nuvola (with the lowercase n) is a tool to dump and perform automatic and manual security analysis on AWS environments configurations and services using predefined, extensible and custom rules created using a simple Yaml syntax.
The general idea behind this project is to create an abstracted digital twin of a cloud platform. For a more concrete example: nuvola reflects the BloodHound traits used for Active Directory analysis but on cloud environments (at the moment only AWS).
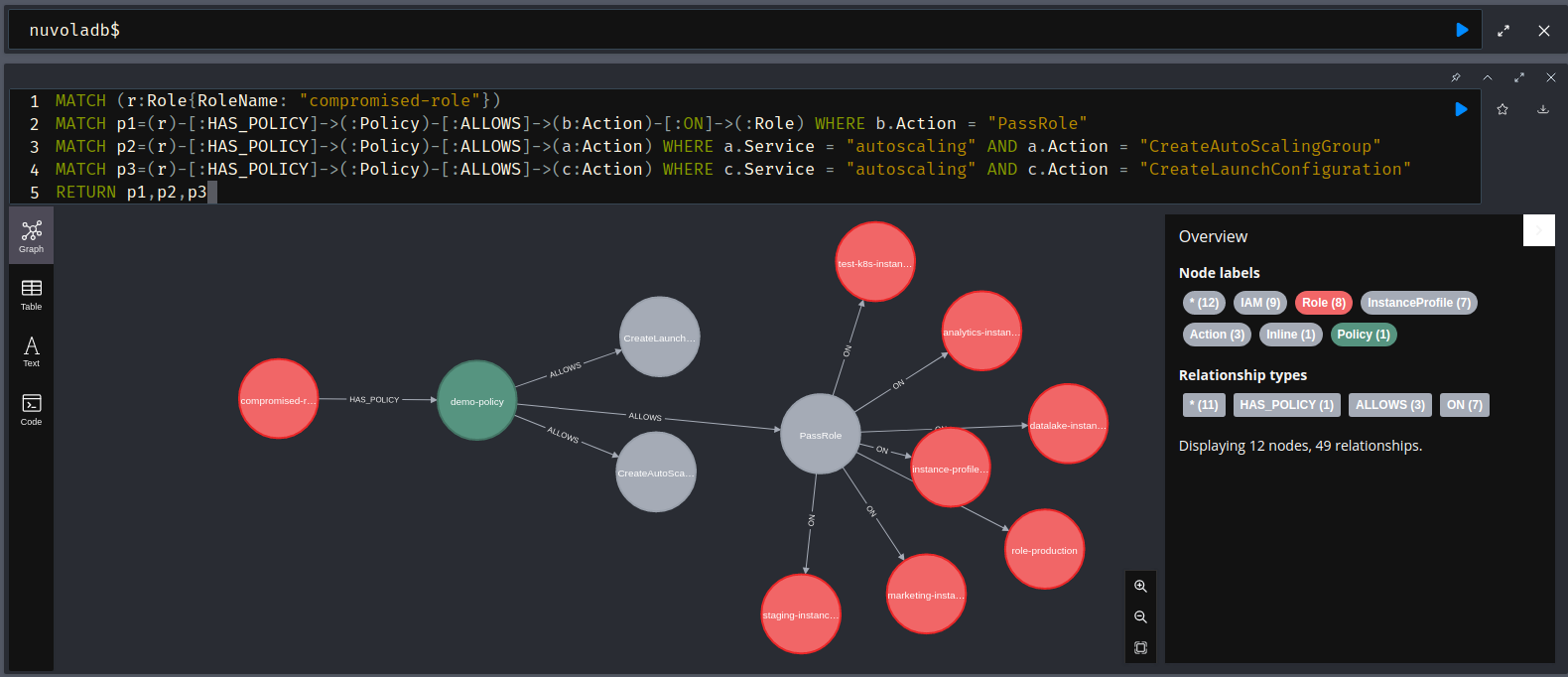
The usage of a graph database also increases the possibility of finding different and innovative attack paths and can be used as an offline, centralised and lightweight digital twin.
Quick Start
Requirements
docker-composeinstalled- an AWS account configured to be used with
awscliwith full access to the cloud resources, better if in ReadOnly mode (the policyarn:aws:iam::aws:policy/ReadOnlyAccessis fine)
Setup
- Clone the repository
git clone --depth=1 https://github.com/primait/nuvola.git; cd nuvola
- Create and edit, if required, the
.envfile to set your DB username/password/URL
cp .env_example .env; Start the Neo4j docker instance make start Build the tool make build
Usage
- Firstly you need to dump all the supported AWS services configurations and load the data into the Neo4j database:
./nuvola dump -profile default_RO -outputdir ~/DumpDumpFolder -format zip
- To import a previously executed dump operation into the Neo4j database:
./nuvola assess -import ~/DumpDumpFolder/nuvola-default_RO_20220901.zip
- To only perform static assessments on the data loaded into the Neo4j database using the predefined ruleset:
./nuvola assess
- Or use Neo4j Browser to manually explore the digital twin.










.png)






