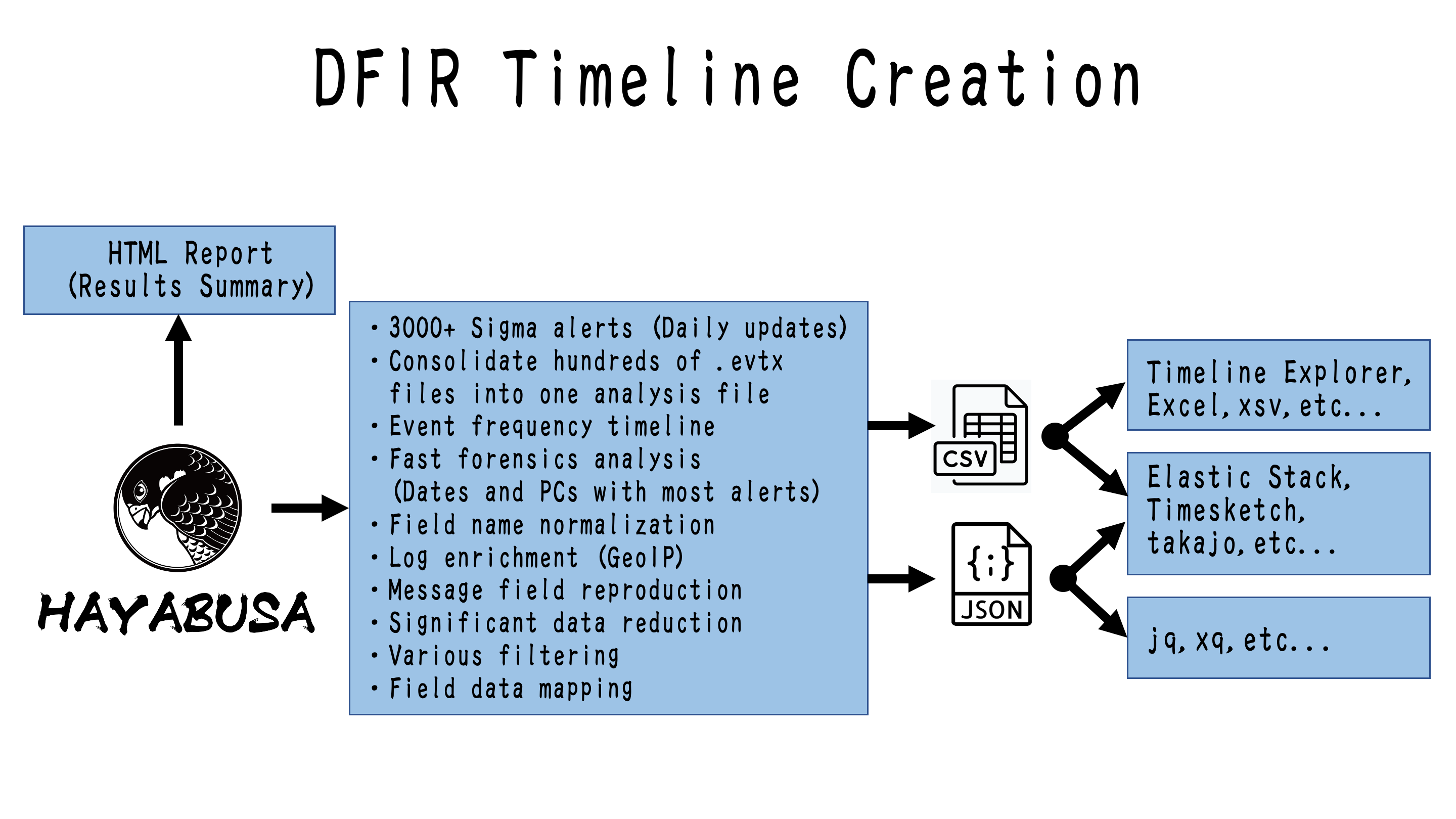
Hayabusa is a Windows event log fast forensics timeline generator and threat hunting tool created by the Yamato Security group in Japan. Hayabusa means “peregrine falcon” in Japanese and was chosen as peregrine falcons are the fastest animal in the world, great at hunting and highly trainable. It is written in Rust and supports multi-threading in order to be as fast as possible. We have provided a tool to convert Sigma rules into Hayabusa rule format. The Sigma-compatible Hayabusa detection rules are written in YML in order to be as easily customizable and extensible as possible. Hayabusa can be run either on single running systems for live analysis, by gathering logs from single or multiple systems for offline analysis, or by running the Hayabusa artifact with Velociraptor for enterprise-wide threat hunting and incident response. The output will be consolidated into a single CSV timeline for easy analysis in LibreOffice, Timeline Explorer, Elastic Stack, Timesketch, etc…
Companion Projects
- EnableWindowsLogSettings – Documentation and scripts to properly enable Windows event logs.
- Hayabusa Rules – Detection rules for hayabusa.
- Hayabusa Sample EVTXs – Sample evtx files to use for testing hayabusa/sigma detection rules.
- Takajo – An analyzer for hayabusa results.
- WELA (Windows Event Log Analyzer) – An analyzer for Windows event logs written in PowerShell.
Main Goals
Threat Hunting and Enterprise-wide DFIR
Hayabusa currently has over 2500 Sigma rules and over 150 Hayabusa built-in detection rules with more rules being added regularly. It can be used for enterprise-wide proactive threat hunting as well as DFIR (Digital Forensics and Incident Response) for free with Velociraptor‘s Hayabusa artifact. By combining these two open-source tools, you can essentially retroactively reproduce a SIEM when there is no SIEM setup in the environment. You can learn about how to do this by watching Eric Capuano‘s Velociraptor walkthrough here.
Fast Forensics Timeline Generation
Windows event log analysis has traditionally been a very long and tedious process because Windows event logs are 1) in a data format that is hard to analyze and 2) the majority of data is noise and not useful for investigations. Hayabusa’s goal is to extract out only useful data and present it in a concise as possible easy-to-read format that is usable not only by professionally trained analysts but any Windows system administrator. Hayabusa hopes to let analysts get 80% of their work done in 20% of the time when compared to traditional Windows event log analysis.
Screenshots
Startup

For More Click Here

















.webp)