Solana Smart Contract Security Best Practices: Essential Tools And Functions
Ensuring the security of Solana smart contracts is crucial to prevent exploits and maintain the integrity of blockchain applications. The Solana ecosystem provides several tools and best practices to enhance security. Here's an overview of key tools and functions that help secure Solana smart contracts: Common Pitfalls And Solutions Integer Overflow/Underflow: Use checked_add, checked_sub, checked_div, and checked_mul to prevent overflows. Loss of...
Program Exposes Unsound And Incomplete Behavior In Compiler
The provided program highlights critical issues within the compiler, exposing both soundness and completeness violations. These bugs manifest in unexpected behavior during execution and compiler crashes, triggered by seemingly innocuous code changes. This article explores the problem, its symptoms, and implications. Program Behavior The program is written in Noir and aims to compute a value, out0, which should consistently return Field(0)...
BypassAV : Techniques To Evade Antivirus And EDR Systems
BypassAV refers to the collection of techniques and tools used to bypass antivirus (AV) and Endpoint Detection and Response (EDR) systems. These security solutions are designed to detect and block malicious activities, but attackers continuously develop methods to evade them. Below is an overview of key techniques and tools used in bypassing AV and EDR systems. Key Techniques For Bypassing...
ComDotNetExploit : Exploiting Windows Protected Process Light (PPL)
ComDotNetExploit is a Proof of Concept (PoC) tool designed to demonstrate the exploitation of Windows Protected Process Light (PPL) by leveraging COM-to-.NET redirection and reflection techniques for code injection. PPL is a security feature introduced in Windows 8.1 to protect critical processes like LSASS from unauthorized access or modification. T his exploit bypasses code integrity checks, enabling malicious payload injection...
Trigon : A Revolutionary Kernel Exploit For iOS
Trigon is a sophisticated deterministic kernel exploit targeting Apple’s iOS devices, leveraging the CVE-2023-32434 vulnerability. This exploit, developed by Alfie CG and collaborators, introduces a groundbreaking approach to kernel exploitation by ensuring reliability and stability during and after execution. Unlike traditional methods prone to instability, Trigon guarantees deterministic outcomes, making it a significant advancement in iOS security research. Technical Overview At...
Bug Bounty Report Templates : Enhancing Efficiency In Vulnerability Reporting
Bug bounty report templates are essential tools for streamlining the process of documenting vulnerabilities. They ensure that hackers provide clear, structured, and comprehensive information, enabling program managers to validate and address issues effectively. Below is an overview of the functionality, benefits, and examples of bug bounty report templates. Purpose Of Bug Bounty Report Templates Standardization: Templates create consistency across reports, ensuring...
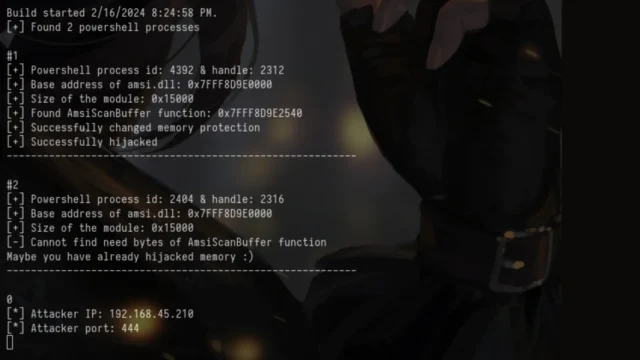
FullBypass : A Tool For AMSI And PowerShell CLM Bypass
FullBypass is a tool designed to circumvent Microsoft's Antimalware Scan Interface (AMSI) and PowerShell's Constrained Language Mode (CLM). By doing so, it enables the execution of unrestricted PowerShell commands, providing a FullLanguage reverse shell. While such tools can be used for legitimate penetration testing and security research, their unethical use is prohibited and may violate laws. How FullBypass Works AMSI Bypass:AMSI...
Carseat : A Python Implementation Of Seatbelt
Carseat is a Python-based tool that replicates the functionality of the well-known security auditing tool, Seatbelt. It includes nearly all modules from Seatbelt, focusing on remote execution capabilities. Designed for cybersecurity professionals, Carseat is particularly useful for gathering system information and assessing security configurations on target hosts. However, privileged access is typically required to execute its modules effectively. Carseat relies...
Pyda : A Tool For Dynamic Binary Analysis
Pyda is an innovative tool designed to simplify dynamic binary analysis by allowing developers to write analysis tools in Python. Built on top of Dynamorio-based instrumentation, Pyda integrates seamlessly with a CPython interpreter, enabling users to inject Python code into x86/ARM64 Linux processes without relying on traditional debugging methods like GDB or ptrace. Key Features Of Pyda Instruction Hooks: Pyda allows...
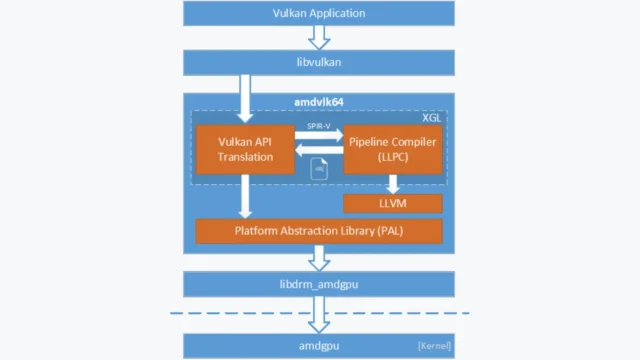
AMDVLK : The Power Of Vulkan On AMD GPUs For Linux
The AMD Open Source Driver for Vulkan® (AMDVLK) is a powerful, open-source Vulkan driver developed by AMD for Radeon™ graphics adapters on Linux®. Designed to optimize the performance of Vulkan-based applications, AMDVLK leverages AMD's Platform Abstraction Library (PAL) to provide a consistent experience across platforms. Below, we explore its tools and functions. Key Functions And Features Vulkan API Support:AMDVLK supports Vulkan...