Just some quick malware analysis on a free Saturday. I was just chilling in the morning, reading twitter, and this post from Justin Elze caught my eye:
It was perfect because I was indeed bored 😉
It was an opendir with a few interesting files:
pdf.bat BAT-File 3,179 Bytes Tue, 10 Sep 2024 15:01:49 GMT
python-3.12.5-amd64.exe EXE-File 26,508,648 Bytes Wed, 28 Aug 2024 18:05:07 GMT
sg.py PY-File 4,082,946 Bytes Wed, 04 Sep 2024 01:22:18 GMT
tx.py PY-File 4,082,936 Bytes Tue, 03 Sep 2024 12:04:59 GMT
update.cmd CMD-File 168 Bytes Fri, 06 Sep 2024 16:37:29 GMTpdf.bat was just a launcher for update.cmd with some interesting social engineering aspect, it also established persistence by adding update.cmd to startup files. update.cmd simply executed sg.py and tx.py with python.
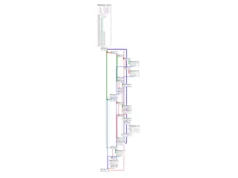
I downloaded entire folder and proceeded to analyze it. After opening sg.py in the text editor, it turned out it’s not a standard python code but a compiled python bytecode.
Ok, shouldn’t be a big issue, there is this great online decompiler that I highly recommend there’s also if you like something that runs offline.
After dumping these files into pylingual I saw the issue. Yes it managed to decompile them but the code was quite obviously obfuscated.
For more information click here.