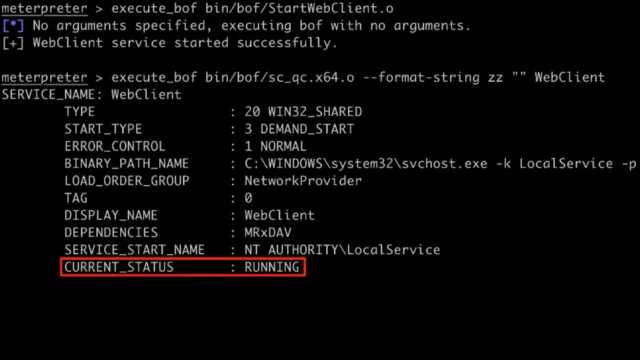
Vulnerability Research : Harnessing Tools Like Metasploit To Uncover And Mitigate Security Weaknesses
Vulnerability research is a critical aspect of cybersecurity that focuses on identifying, analyzing, and documenting security weaknesses in software, hardware, and networks. This process often involves specialized tools and frameworks that aid researchers in discovering vulnerabilities and developing exploits to demonstrate the risks. Below, we explore the role of tools in vulnerability research, with a focus on Metasploit. Metasploit Framework:...
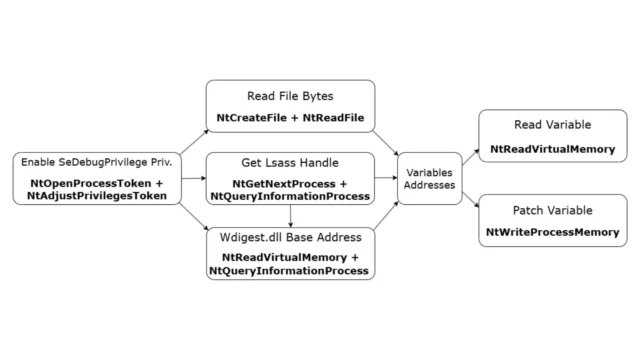
NativeBypassCredGuard : Bypassing Credential Guard With NTAPI Functions
NativeBypassCredGuard is a specialized tool designed to bypass Microsoft's Credential Guard, a security feature that protects sensitive credentials like NTLM password hashes and Kerberos tickets using virtualization-based security (VBS). This tool achieves its objective by patching the WDigest.dll file to enable plaintext credential storage in memory, allowing attackers to retrieve cleartext passwords from the LSASS process memory dump. How NativeBypassCredGuard...
PyClassInformer : An Advanced RTTI Parsing Plugin For IDA Pro
PyClassInformer is an IDAPython-based plugin designed for parsing Run-Time Type Information (RTTI) in C++ binaries. While existing tools like Class Informer and SusanRTTI offer similar functionality, PyClassInformer stands out by addressing limitations such as the inability to use these tools as libraries and the lack of advanced class hierarchy management. Key Features Cross-Platform Compatibility: PyClassInformer supports Windows, macOS, and Linux, as...
NSSM : Essential Guide To Non-Sucking Service Manager For Windows Services
The Non-Sucking Service Manager (NSSM) is a lightweight, open-source utility designed to simplify the management of Windows services. It allows users to run any executable, script, or command as a Windows service, ensuring that the application remains active and restarts automatically in case of crashes or reboots. Below is an overview of its functionality and usage. Key Features Service Creation: NSSM...
PS5 UMTX Jailbreak : Comprehensive Guide And Analysis
The PS5 UMTX Jailbreak is a webkit-based kernel exploit developed by SpecterDev and other contributors, designed to unlock specific features of the PlayStation 5. This tool primarily targets firmware versions up to 5.50, with earlier versions (1.xx and 2.xx) being more stable. Here’s an overview of its functionality and features: Key Features Of PS5 UMTX Jailbreak Kernel Exploit: The jailbreak leverages...
Spice86 – A PC Emulator For Real Mode Reverse Engineering
Spice86 is an advanced PC emulator designed for reverse engineering and rewriting real-mode DOS programs, especially when the source code is unavailable. Built on .NET 8, it is compatible with Windows, macOS, and Linux, offering a robust platform for developers and researchers to dissect and reimplement legacy software. Below is an overview of its primary functions and capabilities. Key Features...
NewMachineAccount : Streamlining Active Directory Machine Account Creation For Penetration Testing
NewMachineAccount.exe is a lightweight, standalone executable designed for creating machine accounts in Active Directory (AD) domains. This tool is particularly useful for system administrators and penetration testers who need to automate the creation of machine accounts with custom configurations, including passwords and organizational units (OUs). Developed by @decoder_it, it provides a command-line interface for seamless integration into scripts and...
Ransomware Tool Matrix : The Arsenal Of Cyber Defense
The Ransomware Tool Matrix is a valuable repository designed to catalog tools commonly used by ransomware gangs and extortionist groups. By leveraging this resource, cybersecurity defenders can gain critical insights into the tactics, techniques, and procedures (TTPs) employed by adversaries, enabling proactive threat hunting, detection, and mitigation strategies. Key Features Of The Ransomware Tool Matrix Tool Categorization: The matrix classifies tools into...
RustDesk : A Comprehensive Remote Desktop Solution
RustDesk is an open-source remote desktop software built using the Rust programming language. It offers a secure, efficient, and feature-rich alternative to proprietary tools like TeamViewer and AnyDesk. Designed for individuals and organizations, RustDesk emphasizes privacy and performance while providing seamless cross-platform support. Key Features Cross-Platform CompatibilityRustDesk supports Windows, macOS, Linux, iOS, and Android, enabling users to connect and control devices...
CrimsonEDR : A Cutting-Edge Tool For Simulating And Bypassing EDR Systems
CrimsonEDR is an open-source tool developed by Matthias Ossard, designed to simulate the behavior of Endpoint Detection and Response (EDR) systems. It provides a platform for identifying malware patterns and understanding evasion techniques, making it valuable for cybersecurity professionals seeking to enhance their skills in bypassing EDR mechanisms. Key Features CrimsonEDR employs a variety of detection methods to identify malware activities: Direct...