Relocatable : A Tool For Position Independent Code
Relocatable is an innovative tool designed to simplify the creation of Position Independent Code (PIC) in C. This tool enables developers to write C code that is directly compiled into raw shellcode, which can be loaded into any process without requiring external utilities like Donut or sRDI. The result is lightweight, efficient shellcode with minimal overhead and straightforward functionality. To...
Understanding Vulnerability And Its Tools In Cybersecurity
In cybersecurity, a vulnerability refers to a flaw or weakness in a system, application, or network that attackers can exploit to gain unauthorized access or cause harm. These vulnerabilities can stem from coding errors, unpatched software, misconfigurations, or even human errors. Identifying and addressing vulnerabilities is critical to maintaining robust security. Types Of Vulnerabilities Software Vulnerabilities: Issues in code, such as...
BOF WinRM Client : Advancing Stealth And Efficiency In Remote System Management
The BOF WinRM Client is a Beacon Object File (BOF) extension for Cobalt Strike that provides a lightweight and stealthy way to interact with the Windows Remote Management (WinRM) service. This tool enables operators to execute commands on remote systems using WinRM without creating persistent sessions or relying on external tools like PowerShell, which can trigger security alerts. Key Features...
Dioxus : Revolutionizing Cross-Platform Development With Rust
Dioxus is a cutting-edge framework for building cross-platform applications using the Rust programming language. It enables developers to create apps for web, desktop, mobile, and server environments with a single codebase. By leveraging Rust's performance and safety, Dioxus provides a robust foundation for modern application development. Core Features Of Dioxus Cross-Platform Development: Dioxus supports multiple platforms such as web (via WebAssembly),...
Modrinth : A Comprehensive Overview Of Tools And Functions
Modrinth is a cutting-edge platform designed to revolutionize the world of Minecraft modding. Focused primarily on Minecraft: Java Edition, it provides a centralized hub for players, developers, and creators to share, discover, and manage mods, plugins, data packs, shaders, and more. With its user-friendly interface and open-source philosophy, Modrinth has quickly become a favorite among the gaming community. The Modrinth...
Deno : The Next Generation JavaScript Runtime For Modern Web Development
Deno is a modern runtime for JavaScript, TypeScript, and WebAssembly, designed to address some of the limitations of Node.js. Created by Ryan Dahl, the original developer of Node.js, Deno emphasizes security, simplicity, and developer productivity. Key Features Of Deno Secure by Default: Deno adopts a sandboxed environment where access to the file system, network, or environment variables is denied unless explicitly...
Exploring Content-Type Research : XSS, CSRF, And WAF Bypass Techniques
The Content-Type header in HTTP requests plays a critical role in web application security. It specifies the format of the data being sent, but improper handling or parsing of this header can expose applications to vulnerabilities such as Cross-Site Scripting (XSS), Cross-Site Request Forgery (CSRF), and Web Application Firewall (WAF) bypasses. Below, we explore these issues in detail. XSS And...
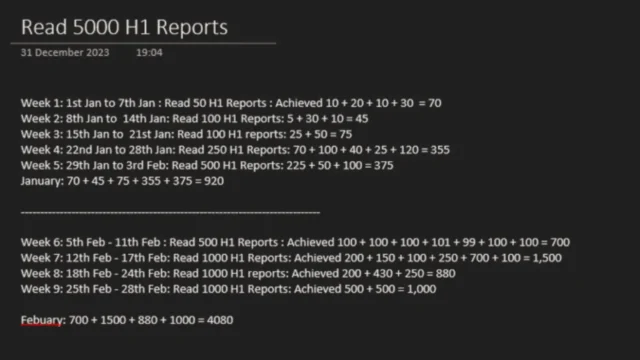
10000 H1 Disclosed Reports : Comprehensive Insights From A 5000-Report Analysis
The journey of reading 10,000 disclosed HackerOne (H1) reports offers valuable insights into the bug bounty ecosystem, emphasizing the importance of analyzing real-world vulnerabilities. This ambitious project was undertaken to deeply understand the types of bugs being reported, accepted, or rejected, and to refine strategies for bug bounty hunting. Here’s a breakdown of how this goal was approached and...
Understanding And Utilizing The Tomcat – CVE-2024-50379 Proof-of-Concept (PoC)
The Tomcat-CVE-2024-50379-PoC is a proof-of-concept tool designed to demonstrate the exploitation of a critical vulnerability in Apache Tomcat, identified as CVE-2024-50379. This vulnerability, with a CVSS score of 9.8, arises from a Time-of-check Time-of-use (TOCTOU) race condition during JavaServer Pages (JSP) compilation. Under specific configurations, this flaw can lead to Remote Code Execution (RCE), posing significant risks to systems...
Monorepos : Benefits, Challenges, And Essential Tools For Scalable Development
A monorepo (short for monolithic repository) is a version control strategy where all projects, libraries, and tools are stored in a single repository. This approach enables streamlined collaboration, code sharing, and efficient dependency management across multiple applications. Below is an overview of tools and their functions within the context of a monorepo. Core Functions Of Monorepo Tools Code Sharing and Reusability:Monorepos...