APPLICATIONS
HOT NEWS
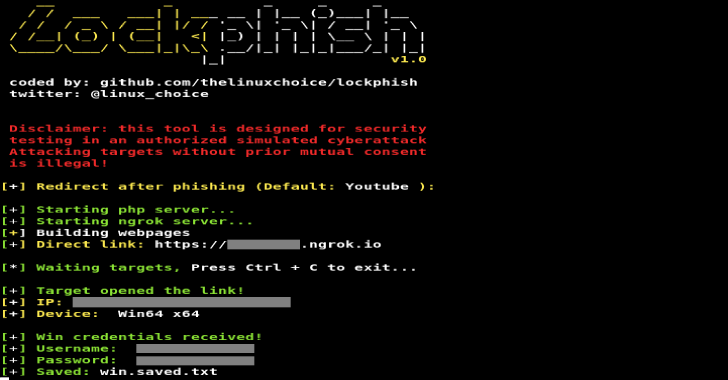
Lockphish : A Tool For Phishing Attacks On The Lock Screen
Lockphish it's the first tool (05/13/2020) for phishing attacks on the lock screen, designed to grab Windows credentials, Android PIN and iPhone Passcode using...
© kalilinuxtutorials.com 2025