Vulnerability Analysis
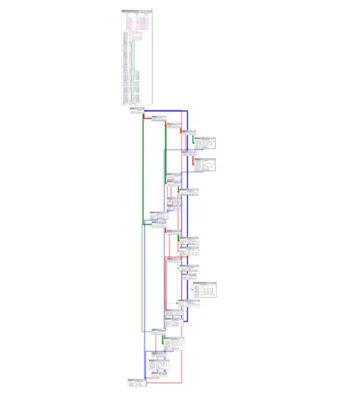
Vulnerability analysis is a critical step in strengthening cybersecurity and protecting digital assets. This category covers the latest tools, techniques, and best practices for identifying security weaknesses in networks, applications, servers, and databases. From automated vulnerability scanners to manual penetration testing frameworks, we explore resources that help organizations detect, assess, and remediate potential threats before attackers can exploit them.
Whether you’re an IT professional, security researcher, or business owner, our guides and reviews provide actionable insights into vulnerability assessment, risk prioritization, and compliance requirements. Stay ahead of cyber risks with trusted vulnerability analysis tools that improve resilience, safeguard sensitive data, and ensure regulatory compliance.