Seccomp provide powerful tools for seccomp analysis. This project is targeted to (but not limited to) analyze seccomp sandbox in CTF pwn challenges. Some features might be CTF-specific, but still useful for analyzing seccomp in real-case.
Features
- Dump – Automatically dumps seccomp-bpf from execution file(s).
- Disasm – Converts bpf to human readable format.
- Simple decompile.
- Display syscall names and arguments when possible.
- Colorful!
- Asm – Write seccomp rules is so easy!
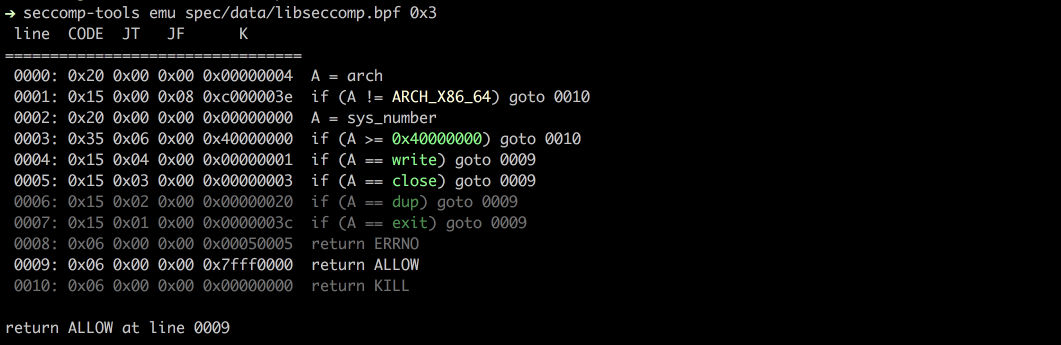
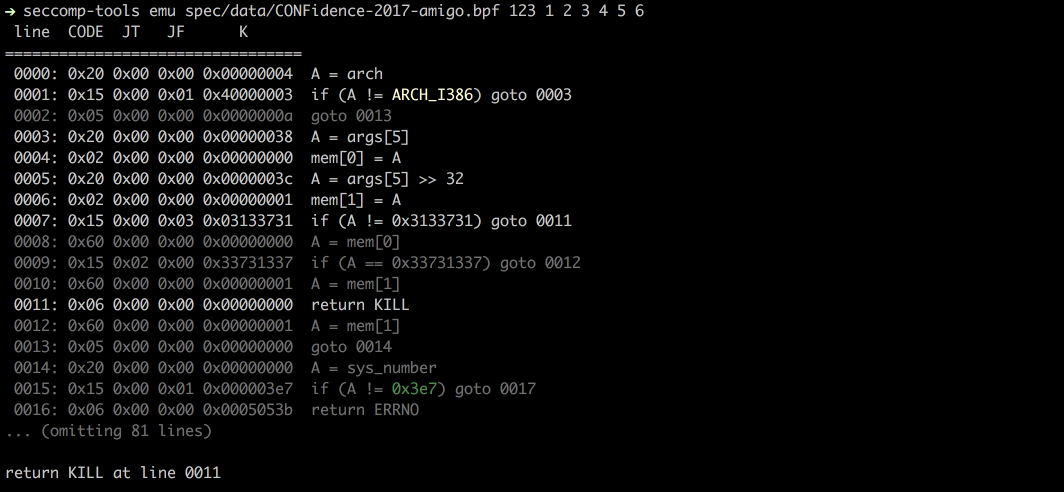
- Emu – Emulates seccomp rules.
- Supports multi-architectures.
Installation
Available on RubyGems.org!
$ gem install seccomp-tools
If you failed when compiling, try:
sudo apt install gcc ruby-dev
and install seccomp-tools again.
Also Read – SQLMap : Automatic SQL Injection & Database Takeover Tool
Command Line Interface
$ seccomp-tools –help
==>Usage: seccomp-tools [–version] [–help] []
==>List of commands:
# asm Seccomp bpf assembler.
# disasm Disassemble seccomp bpf.
# dump Automatically dump seccomp bpf from execution file(s).
# emu Emulate seccomp rules.
# See ‘seccomp-tools –help’ to read about a specific subcommand.
==>$ seccomp-tools dump –help
# dump – Automatically dump seccomp bpf from execution file(s).
==>Usage: seccomp-tools dump [exec] [options]
# -c, –sh-exec Executes the given command (via sh).
# Use this option if want to pass arguments or do pipe things to the execution file.
# e.g. use -c "./bin > /dev/null" to dump seccomp without being mixed with stdout.
# -f, –format FORMAT Output format. FORMAT can only be one of Default: disasm
# -l, –limit LIMIT Limit the number of calling “prctl(PR_SET_SECCOMP)”.
# The target process will be killed whenever its calling times reaches LIMIT.
# Default: 1
-o, –output FILE Output result into FILE instead of stdout.
# If multiple seccomp syscalls have been invoked (see –limit),
# results will be written to FILE, FILE_1, FILE_2.. etc.
# For example, “–output out.bpf” and the output files are out.bpf, out_1.bpf, …
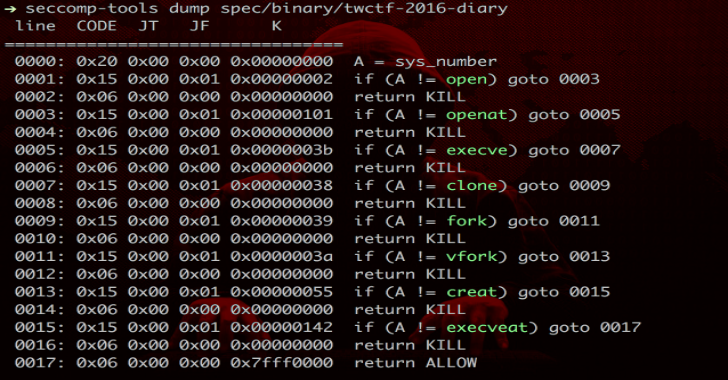
Dump
Dumps the seccomp bpf from an execution file. This work is done by the ptrace syscall.
NOTICE: beware of the execution file will be executed.
$ file spec/binary/twctf-2016-diary
spec/binary/twctf-2016-diary: ELF 64-bit LSB executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/l, for GNU/Linux 2.6.24, BuildID[sha1]=3648e29153ac0259a0b7c3e25537a5334f50107f, not stripped
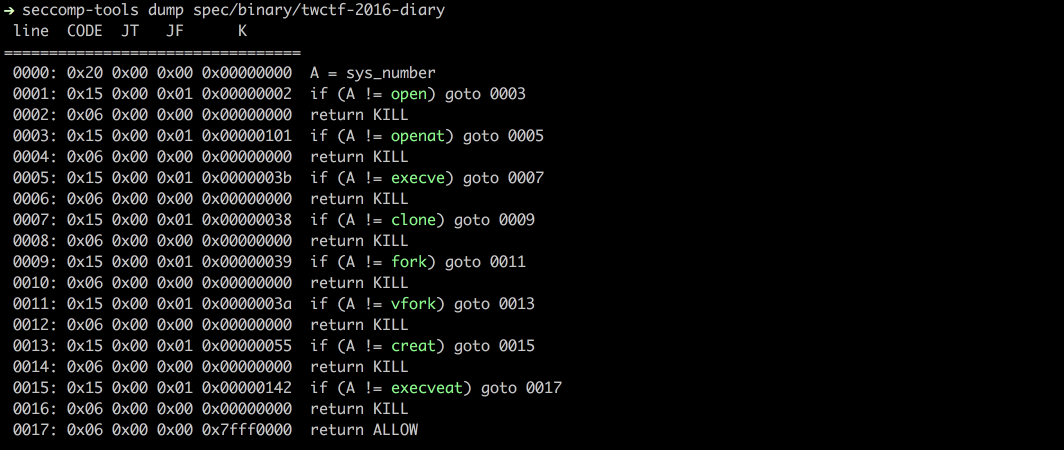
$ seccomp-tools dump spec/binary/twctf-2016-diary
line CODE JT JF K
=================================
0000: 0x20 0x00 0x00 0x00000000 A = sys_number
0001: 0x15 0x00 0x01 0x00000002 if (A != open) goto 0003
0002: 0x06 0x00 0x00 0x00000000 return KILL
0003: 0x15 0x00 0x01 0x00000101 if (A != openat) goto 0005
0004: 0x06 0x00 0x00 0x00000000 return KILL
0005: 0x15 0x00 0x01 0x0000003b if (A != execve) goto 0007
0006: 0x06 0x00 0x00 0x00000000 return KILL
0007: 0x15 0x00 0x01 0x00000038 if (A != clone) goto 0009
0008: 0x06 0x00 0x00 0x00000000 return KILL
0009: 0x15 0x00 0x01 0x00000039 if (A != fork) goto 0011
0010: 0x06 0x00 0x00 0x00000000 return KILL
0011: 0x15 0x00 0x01 0x0000003a if (A != vfork) goto 0013
0012: 0x06 0x00 0x00 0x00000000 return KILL
0013: 0x15 0x00 0x01 0x00000055 if (A != creat) goto 0015
0014: 0x06 0x00 0x00 0x00000000 return KILL
0015: 0x15 0x00 0x01 0x00000142 if (A != execveat) goto 0017
0016: 0x06 0x00 0x00 0x00000000 return KILL
0017: 0x06 0x00 0x00 0x7fff0000 return ALLOW
$ seccomp-tools dump spec/binary/twctf-2016-diary -f inspect
“\x20\x00\x00\x00\x00\x00\x00\x00\x15\x00\x00\x01\x02\x00\x00\x00\x06\x00\x00\x00\x00\x00\x00\x00\x15\x00\x00\x01\x01\x01\x00\x00\x06\x00\x00\x00\x00\x00\x00\x00\x15\x00\x00\x01\x3B\x00\x00\x00\x06\x00\x00\x00\x00\x00\x00\x00\x15\x00\x00\x01\x38\x00\x00\x00\x06\x00\x00\x00\x00\x00\x00\x00\x15\x00\x00\x01\x39\x00\x00\x00\x06\x00\x00\x00\x00\x00\x00\x00\x15\x00\x00\x01\x3A\x00\x00\x00\x06\x00\x00\x00\x00\x00\x00\x00\x15\x00\x00\x01\x55\x00\x00\x00\x06\x00\x00\x00\x00\x00\x00\x00\x15\x00\x00\x01\x42\x01\x00\x00\x06\x00\x00\x00\x00\x00\x00\x00\x06\x00\x00\x00\x00\x00\xFF\x7F”
$ seccomp-tools dump spec/binary/twctf-2016-diary -f raw | xxd
00000000: 2000 0000 0000 0000 1500 0001 0200 0000 ……………
00000010: 0600 0000 0000 0000 1500 0001 0101 0000 …………….
00000020: 0600 0000 0000 0000 1500 0001 3b00 0000 …………;…
00000030: 0600 0000 0000 0000 1500 0001 3800 0000 …………8…
00000040: 0600 0000 0000 0000 1500 0001 3900 0000 …………9…
00000050: 0600 0000 0000 0000 1500 0001 3a00 0000 …………:…
00000060: 0600 0000 0000 0000 1500 0001 5500 0000 …………U…
00000070: 0600 0000 0000 0000 1500 0001 4201 0000 …………B…
00000080: 0600 0000 0000 0000 0600 0000 0000 ff7f …………….
Development
I recommend to use rbenv for your Ruby environment.
Setup
- Install bundler
$ gem install bundler
- Clone the source
$ git clone https://github.com/david942j/seccomp-tools && cd seccomp-tools
- Install dependencies
$ bundle install
Run Tests
$ bundle exec rake
Screenshots
Dump
Emu













.webp)