Crypton is an educational library to learn and practice Offensive and Defensive Cryptography. It is basically a collection of explanation and implementation of all the existing vulnerabilities and attacks on various Encryption Systems (Symmetric and Asymmetric), Digital Signatures, Message Authentication Codes and Authenticated Encryption Systems. Each attack is also supplemented with example challenges from “Capture The Flag” contests and their respective write-ups. Individuals who are already acquainted (or are into CTFs) with this field can use Crypton as a tool to solve challenges based on a particular existing vulnerability.
There are different sections in this README:
- Motivation– What motivated me to create this library
- Library Structure- Directory structure of Crypton
- Domain Coverage- What all cryptosystems and attacks are covered in this library
- Future Plans/Fuss- Attacks/concepts that are to be included soon
Also Read Apache Struts Version 3 : Tool To Exploit 3 RCE Vulnerabilities On ApacheStruts
Motivation
Help CTF players and individuals interested in the field of Cryptography provide a platform for learning attacks in crypto and for experienced CTF players to practice challenges systematically divided into attacks associated with different sub-domains in crypto. Also, illustrate through various attack explanations how proper implementation of protocols is crucial.
Library Structure
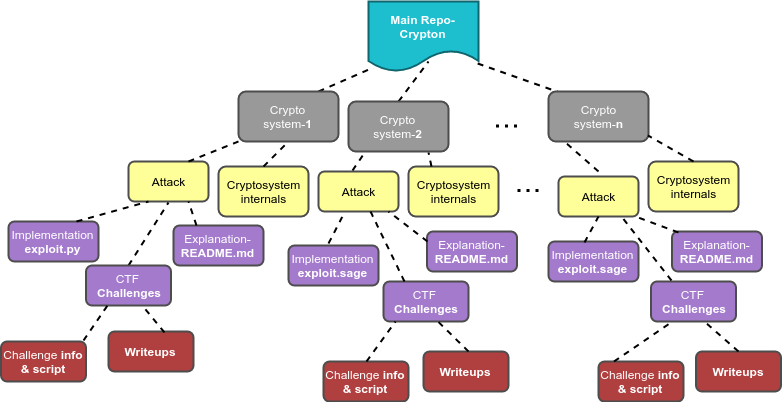
Domain Coverage
1. Block Ciphers
| S.No. |
Topic |
Explanation |
Impl./Exploit |
Challenge# |
| 1 |
Block Cipher Basics– working of block ciphers, padding etc. |
|
|
|
| 2 |
Modes of Encryption– different modes of operation on block ciphers: ECB, CBC, CTR |
|
|
|
| 3 |
Block Size Detection– detect blocksize of a block cipher encrypting data on a remote service |
|
|
|
| 4 |
Mode Detection– detect type of mode of encryption: independent or dependent encryption of blocks |
|
|
|
| 5 |
ECB Byte at a Time– byte at a time decryption of a secret string running on a remote service encrypting input+secret in ECB mode |
|
|
|
| 6 |
CBC IV Detection– detect the value of Initialisation Vector on a remote service that is encrypting our input using a block cipher in CBC mode |
|
|
|
| 7 |
CBC Bit Flipping Attack– exploiting cookie generation mechanism to login as admin when cookie is generated using a block cipher in CBC mode |
|
|
|
| 8 |
CBC Byte at a Time– byte at a time decryption of a secret string running on a remote service encrypting input+secret in ECB mode |
|
|
|
| 9 |
CBC Padding Oracle Attack– decryption of data encrypted by a vulnerable service providing encryption/decryption |
|
|
|
| 10 |
CTR Bit Flipping– exploiting cookie generation mechanism to login as admin when cookie is generated using a block cipher in CBC mode |
|
|
|
2. RSA Encryption
3. Message Authentication Codes (MACs)
4. Discrete Logarithm Problem
| S.No. |
Topic |
Explanation |
Impl./Exploit |
Challenge# |
| 1 |
DLP– cyclic groups, discrete logarithm problem, Baby-Step-Giant-Step algorithm |
|
|
|
| 2 |
Elliptic Curve DLP– defining identity element, inverse of a point, cyclic groups over points on an EC, Hasse’s theorem, ECDLP |
|
|
|
5. ElGamal Encryption
6. Authenticated Encryption (AE)
7. Elliptic Curves
| S.No. |
Topic |
Explanation |
Impl./Exploit |
Challenge# |
| 1 |
Elliptic Curve Internals– defining Elliptic Curves, point addition, point doubling and scalar multiplication |
|
|
|
8. Digital Signatures
Fuss
- RSA Encryption
- Chosen Ciphertext Attack on RSA Cryptosystem- Byte by Byte decryption
- Padding Oracle Attack on PKCS1 padded RSA encryption systemat
- Fermat’s Factorisation
- Coppersmith’s Attack
- Hastad’s Broadcast Attack
- Implementation of HBA on padded messages
- PKCS1-v1.5 Padded RSA encryption
Crypton Disclaimer
The author in no way guarantees that the code is secure. The library is only meant for educational purposes and the code should not be used for implementing in real world. All the example scripts in the library are trivial implementations.
 Credit : Ashutosh Ahelleya
Credit : Ashutosh Ahelleya
Related