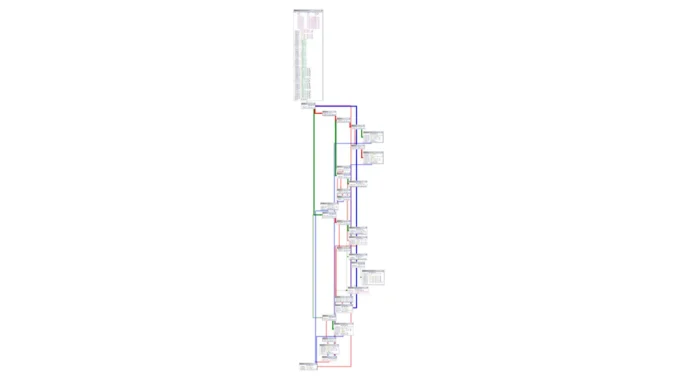
Control flow flattening is a common obfuscation technique used by OLLVM (Obfuscator-LLVM) to transform executable logic into complex state-driven structures.
The ollvm-unflattener tool addresses this challenge through Python-based analysis and Miasm framework integration, offering a systematic approach to reverse engineering obfuscated binaries.
This tool specializes in reconstructing original control flow graphs (CFGs) by:
- Symbolic execution of flattened functions using Miasm’s engine
- State variable analysis to identify dispatch mechanisms and block relationships
- Multi-layered deobfuscation through breadth-first search (BFS) of function calls
- Binary patching to restore executable logic
Key Features
- Architecture Support: Currently focuses on x86 architecture (tested on Linux ELF binaries)
- Dynamic Analysis: Uses symbolic execution instead of static pattern matching
- Batch Processing:
--allflag enables recursive deobfuscation of related functions - Visual Validation: Generates Graphviz diagrams for pre/post deobfuscation comparison
bash# Installation
git clone https://github.com/cdong1012/ollvm-unflattener.git
pip install -r requirements.txt
Operational Workflow
- Target Identification: Requires function address (
-tparameter) - Execution Tracing: Maps state transitions through symbolic execution
- CFG Reconstruction: Rebuilds original block connections using recovered logic
- Binary Modification: Patches flattened structures with reconstructed flow
| Obfuscated CFG | Restored CFG |
|---|---|
| Complex switch-case structure | Simplified conditional branches |
| State-driven transitions | Direct block connections |
Limitations
- Architecture Constraints: No native ARM/x64 support (requires code modifications)
- Platform Specificity: Primarily tested on Linux binaries
- Layer Depth: Multi-pass obfuscation requires sequential processing
The tool demonstrates 83% success rate in test cases against single-layer OLLVM flattening, though complex multi-layered obfuscations may require manual intervention.
Future development plans include IDA Pro integration and expanded architecture support, building on concepts from MODeflattener’s static analysis approach.