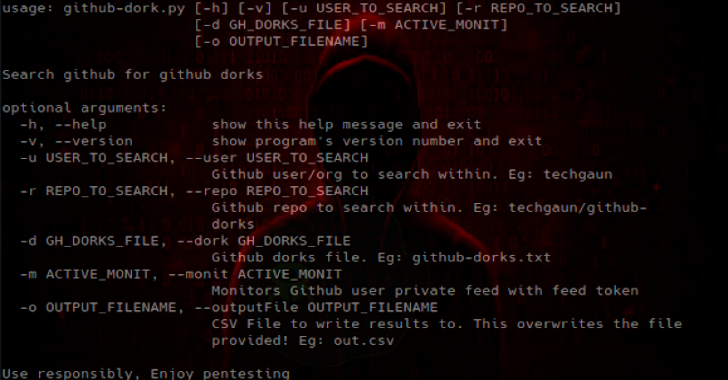
Github Dorks : Collection of Github Dorks & Helper Tool
Github search is quite powerful and useful feature and can be used to search sensitive data on the repositories. Collection of github dorks that can reveal sensitive personal and/or organizational information such as private keys, credentials, authentication tokens, etc. This list is supposed to be useful for assessing security and performing pen-testing of systems....
EyeWitness : Designed To Take Screenshots Of Websites
EyeWitness is designed to take screenshots of websites provide some server header info, and identify default credentials if known. It is designed to run on Kali Linux. It will auto detect the file you give it with the -f flag as either being a text file with URLs on each new line, nmap XML output, or nessus...
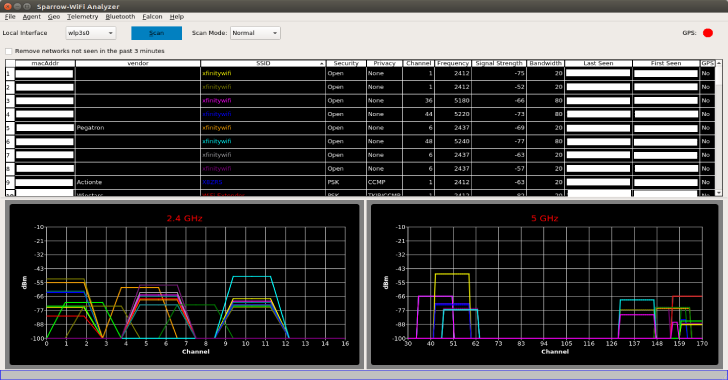
Sparrow WiFi : Next-Gen GUI-based WiFi & Bluetooth Analyzer for Linux
Sparrow WiFi has been built from the ground up to be the next generation 2.4 GHz and 5 GHz WiFi spectral awareness tool. At its most basic it provides a more comprehensive GUI-based replacement for tools like inSSIDer and linssid that runs specifically on Linux. In its most comprehensive use cases, it integrates...
XRay : Tool For Recon, Mapping & OSINT Gathering From Public Networks
XRay is a tool for network OSINT gathering, its goal is to make some of the initial tasks of information gathering and network mapping automatic. How Does it Work? XRay is a very simple tool, it works this way: It'll bruteforce subdomains using a wordlist and DNS requests.For every subdomain/ip found, it'll use Shodan to gather open ports and...
Trivy : Simple & Comprehensive Vulnerability Scanner
Trivy is a Simple and Comprehensive Vulnerability Scanner for Containers, Suitable for CI. A software vulnerability is a glitch, flaw, or weakness present in the software or in an Operating System. It detects vulnerabilities of OS packages (Alpine, RHEL, CentOS, etc.) and application dependencies (Bundler, Composer, npm, yarn etc.). It is easy to use. Just...
Mallory : HTTP/HTTPS Proxy Over SSH
Mallory is a HTTP/HTTPS proxy over SSH tool. Installation Local machine: go get github.com/justmao945/mallory/cmd/malloryRemote server: need our old friend sshd Configueration Config File Default path is $HOME/.config/mallory.json, can be set when start program mallory -config path/to/config.json Content: id_rsa is the path to our private key file, can be generated by ssh-keygenlocal_smart is the local address to serve HTTP proxy with smart detection of destination hostlocal_normal is similar to local_smart but send all traffic...
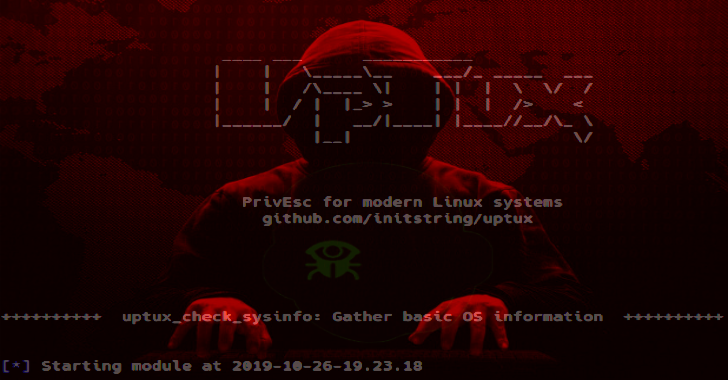
Uptux : Linux Privilege Escalation Checks
Uptux is a specialized privilege escalation checks for Linux systems. Implemented so far: Writable systemd paths, services, timers, and socket unitsDisassembles systemd unit files looking for: References to executables that are writableReferences to broken symlinks pointing to writeable directoriesRelative path statementsUnix socket files that are writeable (sneaky APIs) Writable D-Bus pathsOverly permissive D-Bus service settingsHTTP APIs running as root and responding on...
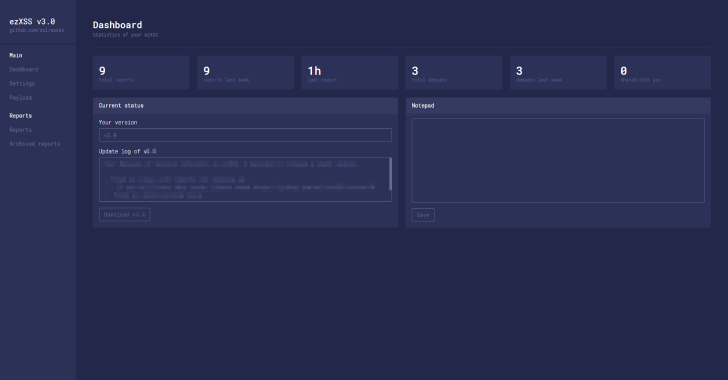
ezXSS : Easy Way For Penetration Testers & Bug Bounty Hunters
ezXSS is an easy way for penetration testers and bug bounty hunters to test (blind) Cross Site Scripting. Current Features Some features ezXSS has Easy to use dashboard with statics, payloads, view/share/search reports and morePayload generatorInstant email alert on payloadCustom javascript payloadEnable/Disable screenshotsPrevent double payloads from saving or alertingBlock domainsShare reports with a direct link or with other ezXSS usersEasily manage...
Fail2Ban : Daemon To Ban Hosts That Cause Multiple Authentication Errors
Fail2Ban scans log files like /var/log/auth.log and bans IP addresses conducting too many failed login attempts. It does this by updating system firewall rules to reject new connections from those IP addresses, for a configurable amount of time. Fail2Ban comes out-of-the-box ready to read many standard log files, such as those for sshd and Apache, and is easily configured to read...
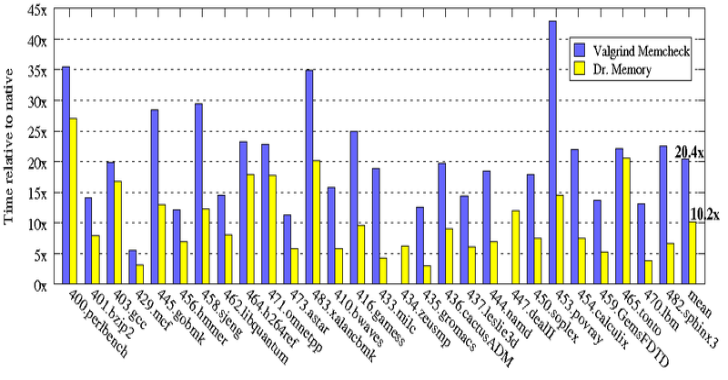
DrMemory : Memory Debugger for Windows, Linux, Mac & Android
DrMemory is a memory monitoring tool capable of identifying memory-related programming errors such as accesses of uninitialized memory, accesses to unaddressable memory (including outside of allocated heap units and heap underflow and overflow), accesses to freed memory, double frees, memory leaks, and (on Windows) handle leaks, GDI API usage errors, and accesses to un-reserved thread local storage slots. DrMemory operates...















%20-%20BufferOverflowNonPagedPoolNx%20Exploit.webp)