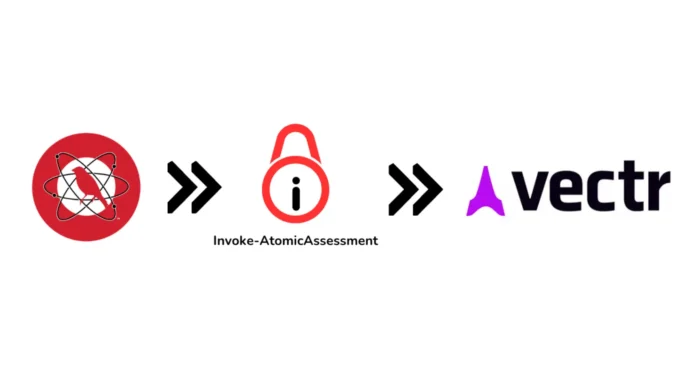
Invoke-AtomicAssessment is a powerful tool designed to facilitate adversary emulation by leveraging Atomic Red Team.
This tool automates the execution of these techniques and logs the results in the ATTiRe format, which can then be visualized on the VECTR platform.
The tool offers various threat actor profiles, enabling simulations of ransomware attacks and activities of Advanced Persistent Threat (APT) groups. The primary goal is to conduct thorough gap analysis to identify and remediate weaknesses in security defenses.
Profiles
The tool includes a collection of pre-configured threat actor profiles, which can be used to simulate specific adversaries or attack scenarios. Below is a list of available profiles:
- Akira: A ransomware group known for targeting enterprises.
- APT41: A Chinese state-sponsored threat group involved in cyber espionage and financial gain.
- BlackCat (ALPHV): A ransomware-as-a-service (RaaS) group targeting multiple industries.
- Lazarus: A North Korean APT group linked to cyber espionage and destructive attacks.
- LockBit: A prolific ransomware group known for its fast encryption and double extortion tactics.
- Mustang Panda: A Chinese APT group focused on espionage and data exfiltration.
- OilRig: An Iranian threat group targeting Middle Eastern organizations for espionage.
In addition to the pre-configured profiles, Invoke-AtomicAssessment allows users to create custom profiles tailored to specific threat actors or attack scenarios. Custom profiles follow a structured JSON format, as shown below:
{
"name": "APT41",
"description": "APT41 is a threat group that researchers have assessed as Chinese state-sponsored espionage group that also conducts financially-motivated operations. Active since at least 2012, APT41 has been observed targeting healthcare, telecom, technology, and video game industries in 14 countries. APT41 overlaps at least partially with public reporting on groups including BARIUM and Winnti Group.",
"references": [
"https://www.group-ib.com/blog/apt41-world-tour-2021/",
"https://cloud.google.com/blog/topics/threat-intelligence/apt41-arisen-from-dust",
"https://malpedia.caad.fkie.fraunhofer.de/actor/apt41"
],
"operating_system": "windows",
"AtomicTests": [
{
"TestNumber": 1,
"Description": "Compiled HTML Help Local Payload",
"Command": "Invoke-AtomicTest T1218.001 -TestNumber 1"
},
{
"TestNumber": 2,
"Description": "Rundll32 with Ordinal Value",
"Command": "Invoke-AtomicTest T1218.011 -TestNumber 11"
},
{
"TestNumber": 3,
"Description": "DLL Side-Loading using the Notepad++ GUP.exe binary",
"Commands": [
"Invoke-AtomicTest T1574.002 -TestNumber 1 -GetPrereqs",
"Invoke-AtomicTest T1574.002 -TestNumber 1"
]
}
]
}For more information click here.











%20Works.png)