Amazon Relational Database Service (RDS) for MySQL is a fully managed relational database service that provides cost-efficient and resizable capacity, while managing time-consuming database administration tasks. This service enables you to run a MySQL database in the cloud without the typical setup, provisioning, and on-going maintenance tasks.
By leveraging Amazon RDS for MySQL on AWS, users can spend more time focusing on their applications and business logic, rather than worrying about database management tasks such as backups, patch management, and failure detection. Amazon RDS for MySQL is a part of the larger Amazon Web Services (AWS) ecosystem, providing seamless integration with other AWS services and a vast array of options for designing and deploying your applications.
The use of Amazon RDS for MySQL extends beyond mere convenience. It also offers features such as automatic backups, software patching, automatic failover, and read replicas to enhance database performance and reliability. But as with any technology, it’s essential to understand and mitigate the potential security risks associated with its use.
MySQL on Amazon RDS: Security Challenges
Public Accessibility Risks
One of the first security considerations when deploying Amazon RDS for MySQL is to control public accessibility. By default, an Amazon RDS instance is not publicly accessible, which means it cannot be accessed from the internet or from outside of your VPC. However, there can be legitimate reasons to enable public accessibility, such as providing access to third-party vendors or enabling remote administration.
While public accessibility can provide flexibility, it also exposes your RDS instance to potential threats. Unauthorized users can potentially gain access to your data, perform malicious activities, or exploit vulnerabilities in your database. Therefore, it’s critical to implement proper security controls when enabling public accessibility.
IAM Role Misconfigurations
IAM (Identity and Access Management) is a crucial component of AWS, allowing you to manage access to AWS services and resources securely. While IAM offers powerful features, misconfigurations can lead to security issues. For instance, overly permissive policies can grant users more access than they need, potentially leading to privilege abuse.
Misconfigured IAM roles can also allow unauthorized access to your Amazon RDS for MySQL instances. For example, an IAM role with unnecessary RDS permissions can potentially enable an attacker to manipulate your database, delete data, or even take over the RDS instance.
SQL Injections and Application-Level Threats
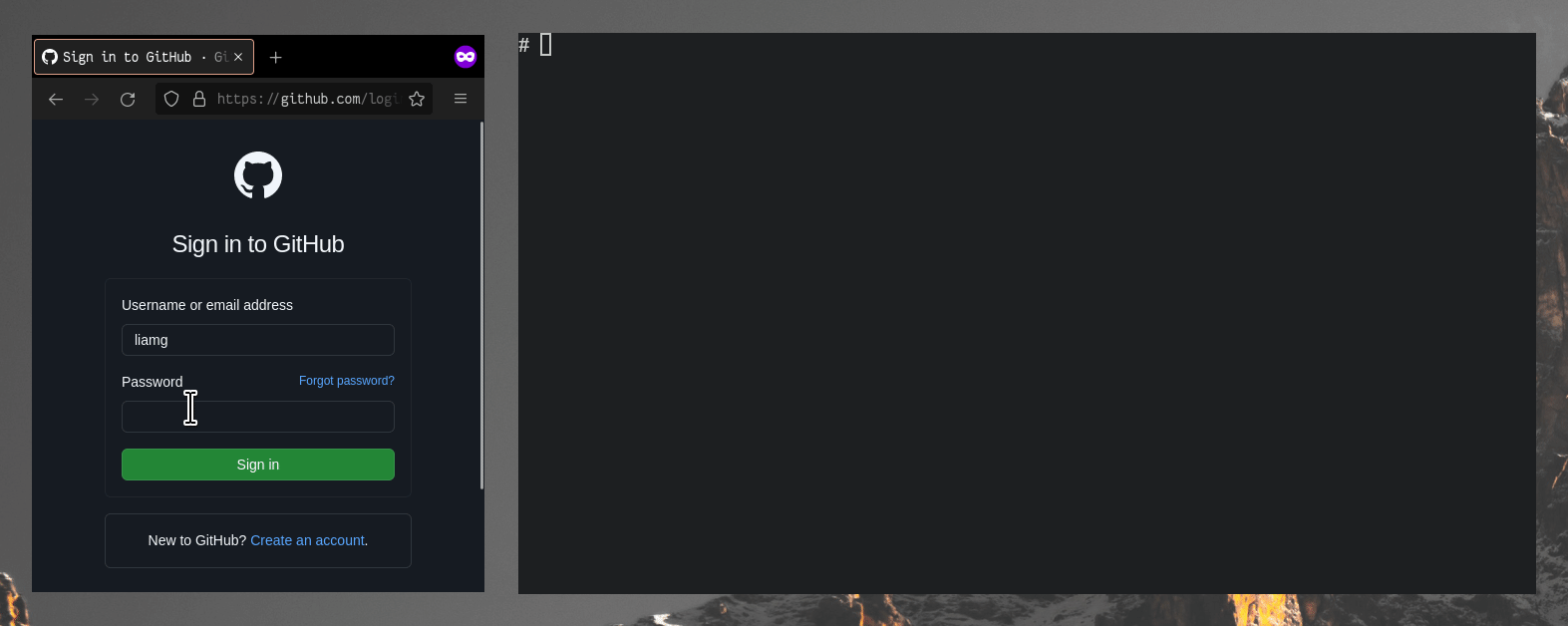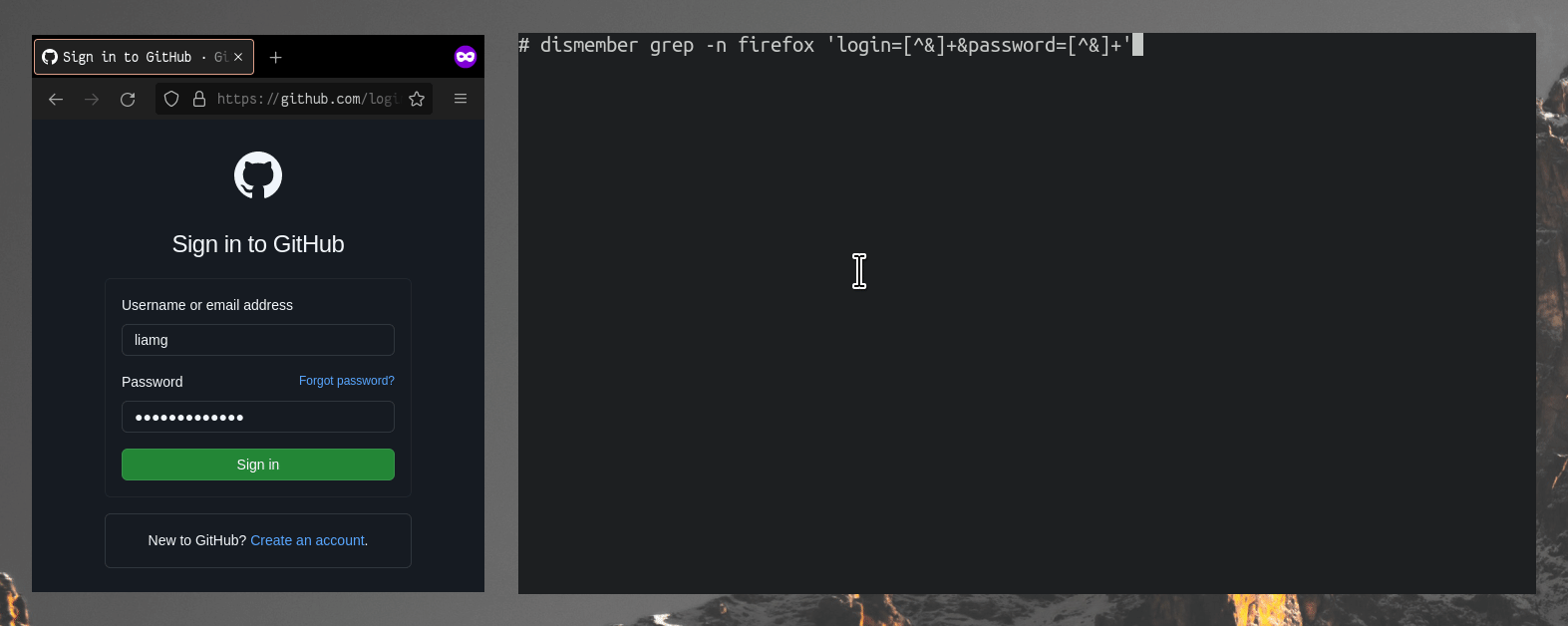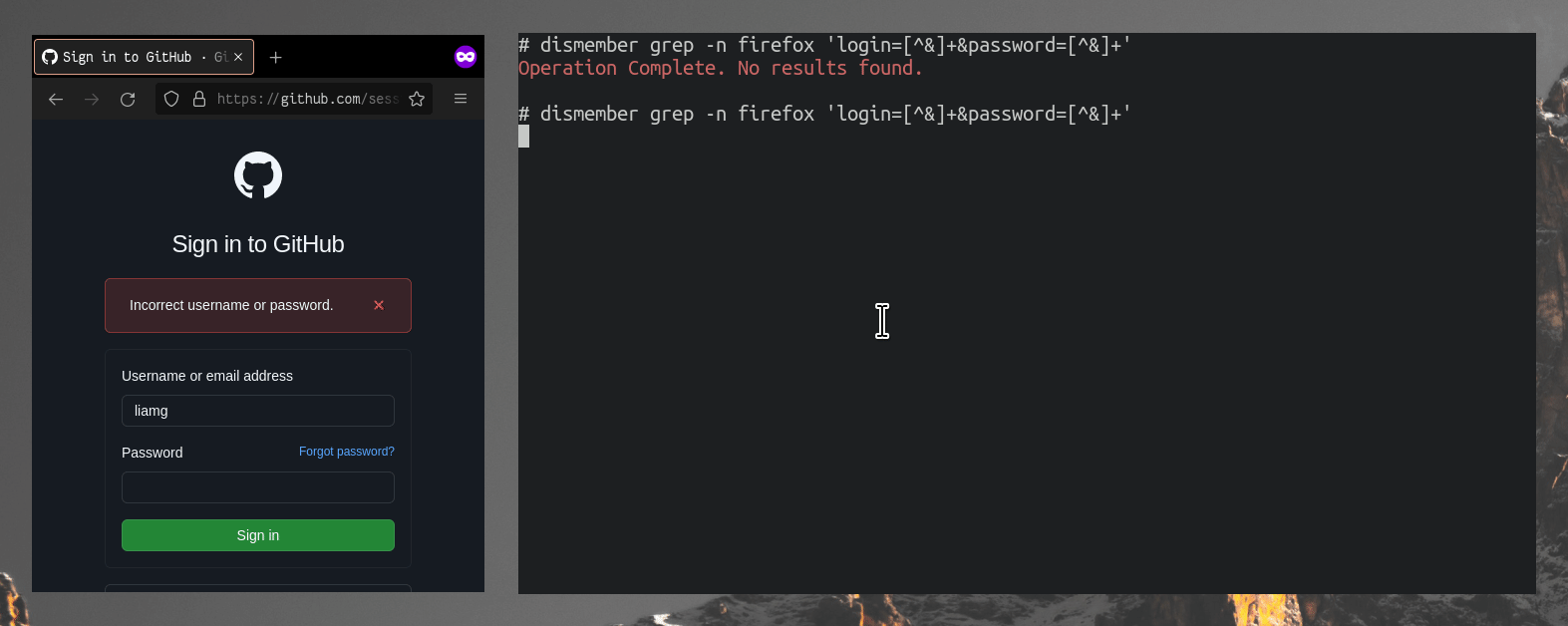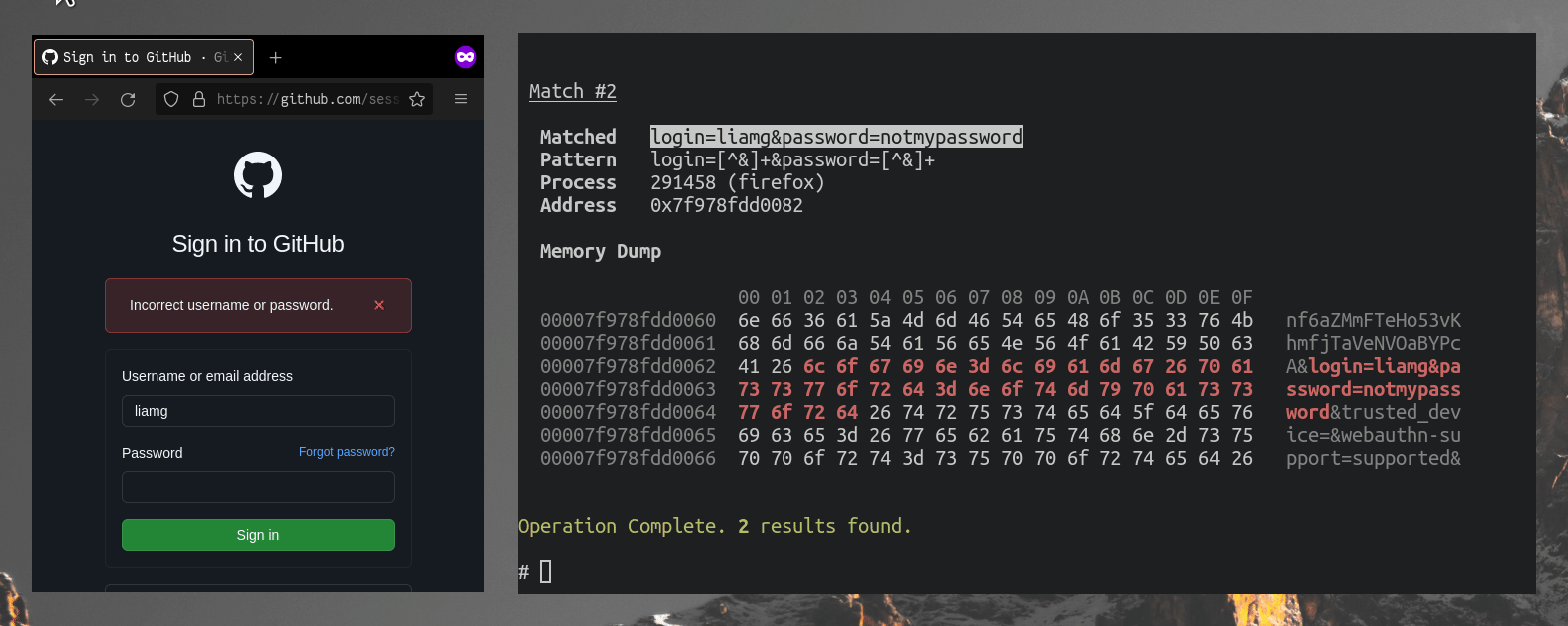
SQL injections are a common application-level threat where an attacker can inject malicious SQL code into your application, which can then manipulate your database. This threat can lead to data breaches, data corruption, and even complete system compromise. Despite being a well-known threat, SQL injections continue to plague many web applications due to poor coding practices or insufficient input validation.
Amazon RDS for MySQL, like any database service, is susceptible to SQL injections if not properly secured. Therefore, it’s essential to adopt secure coding practices, implement proper input validation, and use prepared statements or parameterized queries to mitigate this threat.
5 Tips for Securing MySQL on Amazon RDS
Use IAM Authentication
IAM authentication is a robust feature of Amazon RDS that allows you to use IAM users and roles to manage database access. By using IAM authentication, you can enforce strict access controls, utilize AWS’s native multi-factor authentication, and eliminate the need for a traditional username and password.
To use IAM authentication with Amazon RDS for MySQL, you need to enable it during the database creation or modify an existing database to support it. Once enabled, you can create IAM roles with specific RDS permissions and assign these roles to your users.
Enable Encryption at Rest and in Transit
Encryption is a critical aspect of data security. Amazon RDS for MySQL supports encryption at rest and in transit to protect your sensitive data. Encryption at rest encrypts your data before storing it on the disk, preventing unauthorized access to your data even if the underlying storage is compromised.
On the other hand, encryption in transit ensures that your data is secure while it travels over the network between your database and your application. Amazon RDS supports SSL encryption for data in transit, ensuring that your data cannot be intercepted or tampered with during transmission.
Restrict Network Access
Network access control is a fundamental part of database security. By restricting network access to your Amazon RDS instances, you can reduce the attack surface and minimize the risk of unauthorized access. You can use Security Groups and Network Access Control Lists (NACLs) in VPC to control inbound and outbound traffic to your RDS instances.
Security Groups act as a virtual firewall at the instance level, while NACLs provide a secondary layer of security at the subnet level. By configuring these controls correctly, you can ensure that only trusted and necessary traffic can reach your Amazon RDS for MySQL instances.
Implement Database Activity Monitoring
Monitoring database activities is crucial for detecting anomalies, identifying potential threats, and responding to security incidents. Amazon RDS provides several monitoring features that you can use to keep an eye on your MySQL databases.
Amazon RDS Event Notifications can alert you about significant events, such as failover or backups. Amazon CloudWatch can monitor your databases’ performance and operational health. Additionally, AWS CloudTrail can track API calls to your RDS instances, providing visibility into user activities and potential security issues.
Limit and Monitor User Privileges
Managing user privileges is a critical aspect of database security. Granting excessive privileges or failing to revoke unnecessary privileges can lead to privilege abuse and unauthorized access to sensitive data. Therefore, it’s essential to follow the principle of least privilege (PoLP) when managing user access to your Amazon RDS for MySQL databases.
You should regularly review and update user privileges to ensure they align with their roles and responsibilities. Furthermore, you should monitor user activities to detect any suspicious behavior or privilege abuse. AWS CloudTrail and Amazon RDS’s native auditing features can help you achieve this.
Conclusion
In conclusion, Amazon RDS for MySQL is a powerful service that can simplify database management and increase productivity. However, like any technology, it must be used responsibly. By understanding the potential security risks and implementing the recommended security practices, you can unlock the full potential of Amazon RDS for MySQL while keeping your data secure.