APPLICATIONS
HOT NEWS
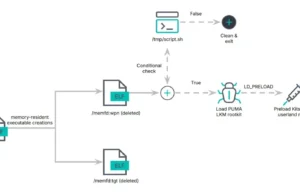
NailaoLoader : Hiding Execution Flow via Patching
NailaoLoader employs sophisticated techniques to obscure its execution flow, leveraging Windows Management Instrumentation (WMI) for lateral movement and file transfer.
Threat actors use WMI...
We provide you with the latest Kali Linux & Penetration testing tools.
Contact us: admin@kalilinuxtutorials.com
© @Kali Linux Tutorials - 2025