Atomic Red Team : Mastering Threat Simulations For Advanced Security Testing
The Atomic Red Team is an open-source framework designed to help security teams emulate adversarial tactics and techniques in alignment with the MITRE ATT&CK® framework. Developed by Red Canary, it provides a library of small, portable detection tests, known as "atomics," that can be executed to assess the effectiveness of security controls and incident response processes. Core Features And Functionality MITRE...
SCCMHunter : A Comprehensive Tool For SCCM Asset Exploitation
SCCMHunter is a Python-based post-exploitation tool designed for security professionals to identify, profile, and exploit System Center Configuration Manager (SCCM) assets within an Active Directory (AD) domain. Developed by Garrett Foster, it serves as a powerful resource for penetration testing and security assessments by uncovering vulnerabilities in SCCM environments. Core Functions Asset Discovery: SCCMHunter queries LDAP using its find module to locate...
eBPF File Creation Blocker : Enhancing Linux Security
The eBPF File Creation Blocker is a cutting-edge security module designed to prevent file creation in specified directories using the Eunomia eBPF Runtime. Leveraging the Linux Security Module (LSM) framework and eBPF technology, this tool offers an efficient and lightweight solution for enforcing directory-specific file creation policies. Key Features Directory Restriction: Blocks file creation attempts specifically within the /etc/test/ directory. Efficient Enforcement:...
DeepSeek-Vulnerability-Analyzer : Enhancing Burp Suite With AI-Powered Analysis
The DeepSeek-Vulnerability-Analyzer is an innovative extension for Burp Suite that leverages AI-driven capabilities to enhance vulnerability detection and analysis. By integrating the DeepSeek API, this tool allows security researchers to identify vulnerabilities such as XSS and SQL injection with greater precision and efficiency. Key Features And Setup Instructions Custom Payload Integration: Create two files, xss.txt and sqli.txt, in the plugin's directory. Store your...
NFCToolsGUI : A Comprehensive NFC Management Tool
NFCToolsGUI is a versatile, cross-platform program designed to interact with PN532 NFC modules, supporting Windows, Linux, and macOS. It simplifies NFC tag management and offers a wide range of functionalities for developers, researchers, and hobbyists. Key Features NFCToolsGUI provides robust features for NFC tag operations: Crack Card Using MFOC: Perform Mifare Classic card cracking. Write and Format Cards: Easily write data or format...
GraphRunner : The Dual-Use Toolset For Microsoft 365 Security
GraphRunner is a powerful post-exploitation toolset designed for interacting with the Microsoft Graph API, enabling red teams and attackers to perform reconnaissance, persistence, and data exfiltration from Microsoft Entra ID (Azure AD) accounts. Developed by Beau Bullock and Steve Borosh of Black Hills Information Security, GraphRunner provides a streamlined approach to exploiting vulnerabilities within Microsoft 365 environments. Key Components GraphRunner is...
NailaoLoader : Hiding Execution Flow via Patching
NailaoLoader employs sophisticated techniques to obscure its execution flow, leveraging Windows Management Instrumentation (WMI) for lateral movement and file transfer. Threat actors use WMI to deploy three files—usysdiag.exe, sensapi.dll, and usysdiag.exe.dat—to targeted machines. The process begins with the execution of usysdiag.exe, a legitimate signed executable by Huorong Internet Security. Execution Flow DLL Side-Loading:The legitimate usysdiag.exe calls LoadLibraryA() to load sensapi.dll. However,...
CVE-2025-21333-POC : An In-Depth Exploration Of Windows Kernel Exploitation Techniques
The CVE-2025-21333 Proof of Concept (PoC) demonstrates an exploit targeting a vulnerability in the vkrnlintvsp.sys driver on Windows systems. This article delves into the tools, techniques, and functionality of the PoC, providing insights into its operation and limitations. Overview Of CVE-2025-21333 CVE-2025-21333 is a kernel vulnerability actively exploited by threat actors. It allows attackers to achieve arbitrary read/write capabilities in the...
Powershell Digital Forensics And Incident Response
PowerShell has emerged as a vital tool in Digital Forensics and Incident Response (DFIR), offering robust capabilities for automating data collection, analysis, and containment during cybersecurity incidents. The PowerShell DFIR-Script.ps1 repository exemplifies how PowerShell can streamline forensic investigations on Windows systems. Key Features Of DFIR-Script.ps1 The DFIR-Script.ps1 is a PowerShell-based script designed to collect forensic artifacts from compromised Windows devices. It...
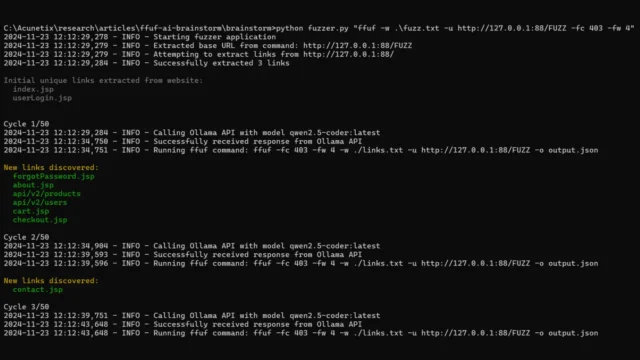
Brainstorm : Revolutionizing Web Fuzzing With Local LLMs
Brainstorm is an innovative web fuzzing tool that integrates traditional fuzzing techniques with AI-powered insights, leveraging local Large Language Models (LLMs) via Ollama to optimize the discovery of hidden directories, files, and endpoints in web applications. By combining the speed and efficiency of tools like ffuf with the intelligence of LLMs, Brainstorm significantly enhances the fuzzing process, uncovering more...