Permission Manager : Tool To Kubernetes RBAC And Users Management, Web UI FTW
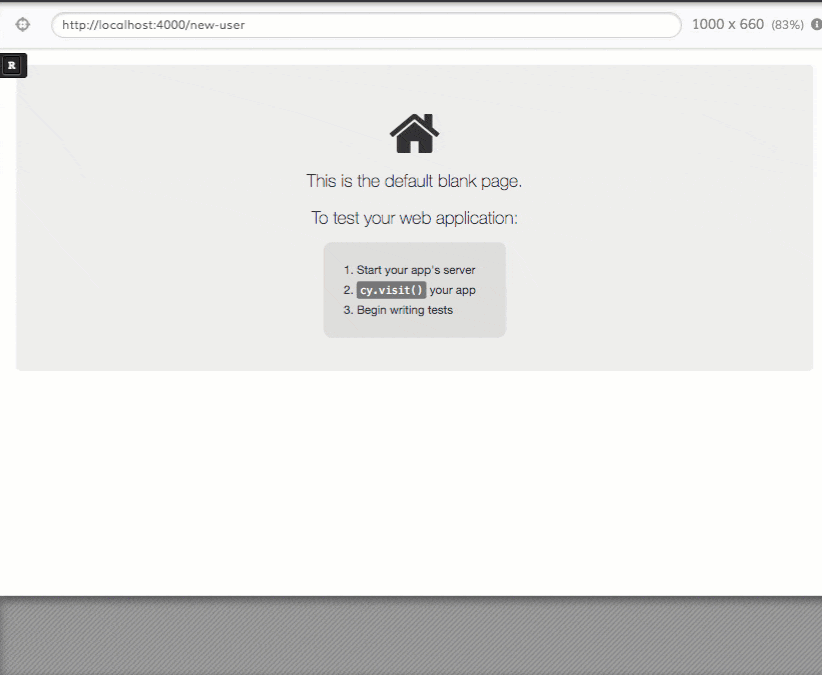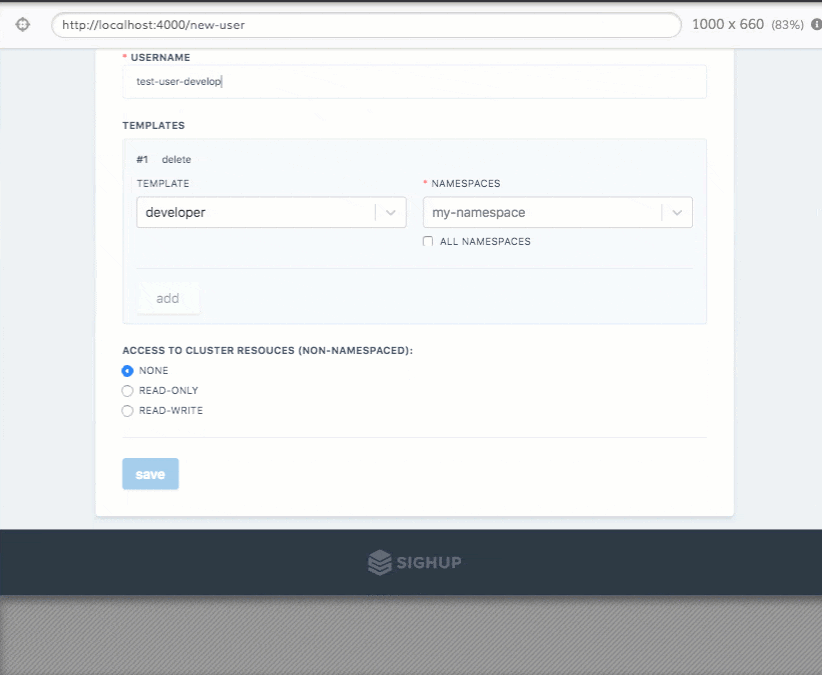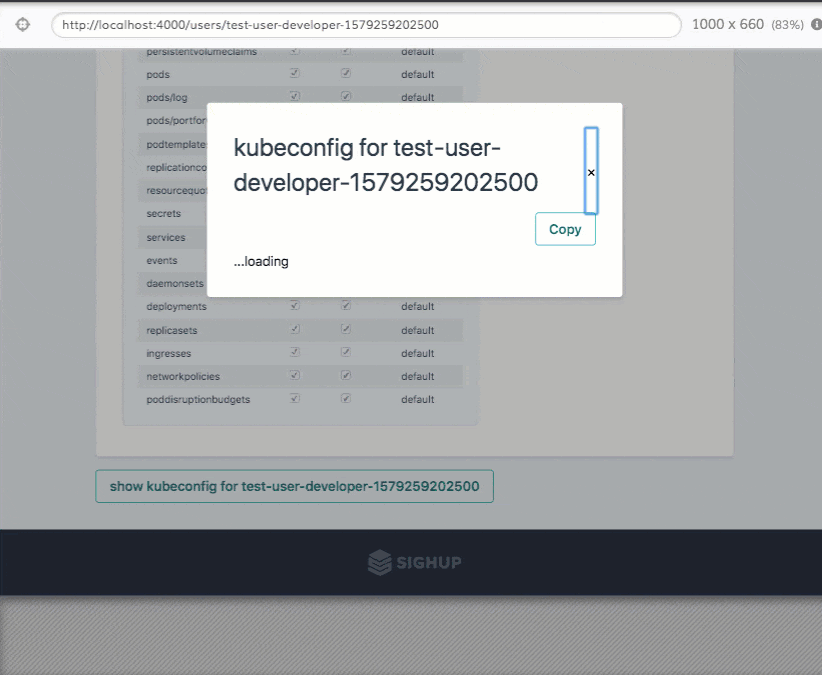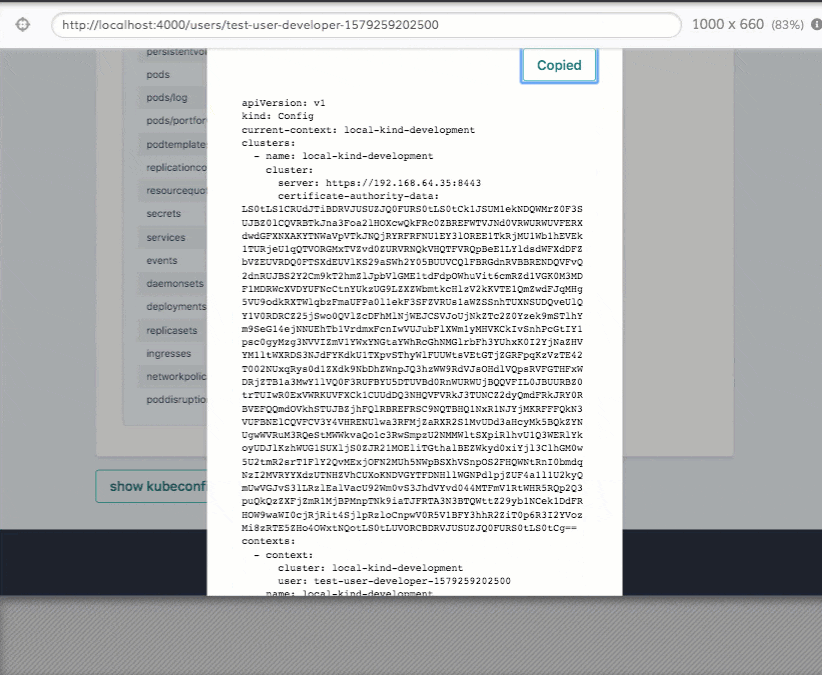
Permission Manager is an application developed by SIGHUP that enables a super-easy and user-friendly RBAC management for Kubernetes. If you are looking for a simple and intuitive way of managing your users within a Kubernetes cluster, this is the right place. With Permission Manager, you can create users, assign namespaces/permissions, and distribute Kubeconfig YAML files via a nice&easy web UI. Screenshots First...
Quiver : A Meta-Tool for Kali Linux
Quiver is an organized namespace of shell functions that pre-fill commands in your terminal so that you can ditch your reliance on notes, copying, pasting, editing, copying and pasting again. Quiver helps you remember how to use every tool in your arsenal and doesn't hide them behind scripting that can be cumbersome to maintain or update. Instead you can...
Onex : A Library Of Hacking Tools For Termux And Other Linux Distributions
Onex is a kali linux hacking tools installer for termux and other linux distribution. It's package manager for hacker's. It can manage large number's of hacking tools that can be installed on single click. Using onex, you can install all hacking tools in Termux and other Linux based distributions. onex can install more than 370+ kali linux hacking tools....
Kali Linux Tools Interface
Kali Linux Tools Interface is a graphical interface to use information security tools by the browser. The project uses the Kali Linux tools as a reference because it is the distribution that has the largest package of native tools. Prerequisites A Debian-based distribution (preferably Kali Linux)The information security tools installedApache / Nginx service runningSSH Service runningShell In A Box (if you...
Lazybee : Wordlist Generator Tool For Termux
Lazybee tool is a python based script from which you can generate random wordlist for brutefocre attacks. This tool has a unique features like wordlist generating time calculation and direct .txt saving in current directory. This tool works on both rooted Android device and Non-rooted Android device. It is available for Termux Installation & Usage $ apt-get update -y$ apt-get upgrade -y$...
NTLMRecon : Tool To Find Out Information About NTLM Endpoints
NTLMRecon is built with flexibilty in mind. Need to run recon on a single URL, an IP address, an entire CIDR range or combination of all of it all put in a single input file? No problem! NTLMRecon got you covered. Read on. A fast and flexible NTLM reconnaissance tool without external dependencies. Useful to find out information about NTLM...
ADB-Toolkit : Tool To Hack Android Device
ADB-Toolkit is a BASH Script with 28 options and an METASPLOIT Section which has 6 options which is made to do easy penetration testing in Android Device. You can do preety much any thing with this script and test your android device is it safe or not. This script is made with the help of ADB (Android Debug Bridge)...
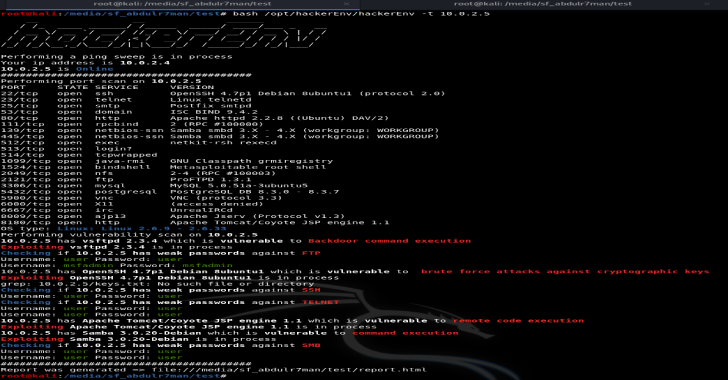
HackerEnv : Sweep IPs & Scan Ports, Vulnerabilities & Exploit Them
hackerEnv is an automation tool that quickly and easily sweep IPs and scan ports, vulnerabilities and exploit them. Then, it hands you an interactive shell for further testing. Also, it generates HTML and docx reports. It uses other tools such as nmap, nikto, metasploit and hydra. Works in kali linux and Parrot OS. Do not run it in Qterminal,...
Peniot : Penetration Testing Tool for IoT
PENIOT is a penetration testing tool for Internet of Things (IoT) devices. It helps you to test/penetrate your devices by targeting their internet connectivity with different types of security attacks. In other words, you can expose your device to both active and passive security attacks. After deciding target device and necessary information (or parameters) of that device, you can...
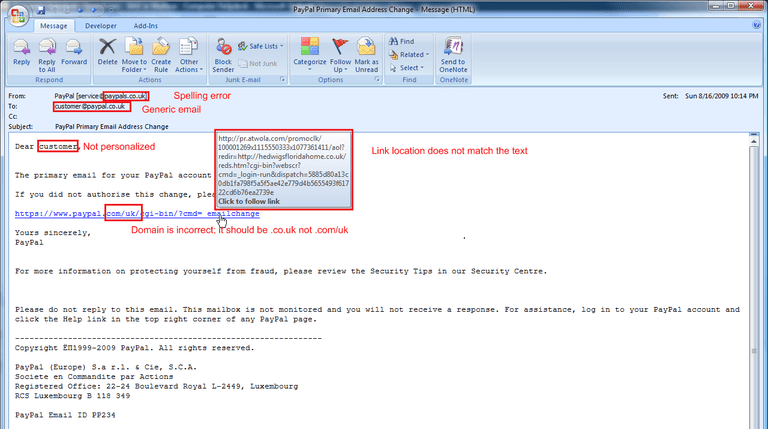
What is Email Spoofing? and How to Avoid It?
Have you ever seen emails that looked genuine but were a scam? Well, these are spoofed emails for you! Talking about email spoofing, they are emails that appear to be from a known person, but they are not in reality. Cybercriminals modify the header of an email to make it look as if it is sent by someone genuine. It is...