WHAT'S NEW
- All
- Accessories
- Android
- Android
- Apple
- Applications
- Blog
- Bluetooth
- Cyber security
- Database Assessment
- Exploitation Tools
- Forensics
- Hacking Courses
- Hacking Tools
- Information Gathering
- iphone
- Kali Linux
- Kali Linux Tools
- Linux
- Malware
- New Post
- Password Attacks
- PCI
- Pentesting Tools
- Phishing
- Post Exploitation
- Security Hacker
- Sniffing/Spoofing
- software
- Stress Testing
- TECH
- Tech today
- Tutorials
- VPN
- Vulnerability Analysis
- Web Application Analysis
- Wi-Fi
- Wi-Fi
- Windows
- Wireless Attacks
- YECH
goLAPS : The Ultimate Guide To Managing LAPS Passwords with Golang
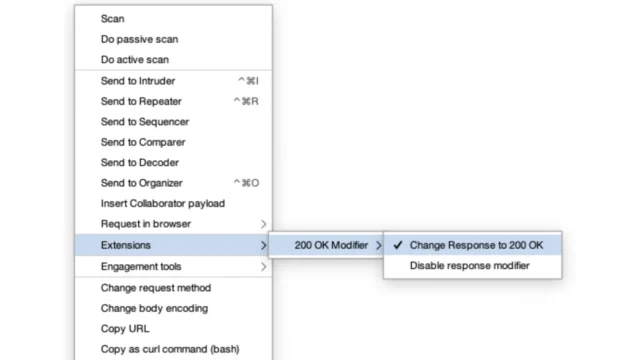
200-OK-Modifier : Mastering Web Application Analysis And Penetration Testing
NullGate : Advancing Evasion Techniques In Windows Exploitation
WebHunt : A Dive Into Web App Testing For Bug Bounty Hunting
Process Ghosting In Rust : Crafting Evasive Applications On Windows
WINDOWS PHONE
Sh00t : A Testing Environment for Manual Security Testers
LATEST ARTICLES
goLAPS : The Ultimate Guide To Managing LAPS Passwords with Golang
goLAPS is a tool designed to interact with the Local Administrator Password Solution (LAPS) in a domain environment. It allows users to retrieve and set LAPS passwords for domain-joined computers using simple binding over LDAP and LDAPS protocols. This project was inspired by pyLAPS and serves as a learning exercise in Golang. Capabilities Of goLAPS Retrieve LAPS Passwords: goLAPS can fetch...
200-OK-Modifier : Mastering Web Application Analysis And Penetration Testing
The 200-OK-Modifier is a versatile Burp extension that allows users to modify server response codes in real-time, specifically changing them to "200 OK." This capability is particularly useful in web application testing and penetration testing scenarios where manipulating server responses can help identify vulnerabilities or simulate specific conditions. Functionality The primary function of the 200-OK-Modifier is to intercept and alter HTTP...
NullGate : Advancing Evasion Techniques In Windows Exploitation
NullGate is a sophisticated project designed to leverage NTAPI functions using indirect syscalls, incorporating the FreshyCalls method with a novel approach to dynamic syscall number retrieval. It also employs a unique technique to bypass Windows Defender's memory scanning, making it a powerful tool for process injection. Key Features Of NullGate Indirect Syscalls: NullGate uses indirect syscalls to invoke NTAPI functions, providing...
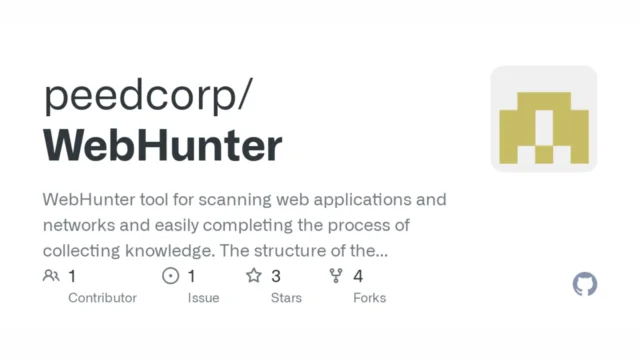
WebHunt : A Dive Into Web App Testing For Bug Bounty Hunting
WebHunt is an innovative project that focuses on web application testing, particularly for bug bounty hunting. It leverages powerful tools like Burp Suite to identify vulnerabilities in web applications. Here's a closer look at how WebHunt functions and the tools it utilizes. Introduction To WebHunt WebHunt is not to be confused with WebHunt.io, a B2B growth agency specializing in AI-driven lead...
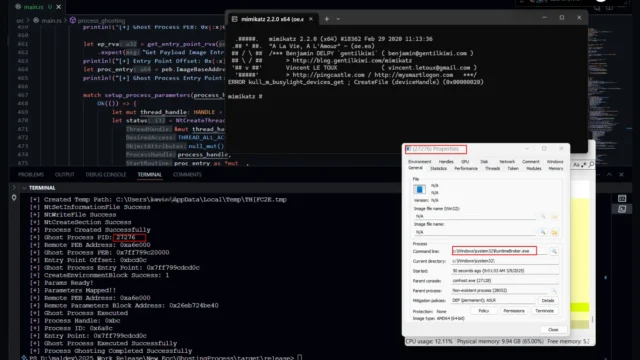
Process Ghosting In Rust : Crafting Evasive Applications On Windows
Process ghosting is a sophisticated technique used to evade detection by security tools on Windows systems. It involves creating a temporary file, marking it for deletion, and then executing its contents from memory without leaving a persistent file on disk. This method allows malicious code to run undetected, as traditional security software often relies on scanning files on disk. How...
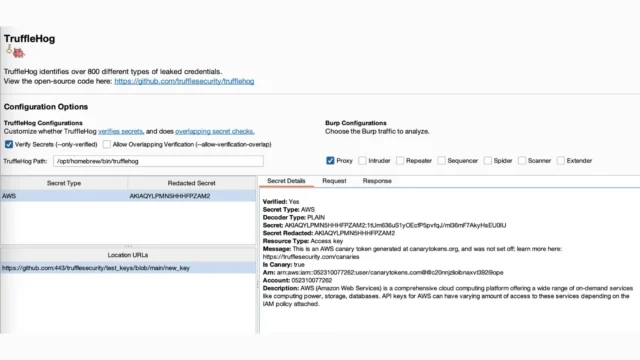
TruffleHog Burp Suite Extension : Enhancing Security With Automated Secret Detection
The TruffleHog Burp Suite Extension is a powerful tool designed to scan HTTP traffic within Burp Suite for over 800 types of secrets, including API keys, passwords, and SSH keys. This extension leverages the capabilities of TruffleHog, a widely recognized tool for detecting sensitive information in code and data streams. Key Features Automatic Secret Detection: The extension runs TruffleHog every 10...
ps5Spoofer : Unlocking PS4 Game Compatibility On Your PS5
The ps5Spoofer is a tool designed for the PlayStation 5 (PS5) that patches the PS4 SDK to version 99.9. This modification prevents the console from prompting for a system update when installing and running PS4 games on the PS5. The spoofer is particularly useful for users who want to play PS4 games without updating their PS5 firmware, ensuring compatibility...
eWPTX Preparion : Essential Tools And Functions
The eWPTX (eLearnSecurity Web Application Penetration Tester Extreme) certification is a challenging credential that validates an individual's advanced skills in web application penetration testing. To prepare effectively for this exam, it's crucial to understand and utilize the right tools and techniques. Here's a detailed overview of key tools and their functions in the context of eWPTX preparation: 1. Burp Suite Function:...
REC2 : Rusty External Command And Control Tool
REC2, short for Rusty External Command and Control, is a sophisticated Command and Control (C2) framework developed in the Rust programming language. Designed for advanced operational use, REC2 enables remote management of implants (clients) across macOS, Linux, and Windows platforms. This tool leverages external APIs like VirusTotal and Mastodon to transmit encrypted communications, ensuring stealth and anonymity during operations. Key...
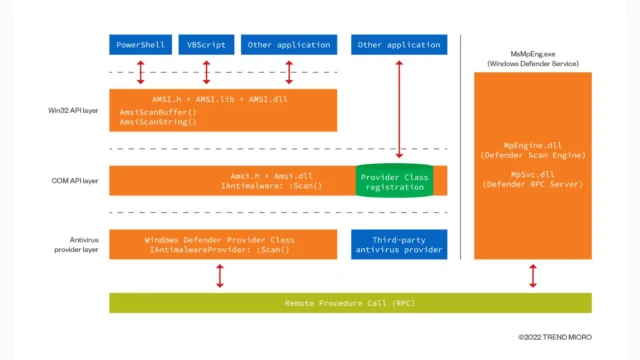
AMSI-Bypass-HWBP : A Tool For Evading AMSI Detection
AMSI (Antimalware Scan Interface) is a Windows feature designed to help protect systems from malware by scanning scripts and files for malicious content. However, attackers often seek to bypass AMSI to execute malicious scripts undetected. One such tool for bypassing AMSI is AMSI-Bypass-HWBP, which utilizes a small debugger to manipulate the behavior of AMSI. Functionality Of AMSI-Bypass-HWBP AMSI-Bypass-HWBP operates by creating...