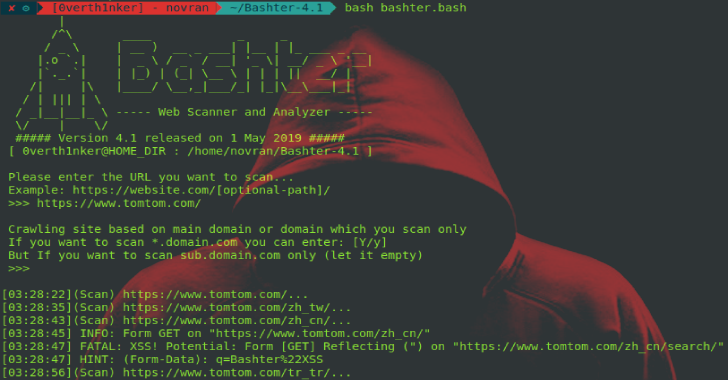
Bashter is a Shell-Script based Web Crawler, Scanner, and Analyser Framework. Bashter is a tool for scanning a Web-based Application. Bashter is very suitable for doing Bug Bounty or Penetration Testing.
It is designed like a framework so you can easily add a script for detect vulnerability.
For Example
To be more powerful, You can add something script (custom) like this:
modules/form/yourscript.bash {WEB-URL} {SOURCECODE}
modules/url/yourscript.bash {WEB-URL} {SOURCECODE}
modules/header/yourscript.bash {WEB-URL} {SOURCECODE}
For the sample, you can follow existing scripts.
Also Read – EvilClippy : For Creating Malicious MS Office Documents
Disable Script
You only need to change the extension, for example .bash => .bashx.
By Default:
- Web Crawler
- Gather Input Form
- Detect Missconfigured CORS
- Detect missing X-FRAME-OPTIONS (Clickjacking Potential)
- Detect Reflected XSS via URL
- Detect Reflected XSS via Form
- Detect HTTP Splitting Response via CRLF Injection
- Detect Open Redirect
How to Run:
git clone https://github.com/zerobyte-id/Bashter.git
cd Bashter/
bash bashter.bash
Notes: This tool will consume a lot of disk usage, so don’t forget to housekeep bashter-tempdata and scan-logs.
Credits: Schopath, Suhada , Abay