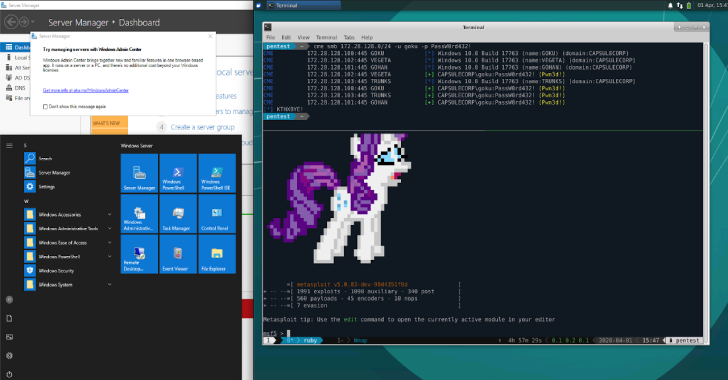
Capsulecorp Pentest : Vagrant VirtualBox Environment For Conducting An Internal Network Penetration Test
The Capsulecorp Pentest is a small virtual network managed by vagrant and ansible. It contains five virtual machines, including one Linux attacking system running xubuntu and 4 Windows 2019 servers configured with various vulnerable services. This project can be used to learn network penetration testing as a stand-alone environment but is ultimatly designed to compliment my book The Art...
Santa : A Binary Whitelisting/Blacklisting System For macOS
Santa is a binary authorization system for macOS. It consists of a kernel extension (or a system extension on macOS 10.15+) that monitors for executions, a userland daemon that makes execution decisions based on the contents of a SQLite database, a GUI agent that notifies the user in case of a block decision and a command-line utility for managing...
Applications You Can Build with Free APIs
With free APIs, developers can practice programming by using those APIs to create applications. Once you have practiced writing apps, you can then move on to paying for some APIs that you can use to write even more useful or complex apps. Phone Number Validator There is a multitude of free APIs that are available to the public. So, your options...
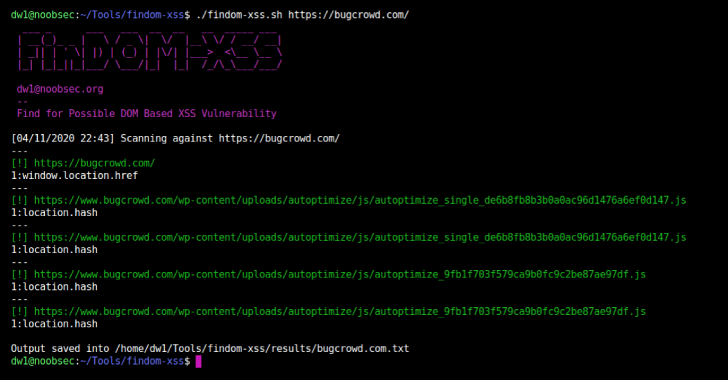
FinDOM-XSS : A Fast DOM Based XSS Vulnerability Scanner With Simplicity
FinDOM-XSS is a tool that allows you to finding for possible and/ potential DOM based XSS vulnerability in a fast manner. Installation $ git clone https://github.com/dwisiswant0/findom-xss.git Dependencies: LinkFinder Configuration Change the value of LINKFINDER variable (on line 3) with your main LinkFinder file. Usage To run the tool on a target, just use the following command. $ ./findom-xss.sh https://target.host/about-us.html This will run the tool against target.host. URLs...
ParamSpider : Mining Parameters From Dark Corners Of Web Archives
ParamSpider is a mining parameters from dark corners of web archives. Features Finds parameters from web archives of the entered domain.Finds parameters from subdomains as well.Gives support to exclude urls with specific extensions.Saves the output result in a nice and clean manner.It mines the parameters from web archives (without interacting with the target host) Usage Note : Use python 3.7+ $ git clone https://github.com/devanshbatham/ParamSpider$...
GIVINGSTORM : Infection Vector That Bypasses AV, IDS, & IPS
GIVINGSTORM is a breeze to use. Simply clone the directory, and cd into it. The beginnings of a C2 framework. Currently without all the C2 stuff so far. Generates a dual stage VBS infection vector, and a dual stage HTA infection vector. The variables take into account C2 addresses, Koadic/Empire payloads, and a few delivery mechanisms. The payload files...
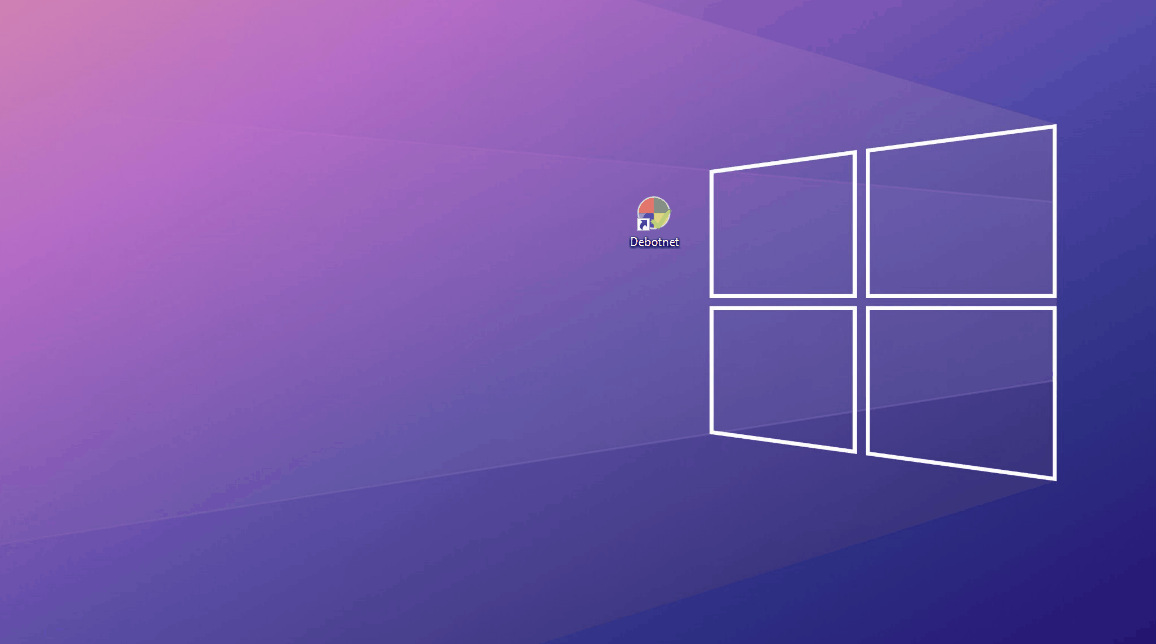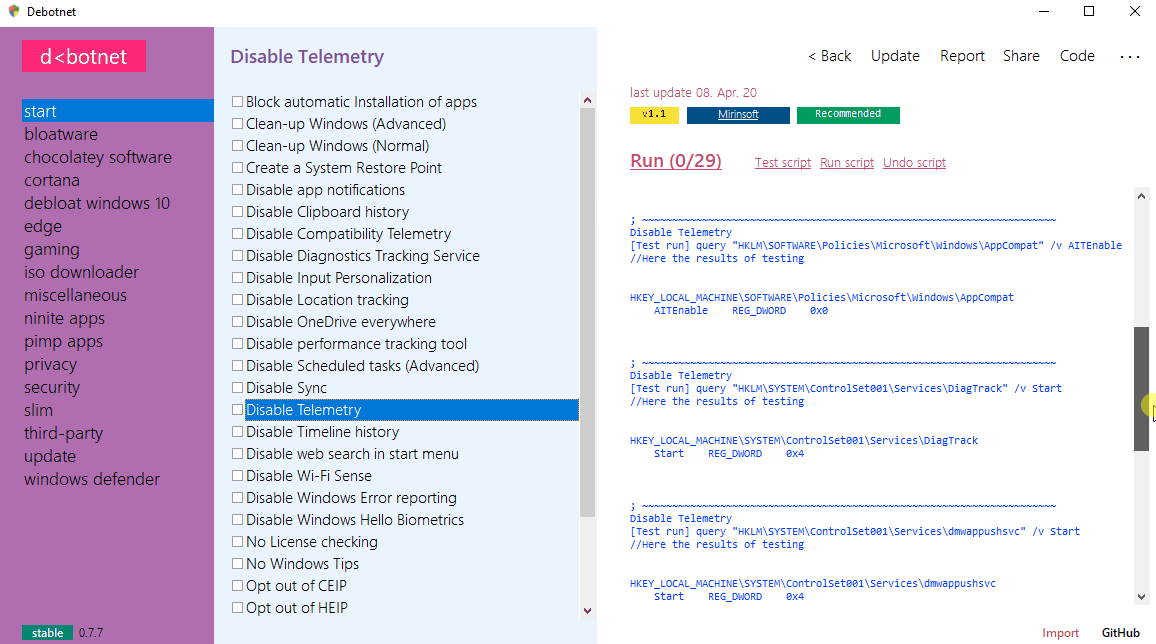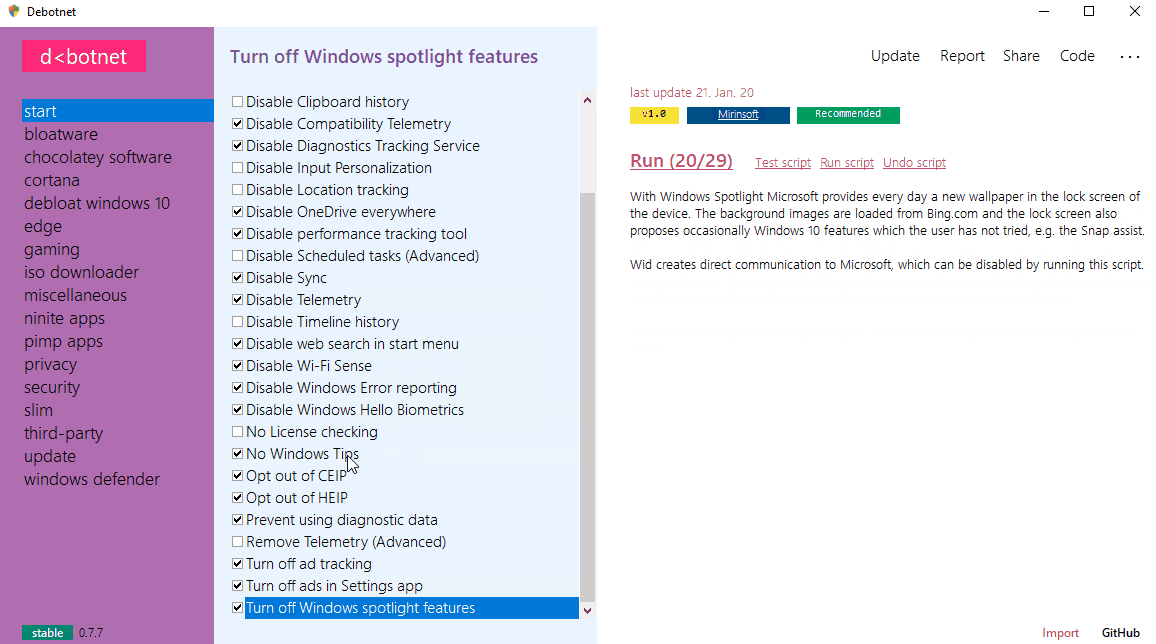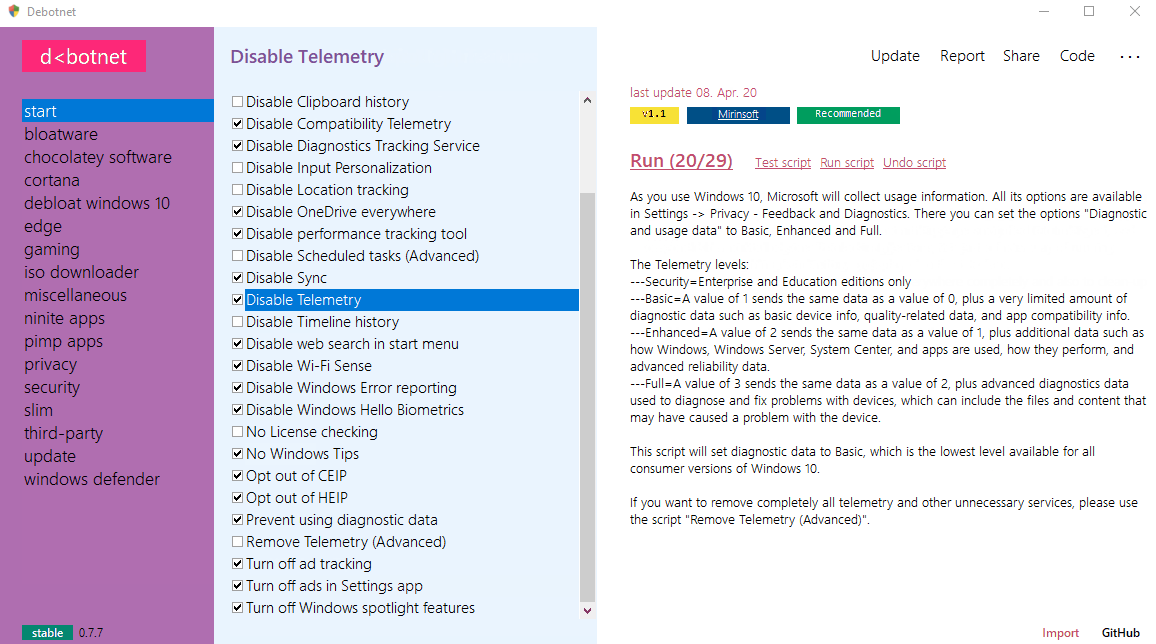
Debotnet : Tool For Controlling Windows 10’s Privacy-Related Settings
Debotnet is a free and portable tool for controlling Windows 10's many privacy-related settings and keep your personal data private. Your preparation for the Net! The Windows 10 default privacy settings leave a lot to be desired when it comes to protecting you and your private information. Whenever I set up a new computer or update a current setup for my...
OWASP Threat Dragon Desktop
Threat Dragon is a free, open-source, cross-platform threat modeling application including system diagramming and a rule engine to auto-generate threats/mitigations. It is an OWASP Incubator Project. The focus of the project is on great UX, a powerful rule engine and integration with other development lifecycle tools. There is a good overview of threat modeling and risk assessment from OWASP, and...
Cloudtopolis : Cracking Hashes In The Cloud For Free
Cloudtopolis is a tool that facilitates the installation and provisioning of Hashtopolis on the Google Cloud Shell platform, quickly and completely unattended (and also, free!). Requirements Have 1 Google account (at least). Installation Cloudtopolis installation is carried out in two phases: Phase 1 Access Google Cloud Shell from the following link: https://ssh.cloud.google.com/cloudshell/editor?hl=es&fromcloudshell=true&shellonly=true Then, run the following commands inside this terminal: wget https://raw.githubusercontent.com/JoelGMSec/Cloudtopolis/master/Cloudtopolis.sh chmod +x Cloudtopolis.sh ./Cloudtopolis.sh Phase 2 Access...
Colabcat – Running Hashcat On Google Colab With Session Backup And Restore
Colabcat is a tool used to run hashcat on Google colab with session backup and restore. Usage Go to the link below to open a copy of the colabcat.ipynb file in Google Colab: https://colab.research.google.com/github/someshkar/colabcat/blob/master/colabcat.ipynbClick on Runtime, Change runtime type, and set Hardware accelerator to GPU.Go to your Google Drive and create a directory called dothashcat, with a hashes subdirectory where you...