Red Canary Mac Monitor is an advanced, stand-alone system monitoring tool tailor-made for macOS security research, malware triage, and system troubleshooting. Harnessing Apple Endpoint Security (ES), it collects and enriches system events, displaying them graphically, with an expansive feature set designed to surface only the events that are relevant to you. The telemetry collected includes process, interprocess, and file events in addition to rich metadata, allowing users to contextualize events and tell a story with ease. With an intuitive interface and a rich set of analysis features, Red Canary Mac Monitor was designed for a wide range of skill levels and backgrounds to detect macOS threats that would otherwise go unnoticed. As part of Red Canary’s commitment to the research community, the Mac Monitor distribution package is available to download for free.
Requirements
- Processor: We recommend an
Apple Siliconmachine, butIntelworks too! - System memory:
4GB+is recommended - macOS version:
13.1+(Ventura)
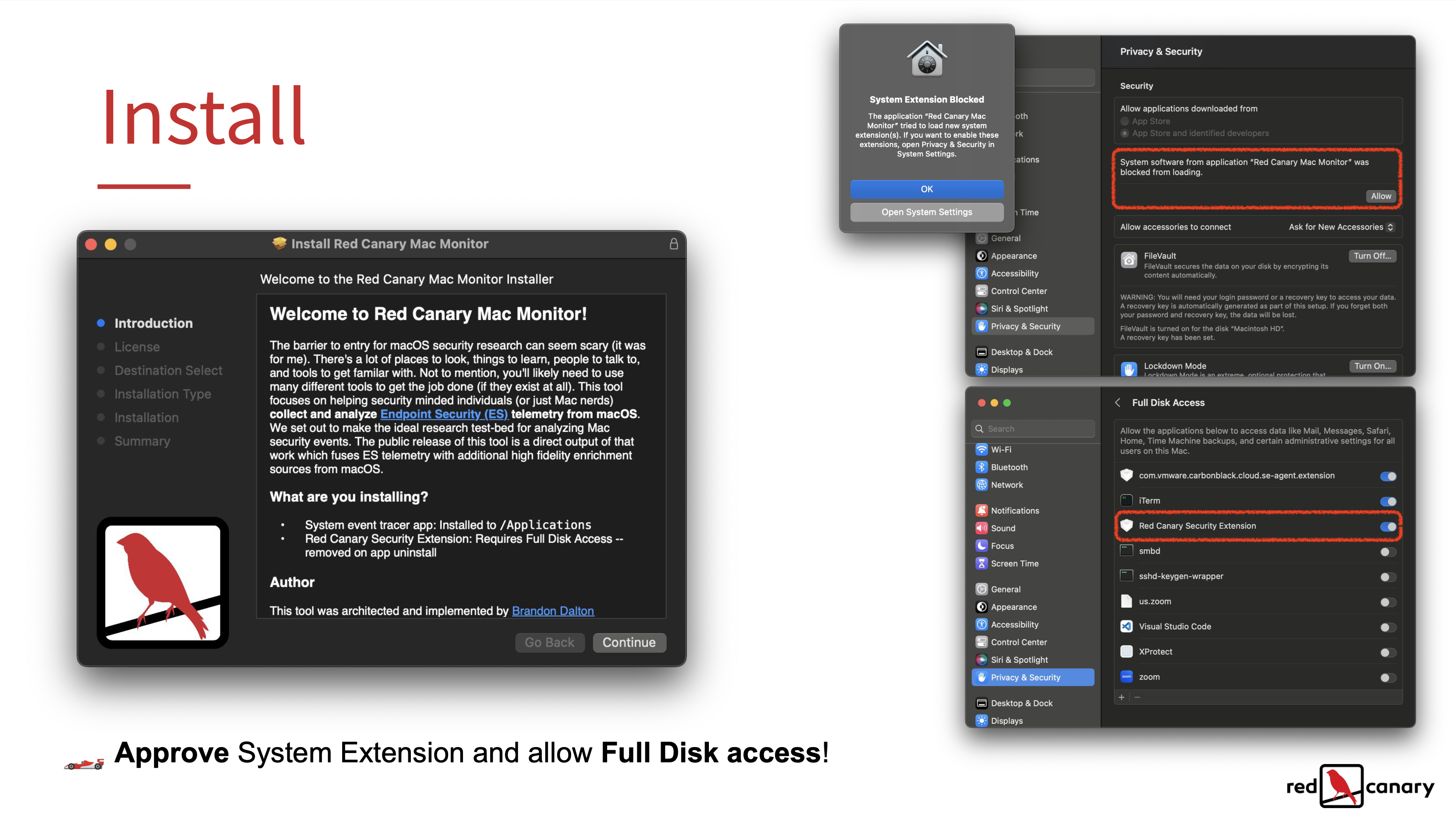
How can I install this thing?
- Go to the releases section and download the latest installer: https://github.com/redcanaryco/mac-monitor/releases
- Open the app:
Red Canary Mac Monitor.app - You’ll be prompted to “Open System Settings” to “Allow” the System Extension.
- Next, System Settings will automatically open to
Full Disk Access— you’ll need to flip the switch to enable this for theRed Canary Security Extension. Full Disk Access is a requirement of Endpoint Security. - ????️ Click the “Start” button in the app and you’ll be prompted to reopen the app. Done!
Install footprint
- Event monitor app which establishes an XPC connection to the Security Extension:
/Applications/Red Canary Mac Monitor.appw/signing identifier ofcom.redcanary.agent. - Security Extension:
/Library/SystemExtensions/../com.redcanary.agent.securityextension.systemextensionw/signing identifier ofcom.redcanary.agent.securityextension.systemextension.
For More Click Here



























.webp)