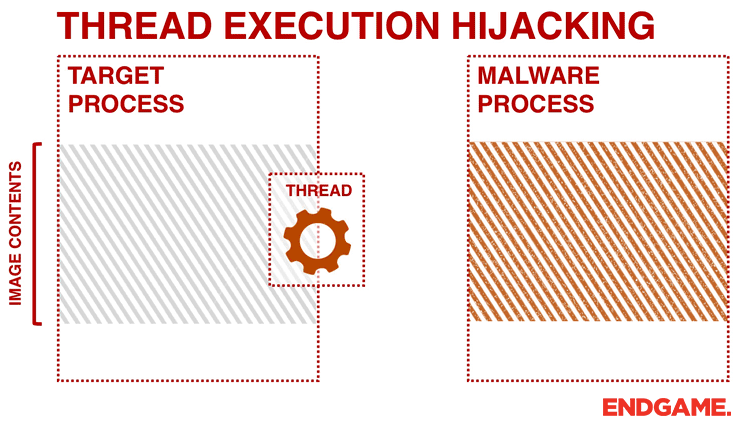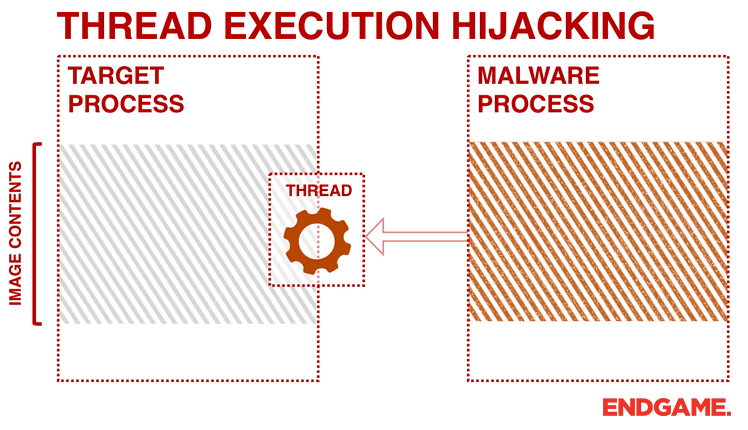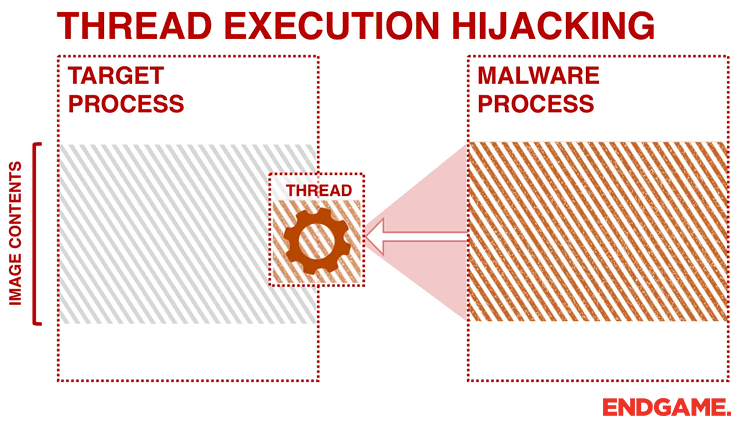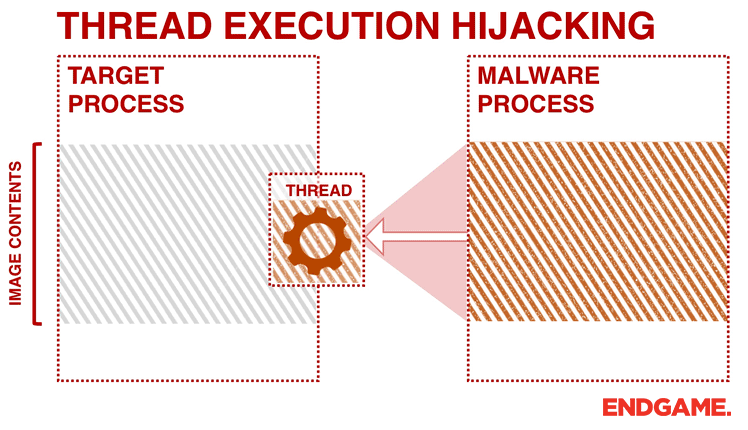
APPLICATIONS
HOT NEWS
5 Best Online Cyber Security Courses
Over the years, technology has advanced and evolved, with more enterprises moving to online platforms. However, with this evolution, the rate of cybercrimes has...
We provide you with the latest Kali Linux & Penetration testing tools.
Contact us: admin@kalilinuxtutorials.com
© @Kali Linux Tutorials - 2024

.webp)








.webp)


.webp)
.png)

.png)