APPLICATIONS
HOT NEWS
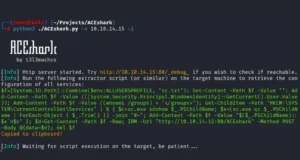
DataSurgeon : Quickly Extracts IP’s, Email Addresses, Hashes, Files, Credit Cards,...
DataSurgeon (ds) is a versatile tool designed for incident response, penetration testing, and CTF challenges. It allows for the extraction of various types of...
© kalilinuxtutorials.com 2025