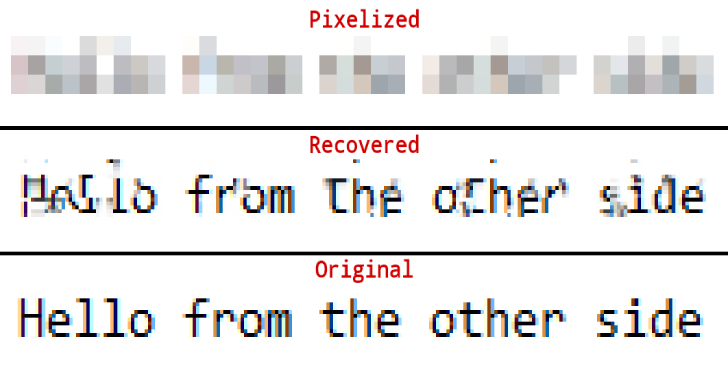
Depix : Recovers Passwords From Pixelized Screenshots
Depix is a tool for recovering passwords from pixelized screenshots. This implementation works on pixelized images that were created with a linear box filter. In this article I cover background information on pixelization and similar research. Example python depix.py -p images/testimages/testimage3_pixels.png -s images/searchimages/debruinseq_notepad_Windows10_closeAndSpaced.png -o output.png Usage Cut out the pixelated blocks from the screenshot as a single rectangle.Paste a De Bruijn sequence with expected...
Js-X-Ray : JavaScript & Node.js Open-Source SAST Scanner
Js-X-Ray is a JavaScript AST analysis. This package has been created to export the Node-Secure AST Analysis to enable better code evolution and allow better access to developers and researchers. The goal is to quickly identify dangerous code and patterns for developers and Security researchers. Interpreting the results of this tool will still require you to have a set of...
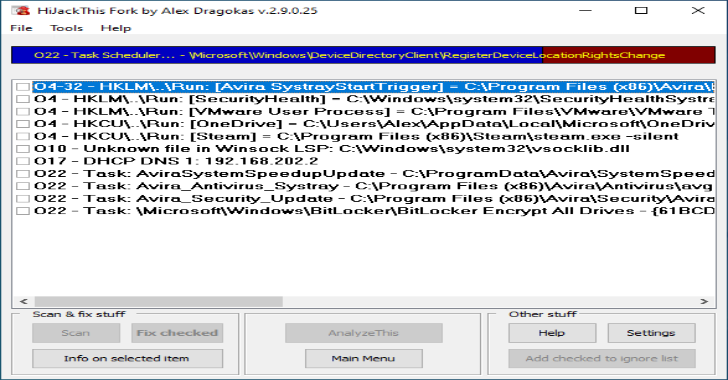
HiJackThis : A Free Utility That Finds Malware, Adware & Other Security Threats
HiJackThis Fork is a free utility for Microsoft Windows that scans your computer for settings changed by adware, spyware, malware and other unwanted programs. HiJackThis Fork primarily detects hijacking methods rather than comparing items against a pre-built database. This allows it to detect new or previously unknown malware - but it also makes no distinction between safe and unsafe items....
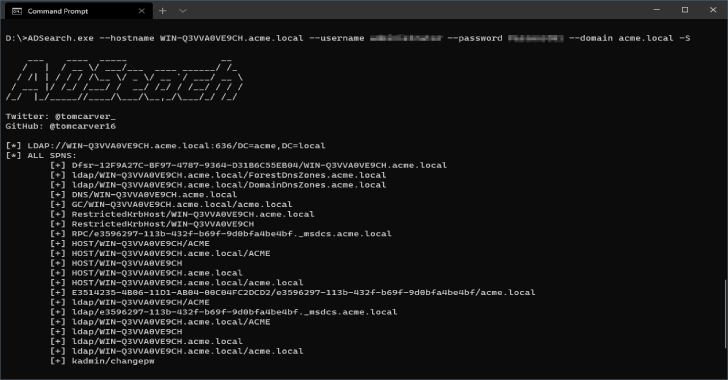
ADSearch : A Tool To Help Query AD Via The LDAP Protocol
ADSearch is a tool written for cobalt-strike's execute-assembly command that allows for more efficent querying of AD. Key Features List all Domain AdminsCustom LDAP SearchConnect to LDAPS ServersOutput JSON data from AD instancesRetrieve custom attributes from a generic query (i.e. All computers) Usage ADSearch 1.0.0.0Copyright c 2020USAGE:Query Active Directory remotely or locally:ADSearch --domain ldap.example.com --password AdminPass1 --username admin --users-f, --full If set will...
Obfuscator : The Program Is Designed To Obfuscate The Shellcode
Obfuscator program is designed to obfuscate the shellcode. Currently the tool supports 2 encryption. XOR AES The tool accepts shellcode in 4 formats. base64 hex c raw Command Line Usage Usage Description ----- ----------- /f ...
Pytmipe : Python Library And Client For Token Manipulations & Impersonations For Privilege Escalation On Windows
PYTMIPE (PYthon library for Token Manipulation and Impersonation for Privilege Escalation) is a Python 3 library for manipulating Windows tokens and managing impersonations in order to gain more privileges on Windows. TMIPE is the python 3 client which uses the pytmipe library. Content A python client: tmipe (python3 tmipe.py)A python library: pytmipe. Useful for including this project in another onepytinstaller examples,...
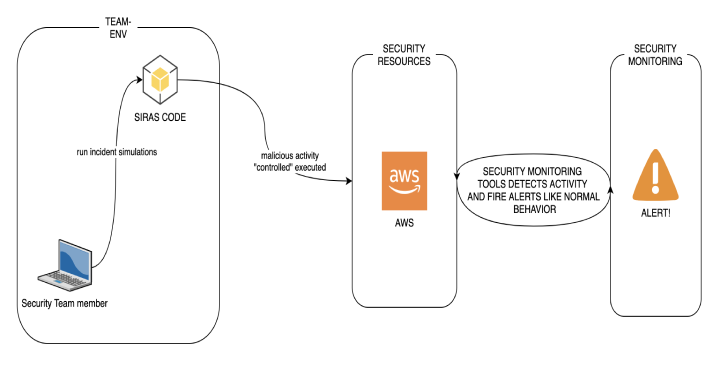
Siras : Security Incident Response Automated Simulations
Security Incident Response Automated Simulations (SIRAS) are internal/controlled actions that provide a structured opportunity to practice the incident response plan and procedures during a realistic scenarios. the main idea of SIRAS is create an detection-as-a-code testing scenarios to facilitate the blueteam/tabletops scenarios. All smokers of siras make real actions into your AWS and then delete those actions in the...
A Native VPN for Linux Users
From Mac to Windows to the mighty Linux, there are multiple operating systems out there. Obviously, they all have benefits over the others, but for you Linux users out there, you might be thinking you have the best security systems available;those online hackers won’t get hold of your details or subject you to password attacks. You might also be...
Fuzzilli : A JavaScript Engine Fuzzer
Fuzzilli is a (coverage-)guided fuzzer for dynamic language interpreters based on a custom intermediate language ("FuzzIL") which can be mutated and translated to JavaScript. Usage The basic steps to use this fuzzer are: Download the source code for one of the supported JavaScript engines. See the Targets/ directory for the list of supported JavaScript engines.Apply the corresponding patches from the target's directory....
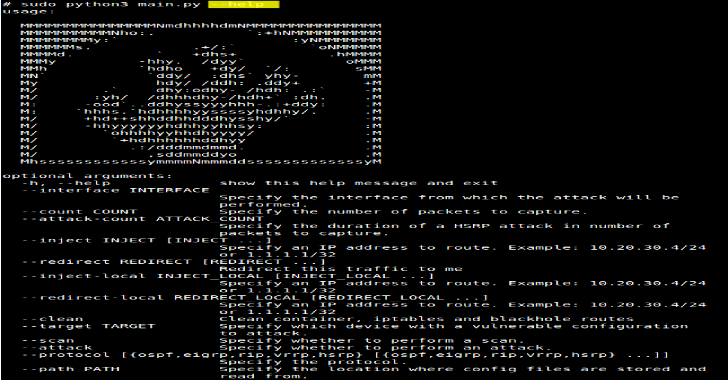
Routopsy : A Toolkit To Attack Networking Protocols
Routopsy is a toolkit built to attack often overlooked networking protocols. Routopsy currently supports attacks against Dynamic Routing Protocols (DRP) and First-Hop Redundancy Protocols (FHRP). Most of the attacks currently implemented make use of a weaponized 'virtual router' as opposed to implementing protocols from scratch. The tooling is not limited to the virtual routers, and allows for further attacks...