Trivy is a Simple and Comprehensive Vulnerability Scanner for Containers, Suitable for CI. A software vulnerability is a glitch, flaw, or weakness present in the software or in an Operating System.
It detects vulnerabilities of OS packages (Alpine, RHEL, CentOS, etc.) and application dependencies (Bundler, Composer, npm, yarn etc.).
It is easy to use. Just install the binary and you’re ready to scan. All you need to do for scanning is to specify an image name of the container.
Features
- Detect comprehensive vulnerabilities
- OS packages (Alpine, Red Hat Universal Base Image, Red Hat Enterprise Linux, CentOS, Debian, Ubuntu, Amazon Linux and Distroless)
- Application dependencies (Bundler, Composer, Pipenv, Poetry, npm, yarn and Cargo)
- Simple
- Specify only an image name
- See Quick Start and Examples
- Easy installation
apt-get install,yum installandbrew installis possible (See Installation)- No pre-requisites such as installation of DB, libraries, etc. (The exception is that you need
rpminstalled to scan images based on RHEL/CentOS. This is automatically included if you use our installers or the tool container image. See Vulnerability Detection for background information.)
- High accuracy
- Especially Alpine Linux and RHEL/CentOS
- Other OSes are also high
- DevSecOps
- Suitable for CI such as Travis CI, CircleCI, Jenkins, etc.
- See CI Example
Also Read – Uptux : Linux Privilege Escalation Checks
Installation
RHEL/CentOS
Add repository setting to /etc/yum.repos.d.
$ sudo vim /etc/yum.repos.d/trivy.repo
[trivy]
name=Trivy repository
baseurl=https://aquasecurity.github.io/trivy-repo/rpm/releases/$releasever/$basearch/
gpgcheck=0
enabled=1
$ sudo yum -y update
$ sudo yum -y install trivy
or
$ rpm -ivh https://github.com/aquasecurity/trivy/releases/download/v0.1.6/trivy_0.1.6_Linux-64bit.rpm
Debian/Ubuntu
Add repository to /etc/apt/sources.list.d.
$ sudo apt-get install wget apt-transport-https gnupg lsb-release
$ wget -qO – https://aquasecurity.github.io/trivy-repo/deb/public.key | sudo apt-key add –
$ echo deb https://aquasecurity.github.io/trivy-repo/deb $(lsb_release -sc) main | sudo tee -a /etc/apt/sources.list.d/trivy.list
$ sudo apt-get update
$ sudo apt-get install trivy
Or
$ sudo apt-get install rpm
$ wget https://github.com/aquasecurity/trivy/releases/download/v0.1.6/trivy_0.1.6_Linux-64bit.deb
$ sudo dpkg -i trivy_0.1.6_Linux-64bit.deb
Arch Linux
Package trivy-bin can be installed from the Arch User Repository. Examples:
pikaur -Sy trivy-bin
or
yay -Sy trivy-bin
Homebrew
You can use homebrew on macOS.
$ brew install aquasecurity/trivy/trivy
Binary (Including Windows)
Get the latest version from this page,
and download the archive file for your operating system/architecture.
Unpack the archive, and put the binary somewhere in your $PATH (on UNIX-y systems, /usr/local/bin or the like). Make sure it has execution bits turned on.
You also need to install rpm command for scanning images based on RHEL/CentOS.
From source
$ mkdir -p $GOPATH/src/github.com/aquasecurity
$ cd $GOPATH/src/github.com/aquasecurity
$ git clone https://github.com/aquasecurity/trivy
$ cd trivy/cmd/trivy/
$ export GO111MODULE=on
$ go install
You also need to install rpm command for scanning images based on RHEL/CentOS.
Quick Start
Simply specify an image name (and a tag). The latest tag should be avoided as problems occur with the image cache. See Clear image caches.
Basic
$ trivy [YOUR_IMAGE_NAME]
For example:
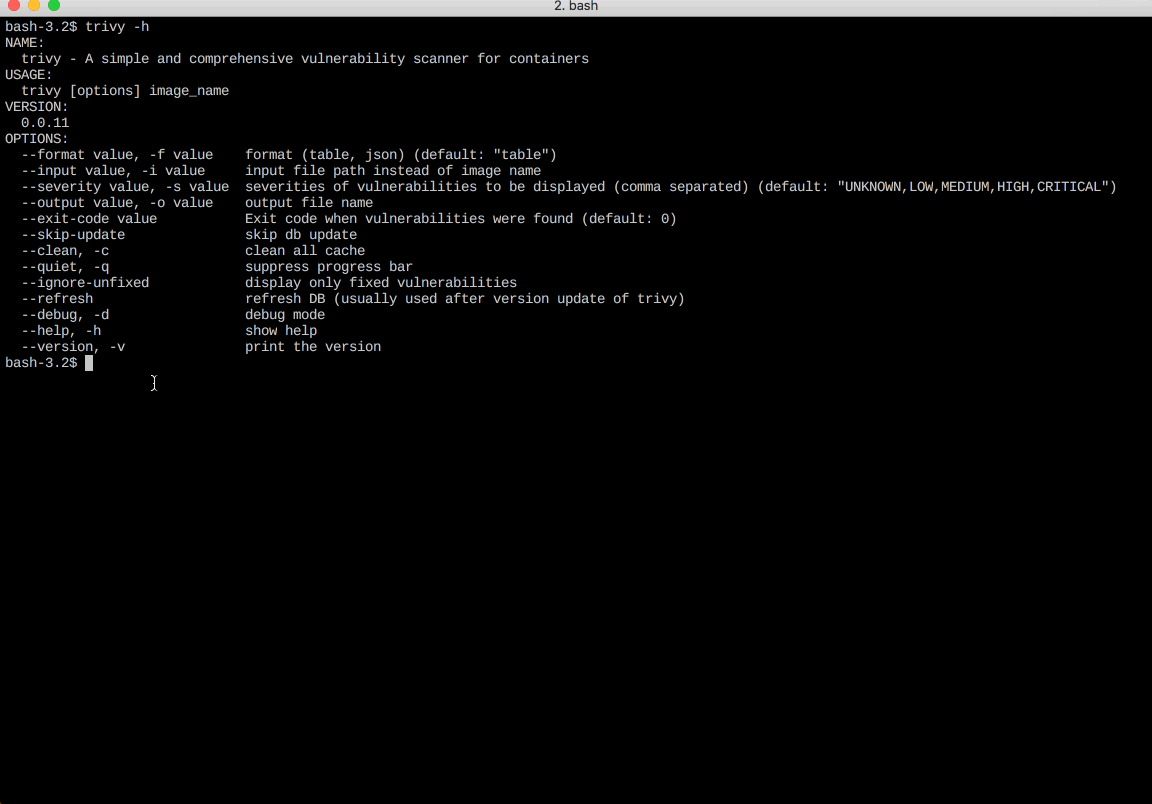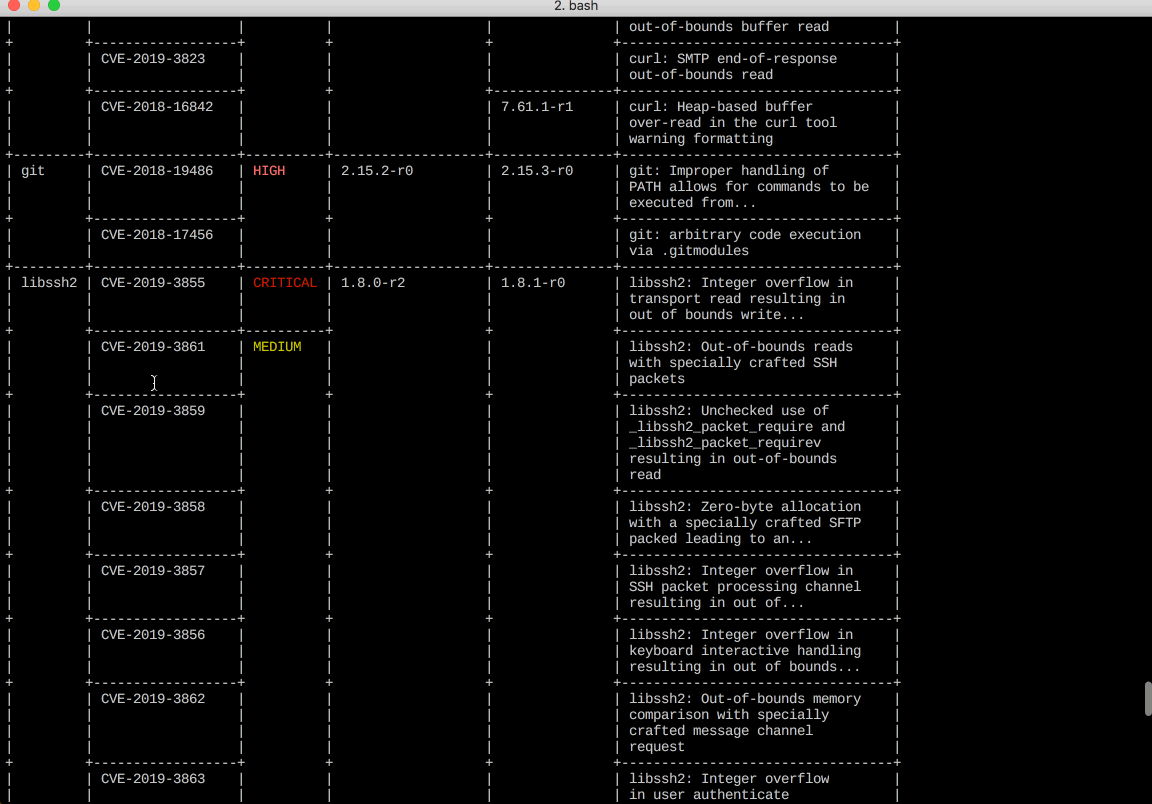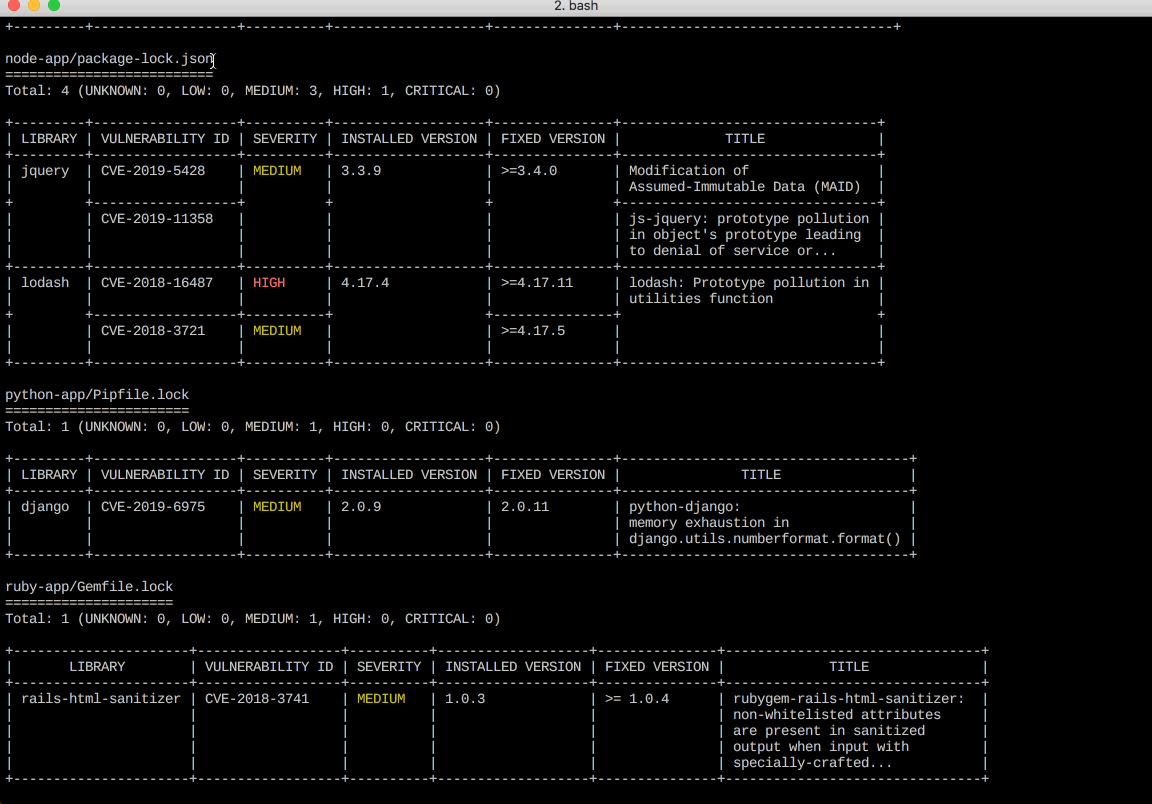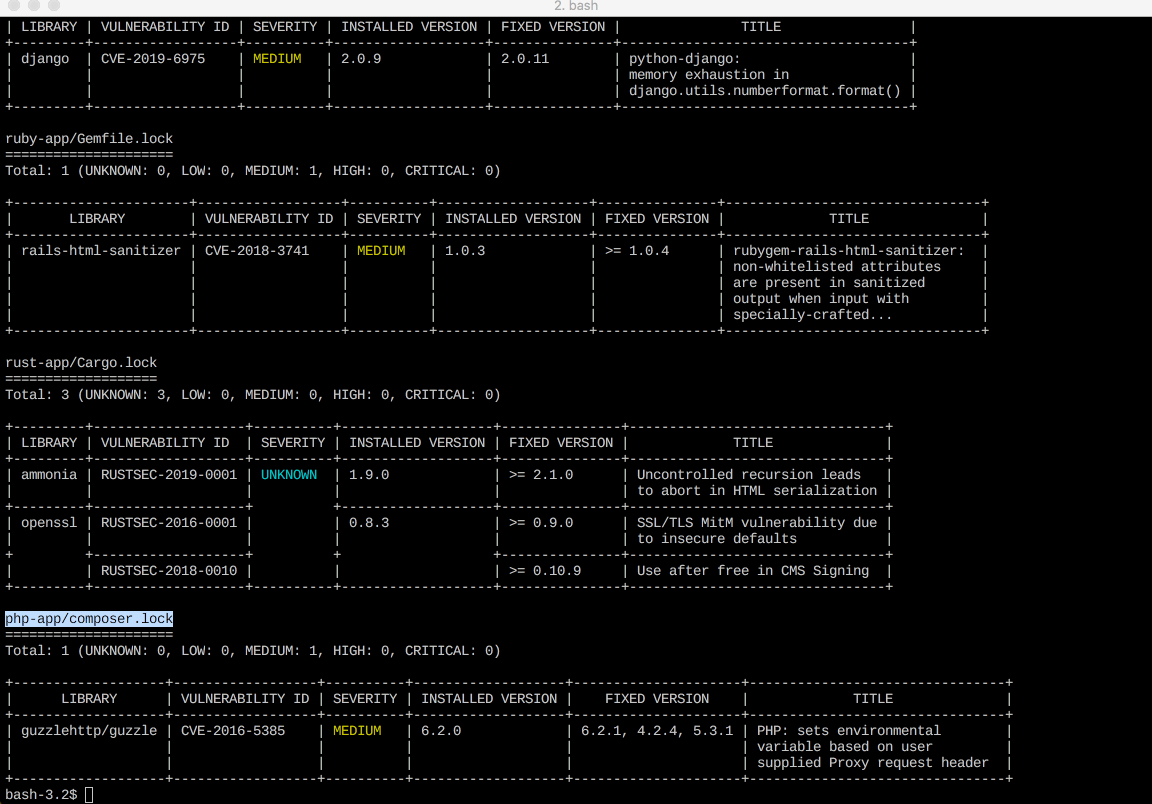
$ trivy python:3.4-alpine
Result
Docker
Replace [YOUR_CACHE_DIR] with the cache directory on your machine.
$ docker run –rm -v [YOUR_CACHE_DIR]:/root/.cache/ aquasec/trivy [YOUR_IMAGE_NAME]
Example for macOS:
$ docker run –rm -v $HOME/Library/Caches:/root/.cache/ aquasec/trivy python:3.4-alpine
If you would like to scan the image on your host machine, you need to mount docker.sock.
$ docker run –rm -v /var/run/docker.sock:/var/run/docker.sock \
-v $HOME/Library/Caches:/root/.cache/ aquasec/trivy python:3.4-alpine
Please re-pull latest aquasec/trivy if an error occurred. Result
Examples
Scan an image
Simply specify an image name (and a tag).
$ trivy knqyf263/vuln-image:1.2.3
Scan an image file
$ docker save ruby:2.3.0-alpine3.9 -o ruby-2.3.0.tar
$ trivy –input ruby-2.3.0.tar
Save the results as JSON
$ trivy -f json -o results.json golang:1.12-alpine
Filter the vulnerabilities by severities
$ trivy –severity HIGH,CRITICAL ruby:2.3.0
Filter the vulnerabilities by type
$ trivy –vuln-type os ruby:2.3.0
Available values:
- library
- os
Skip update of vulnerability DB
It always updates its vulnerability database when it starts operating. This is usually fast, as it is a difference update. But if you want to skip even that, use the --skip-update option.
$ trivy –skip-update python:3.4-alpine3.9
Update only specified distributions
By default, it always updates its vulnerability database for all distributions. Use the --only-update option if you want to name specified distributions to update.
$ trivy –only-update alpine,debian python:3.4-alpine3.9
$ trivy –only-update alpine python:3.4-alpine3.9
Only download vulnerability database
You can also ask it to simply retrieve the vulnerability database. This is useful to initialize workers in Continuous Integration systems. In the first run, the --only-update option is silently ignored.
$ trivy –download-db-only
$ trivy –download-db-only –only-update alpine
Ignore unfixed vulnerabilities
By default, it also detects unpatched/unfixed vulnerabilities. This means you can’t fix these vulnerabilities even if you update all packages. If you would like to ignore them, use the --ignore-unfixed option.
$ trivy –ignore-unfixed ruby:2.3.0
Specify exit code
By default, it exits with code 0 even when vulnerabilities are detected. Use the --exit-code option if you want to exit with a non-zero exit code.
$ trivy –exit-code 1 python:3.4-alpine3.9
This option is useful for CI/CD. In the following example, the test will fail only when a critical vulnerability is found.
$ trivy –exit-code 0 –severity MEDIUM,HIGH ruby:2.3.0
$ trivy –exit-code 1 –severity CRITICAL ruby:2.3.0
Ignore the specified vulnerabilities
Use .trivyignore.
$ cat .trivyignore
# Accept the risk
CVE-2018-14618
# No impact in our settings
CVE-2019-1543
$ trivy python:3.4-alpine3.9
Specify cache directory
$ trivy –cache-dir /tmp/trivy/ python:3.4-alpine3.9
Clear image caches
The --clear-cache option removes image caches. This option is useful if the image which has the same tag is updated (such as when using latest tag).
$ trivy –clear-cache python:3.7
Reset
The --reset option removes all caches and database. After this, it takes a long time as the vulnerability database needs to be rebuilt locally.
$ trivy –reset
Screenshot

















.png)

