APPLICATIONS
HOT NEWS
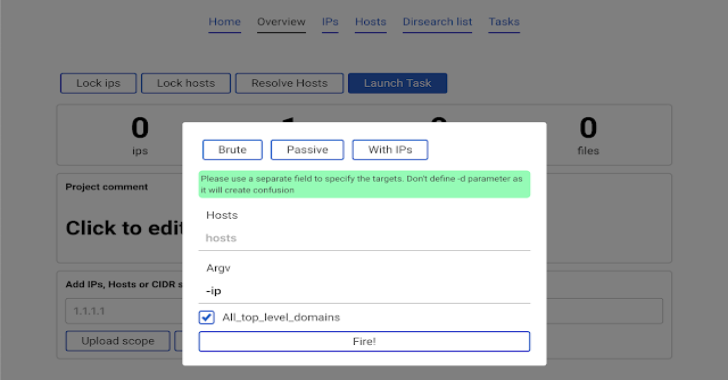
Project Black : BugBounty Progress Control With Scanning Modules
Project Black is a scope control, scope scanner and progress tracker for easier working on a bug bounty or pentest project. The tools encourages...
© kalilinuxtutorials.com 2025










.webp)




.webp)


.webp)