Chrome Browser Exploitation, Part 1 : Introduction To V8 And JavaScript Internals
The blog post "Chrome Browser Exploitation, Part 1: Introduction to V8 and JavaScript Internals" provides foundational insights into browser internals and tools critical for analyzing JavaScript engine behavior. Below is a detailed overview of key tools and their functions in V8 research: 1. Debugging Tools (d8 and %DebugPrint) The d8 developer shell is V8’s debugging interface, enabling researchers to execute JavaScript...
Chrome Browser Exploitation, Part 3: Analyzing and Exploiting CVE-2018-17463
The exploitation of CVE-2018-17463, a type confusion vulnerability in Chrome’s V8 JavaScript engine, relies on a suite of specialized tools to analyze and weaponize the flaw. This vulnerability stemmed from improper side-effect modeling in TurboFan’s JSCreateObject operation, allowing attackers to corrupt memory via redundancy elimination during JIT compilation. Below are key tools and techniques used in its exploitation: 1. d8...
Full Spectrum Event Tracing For Windows Detection In The kernel Against Rootkits
Sanctum EDR demonstrates a multi-layered approach to detecting and preventing Event Tracing for Windows (ETW) tampering by rootkits, combining kernel-mode monitoring with user-space protections. This toolkit focuses on neutralizing advanced techniques used by malware like Remcos RAT and Lazarus Group's FudModule rootkit to blind security solutions. Key Functions Kernel Dispatch Table MonitoringSanctum's driver periodically validates the integrity of the ETW Kernel...
SpyAI : Intelligent Malware With Advanced Capabilities
SpyAI is a sophisticated form of malware that leverages advanced technologies to capture and analyze screenshots from entire monitors. It utilizes Slack as a trusted channel to exfiltrate these screenshots to a Command and Control (C2) server. The C2 server employs GPT-4 Vision, a cutting-edge AI model, to analyze the screenshots and construct detailed daily activity reports frame by...
Proxmark3 : The Ultimate Tool For RFID Security And Analysis
The Proxmark3 is a versatile, open-source tool designed for radio-frequency identification (RFID) security analysis, research, and development. Originally created by Jonathan Westhues in 2007, it has evolved into a powerful device capable of reading, writing, emulating, and analyzing various RFID protocols at both low (125 kHz, 134 kHz) and high frequencies (13.56 MHz). Key Functions RFID Tag Analysis: The Proxmark3 can...
Awesome Solana Security : Enhancing Program Development
The "Awesome Solana Security" collection is a comprehensive resource designed to help developers build more secure Solana programs. It provides a wide range of tools, documentation, and best practices to ensure robust security in the Solana ecosystem. Development Resources For developers transitioning from Ethereum to Solana, RareSkills' Solana course is highly recommended. The Solana handbook offers detailed insights into Solana's architecture...
IngressNightmare-POCs : Understanding The Vulnerability Exploitation Flow
The "IngressNightmare" vulnerabilities, disclosed in March 2025, represent a critical set of security issues affecting the NGINX Ingress Controller for Kubernetes. These vulnerabilities, including CVE-2025-24513, CVE-2025-24514, CVE-2025-1097, CVE-2025-1098, and CVE-2025-1974, pose significant risks to Kubernetes environments by enabling unauthenticated remote code execution (RCE) and potential cluster takeover. Overview Of IngressNightmare Vulnerabilities CVE-2025-24513: Auth secret file path traversal vulnerability (Medium). CVE-2025-24514: Configuration injection...
AdaptixC2 : Enhancing Penetration Testing With Advanced Framework Capabilities
AdaptixC2 is an advanced post-exploitation and adversarial emulation framework designed specifically for penetration testers. It offers a robust set of features that enhance the flexibility and effectiveness of security testing operations. The framework includes a server component written in Golang and a cross-platform GUI client developed using C++ QT, ensuring compatibility across Linux, Windows, and MacOS. Key Features Of AdaptixC2 Server/Client...
Bincrypter : Enhancing Linux Binary Security through Runtime Encryption And Obfuscation
Bincrypter is a powerful Linux binary runtime crypter written in BASH. It is designed to obfuscate and encrypt ELF binaries and #!-scripts, providing a robust layer of protection against reverse engineering and detection by antivirus and endpoint detection and response (EDR) systems. Key Features Of Bincrypter Obfuscation and Encryption: Bincrypter can encrypt and obfuscate any ELF binary or #!-script, making it...
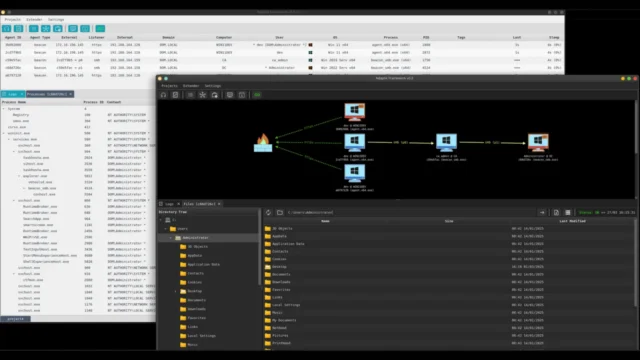
Endpoint With Missing Agents : Identifying And Managing Security Gaps
Endpoint security is crucial for protecting organizations from cyber threats. However, managing endpoint agents can be challenging, especially when devices are missing critical security software. This article explores how to identify and manage endpoints with missing agents using tools like Microsoft Defender for Endpoint and Intune. Challenges With Endpoint Agents Device Discovery and Agent Installation: Identifying which devices should have specific...