AngrgDB : Use Angr Inside GDB
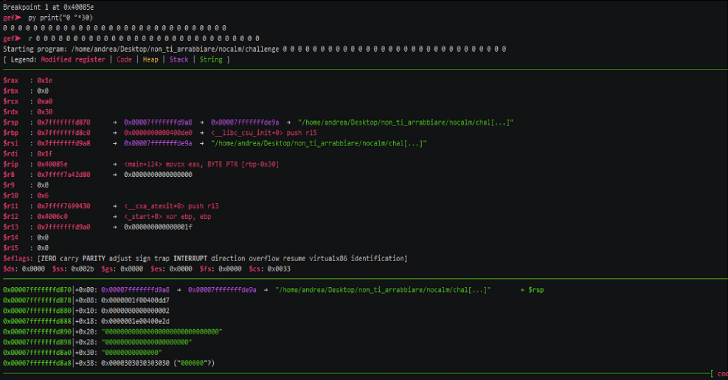
AngrgDB use angr inside GDB. Create an angr state from the current debugger state. Install pip install angrgdb echo "python import angrgdb.commands" >> ~/.gdbinit Usage AngrgDB implements the angrdbg API in GDB. You can use it in scripts like this: from angrgdb import *gdb.execute("b *0x004005f9")gdb.execute("r aaaaaaaa")sm = StateManager()sm.sim(sm, 100)m = sm.simulation_manager()m.explore(find=0x00400607, avoid=0x00400613)sm.to_dbg(m.found) #write input to GDBgdb.execute("x/s $rax")#0x7fffffffe768: "ais3{I_tak3_g00d_n0t3s}"gdb.execute("c")#Correct! that is the secret key! You can also...
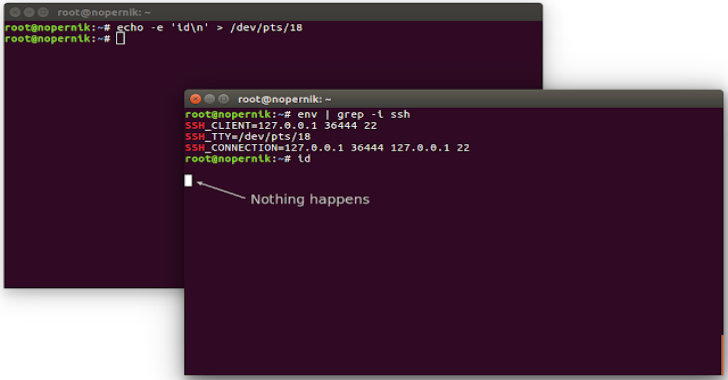
SSHPry V2 – Spy & Control OS SSH Connected Client’s TTY
This is a second release of SSHPry tool, with multiple features added. Control of target's TTYBuilt-In KeyloggerConsole-Level phishingRecord & Replay previous sessions I always curious about what can be done after you somehow got root and already talked about some techniques of post exploitation with highly privileged accounts: SSH SnoopingRDP Session Hijacking Also Read - One-Lin3r : Gives You One Liners That Aids...
Sandcastle : A Python Script For AWS S3 Bucket Enumeration
Inspired by a conversation with Instacart's @nickelser on HackerOne, I've optimized and published Sandcastle – a Python script for AWS S3 bucket enumeration, formerly known as bucketCrawler. The script takes a target's name as the stem argument (e.g. shopify) and iterates through a file of bucket name permutations, such as the ones below: -training -bucket -dev -attachments -photos -elasticsearch Getting...
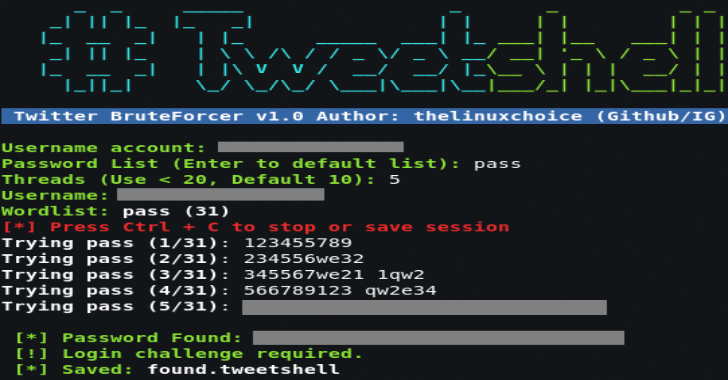
TweetShell : Multi-Thread Twitter BruteForcer In Shell Script
Tweetshell is an Shell Script to perform multi-threaded brute force attack against Twitter, this script can bypass login limiting and it can test infinite number of passwords with a rate of +400 passwords/min using 20 threads. Multi-thread Twitter BruteForcer in Shell Script. Features Multi-thread (400 pass/min, 20 threads)Save/Resume sessionsAnonymous attack through TORDefault password list (best +39k 8 letters)Check valid usernameCheck and...
Jackdaw : Gather Gather Gather
Jackdaw is here to collect all information in your domain, store it in a SQL database and show you nice graphs on how your domain objects interact with each-other an how a potential attacker may exploit these interactions. It also comes with a handy feature to help you in a password-cracking project by storing/looking up/reporting hashes/passowrds/users. Example Commands Most of these...
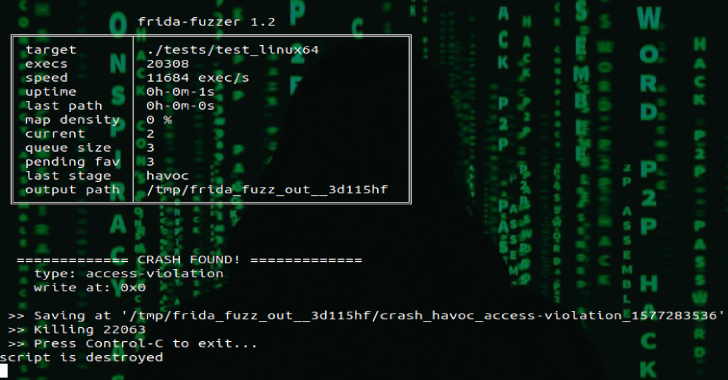
Frida-Fuzzer : Experimental Fuzzer Used For API In-Memory Fuzzing
Frida-Fuzzer is a experimental fuzzer is meant to be used for API in-memory fuzzing. The design is highly inspired and based on AFL/AFL++. ATM the mutator is quite simple, just the AFL's havoc and splice stages. I tested only the examples under tests/, this is a WIP project but is known to works at least on GNU/Linux x86_64 and...
DigiTrack : Attacks For $5 or Less Using Arduino
In 30 seconds, DigiTrack attack can learn which networks a MacOS computer has connected to before, and plant a script that tracks the current IP address and Wi-Fi network every 60 seconds. It includes Hardtracker - Digispark VPN buster to send the IP address and BSSID/SSID of nearby Wi-Fi networks on a MacOS computer to a Grabify tracker every 60...
FProbe : Domains/Subdomains & Probe For Working Http/Https Server
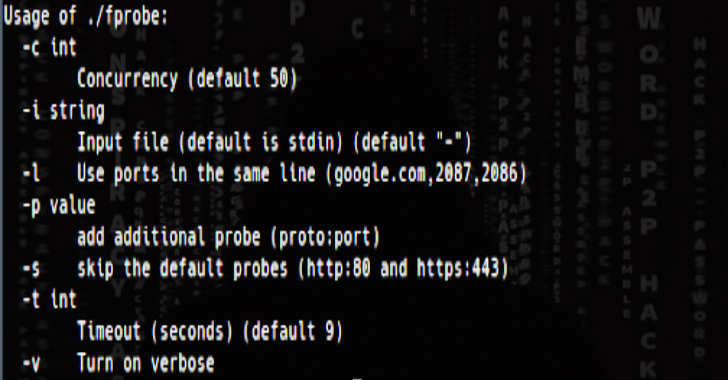
FProbe is a took to take list of domains/subdomains and probe for working http/https server. Installation GO111MODULE=on go get -u github.com/theblackturtle/fprobe Features Take a list of domains/subdomains and probe for working http/https server.Optimize RAM and CPU in runtime.Support special ports for each domainVerbose in JSON format with some additional headers, such as Status Code, Content Type, Location. Usage Usage******* -c int ...
MSSQLi-DUET : MSSQL Injection-based Domain User Enumeration Tool
SQL injection script for MSSQL that extracts domain users from an Active Directory environment based on RID bruteforcing. Supports various forms of WAF bypass techniques through the implementation of SQLmap tamper functions. Additional tamper functions can be incorporated by the user depending on the situation and environment. Comes in two flavors: straight-up Python script for terminal use, or a Burp...
AWSPX : A Graph-Based Tool For Visualizing Effective Access
AWSPX is a graph-based tool for visualizing effective access and resource relationships within AWS. It resolves policy information to determine what actions affect which resources, while taking into account how these actions may be combined to produce attack paths. Unlike tools like Bloodhound, awspx requires permissions to function. It is not expected to be useful in cases where these...