Havoc : Modern and malleable post-exploitation command and control framework
Havoc is a modern and malleable post-exploitation command and control framework, created by @C5pider. ⚠️Havoc is in an early state of release. Breaking changes may be made to APIs/core structures as the framework matures. Support Consider supporting C5pider on Patreon/Github Sponsors. Additional features are planned for supporters in the future, such as custom agents/plugins/commands/etc. Quick Start Please see the Wiki for complete documentation. Havoc works...
OFRAK : Unpack, Modify, And Repack Binaries
OFRAK (Open Firmware Reverse Analysis Konsole) is a binary analysis and modification platform. OFRAK combines the ability to: Identify and Unpack many binary formats Analyze unpacked binaries with field-tested reverse engineering tools Modify and Repack binaries with powerful patching strategies OFRAK supports a range of embedded firmware file formats beyond userspace executables, including: Compressed filesystems Compressed & checksummed firmware Bootloaders RTOS/OS kernels OFRAK equips users with: A Graphical User...
Autobloody : Tool To Automatically Exploit Active Directory Privilege Escalation Paths Shown By BloodHound
Autobloody is a tool to automatically exploit Active Directory privilege escalation paths shown by BloodHound. Description This tool automates the AD privesc between two AD objects, the source (the one we own) and the target (the one we want) if a privesc path exists in BloodHound database. The automation is composed of two steps: Finding the optimal path for privesc using bloodhound...
S3Crets Scanner : Hunting For Secrets Uploaded To Public S3 Buckets
S3cret Scanner tool designed to provide a complementary layer for the Amazon S3 Security Best Practices by proactively hunting secrets in public S3 buckets. Can be executed as scheduled task or On-Demand. Automation Workflow The automation will perform the following actions: List the public buckets in the account (Set with ACL of Public or objects can be public)List the textual or sensitive files...
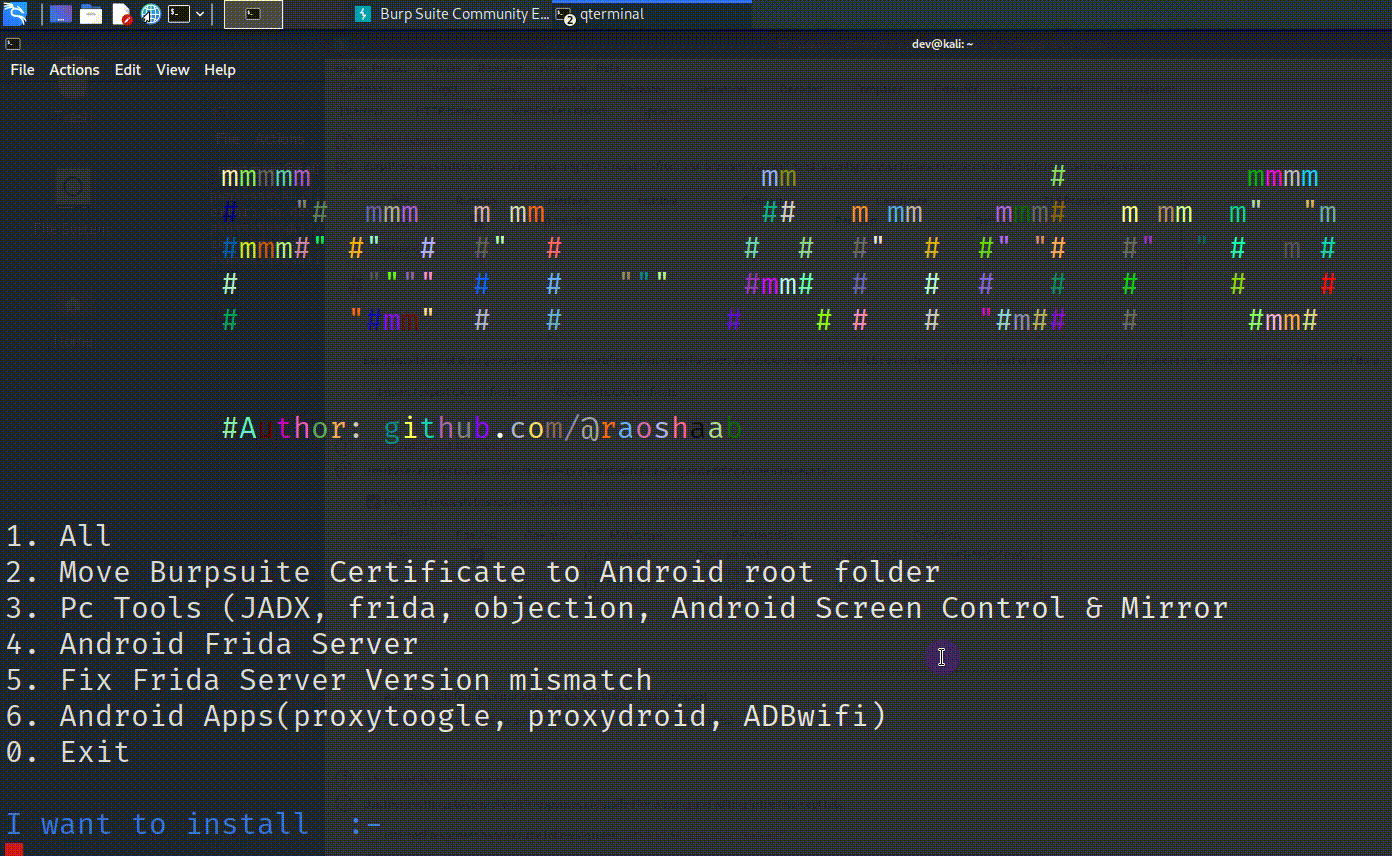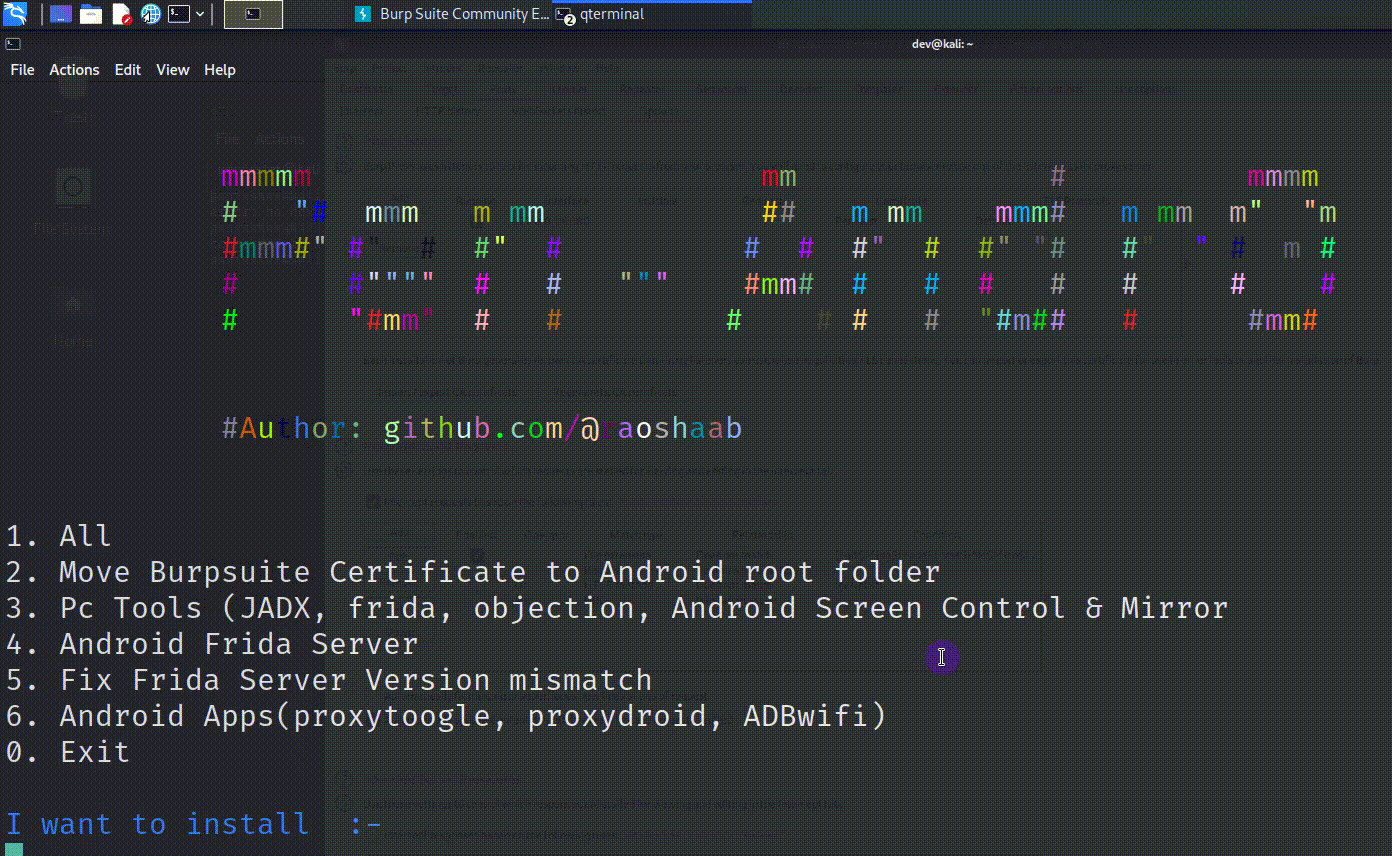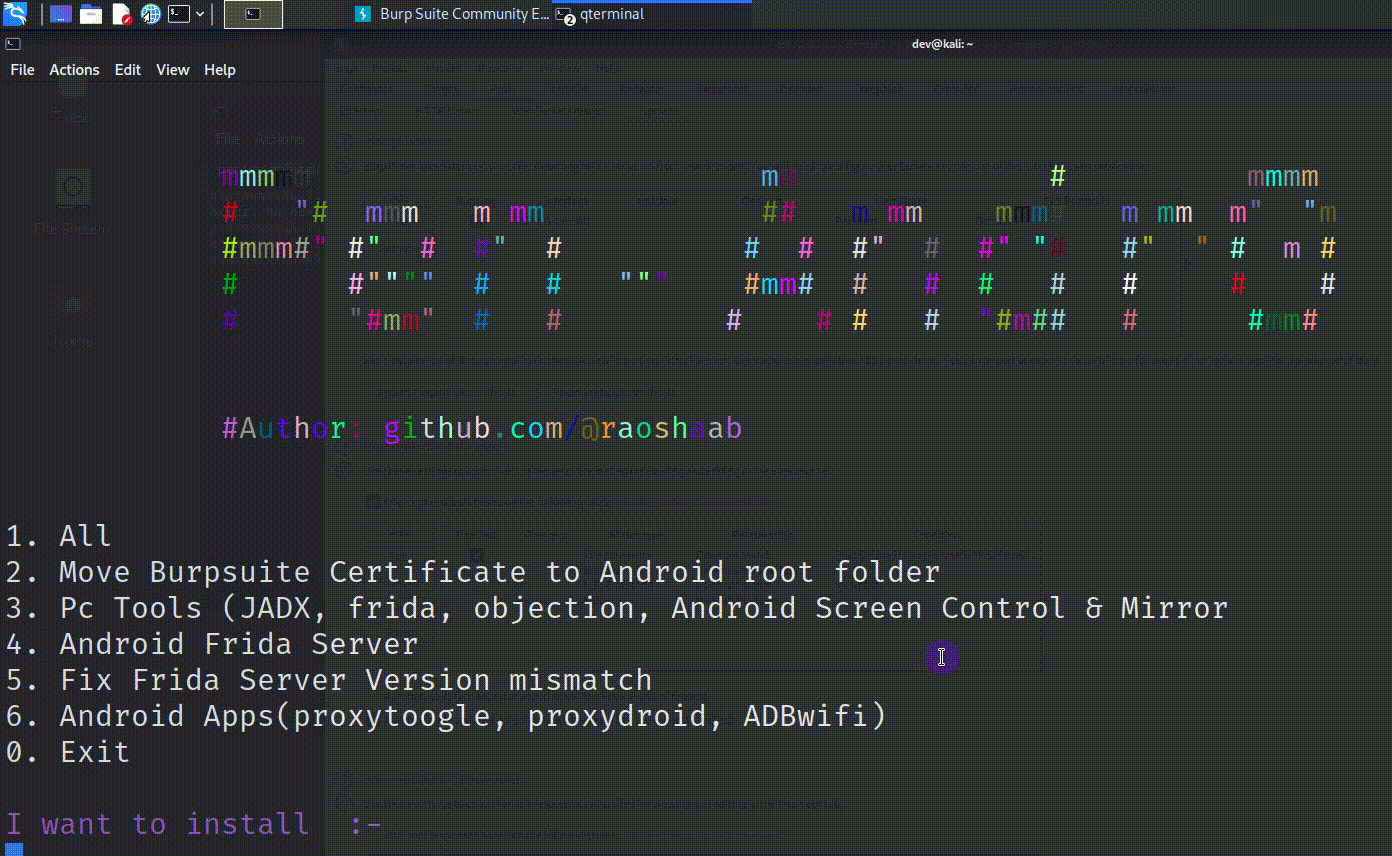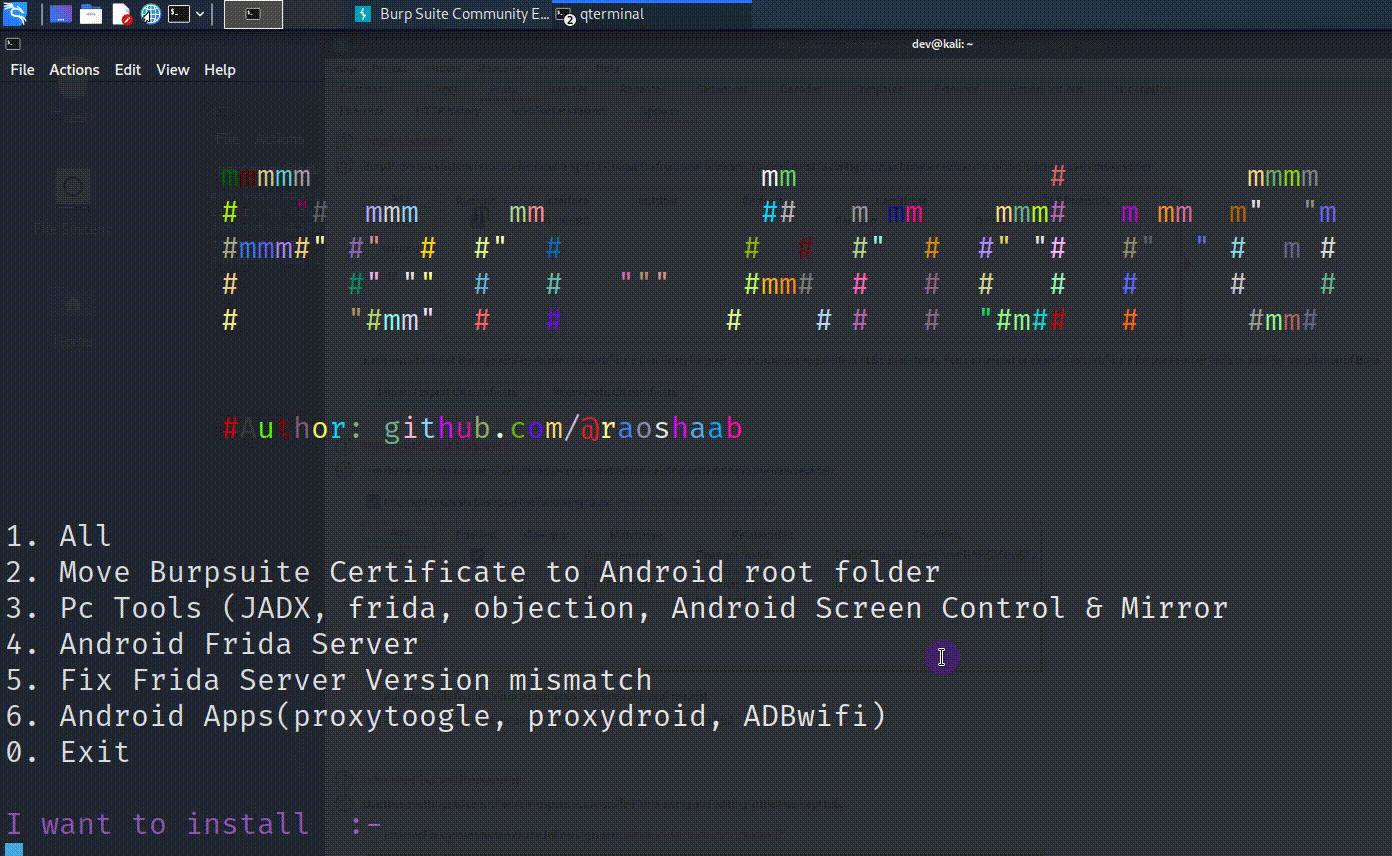
Pen Andro – An Automated Android Penetration Testing Tool
Introduction Pen-Andro Script will automate the process of installing all necessary tools & tasks for Android Pentesting i.e Moving Burpsuite Certificate,Installing Adb frida server, APKs like proxy toggle, proxydroid, adbwifi. Usage Open Terminal Run below command curl -sL https://tinyurl.com/pen-Android | sudo bash Preconditions Burpsuite proxy Running at 127.0.0.1:8080 Rooted Android device connected via adb (Only one device should be connected) Magisk App (It will make installation easy...
ZPhisher : Automated Phishing Tool For Pentesters
Zphisher is an upgraded form of Shellphish. The main source code is from Shellphish. But I have not fully copied it. I have upgraded it & cleared the Unnecessary Files. It has 37 Phishing Page Templates ; including Facebook , Twitter & Paypal. It also has 4 Port Forwarding Tools . Installation apt updateapt install git php openssh...
The Hackingsage/Hacktronian – A Pentesting Tool for Linux and Android
Hacktronian is a free and open-source tool used for information gathering. It is used for performing numerous data hacking and penetration testing on websites and web applications. Hacktronian has different modules such as information gathering, and password attacks. Hacktronian is a complete package of different hacking tools/modules such as Setoolkit, Nmap, Host To IP Conversion, WAScan module, CMS Scanner module, and...
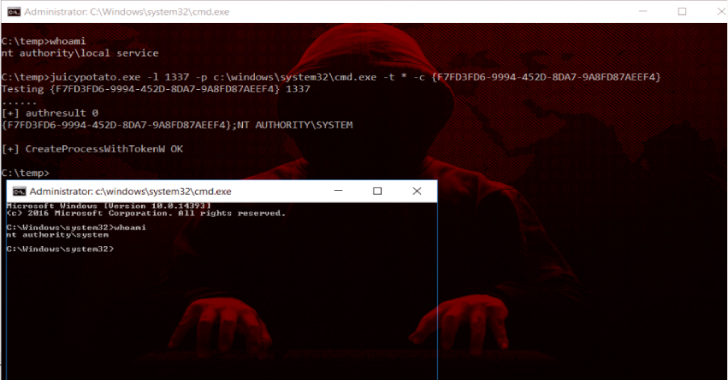
Juicy Potato : A Sugared Version Of RottenPotatoNG, With A Bit Of Juice
Juicy Potato is a sugared version of RottenPotatoNG, with a bit of juice, i.e. another Local Privilege Escalation tool, from a Windows Service Accounts to NT AUTHORITYSYSTEM. Summary RottenPotatoNG and its variants leverages the privilege escalation chain based on BITS service having the MiTM listener on 127.0.0.1:6666 and when you have SeImpersonate or SeAssignPrimaryToken privileges. During a Windows build review we found a setup where BITS was intentionally disabled and port 6666 was taken. We decided to weaponize RottenPotatoNG: Say hello to...
NetLlix : Tool To Emulate & Test Exfiltration Of Data Over Different Network Protocols
NetLlix is a project created with an aim to emulate and test exfiltration of data over different network protocols. The emulation is performed w/o the usage of native API's. This will help blue teams write correlation rules to detect any type of C2 communication or data exfiltration. Currently, this project can help generate HTTP/HTTPS traffic (both GET and POST) using...
Squarephish : OAuth Device Code Authentication Flow & QR codes
SquarePhish is an advanced phishing tool that uses a technique combining the OAuth Device code authentication flow and QR codes. See PhishInSuits for more details on using OAuth Device Code flow for phishing attacks. _____ ...










.png)
.png)
.png)
.png)


.png)
.png)
.webp)