APPLICATIONS
HOT NEWS
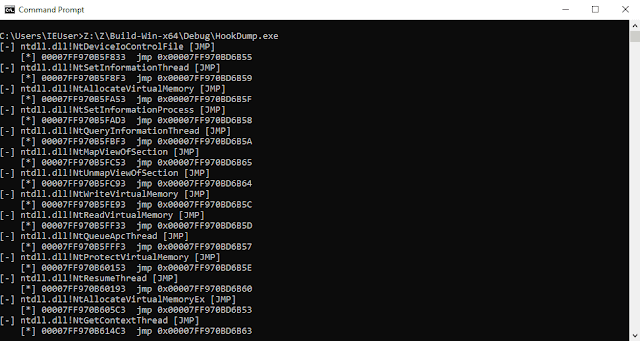
HookDump : Security Product Hook Detection
HookDump is a tool for security product hook detection.
Building Source
In order to build this you will need Visual Studio 2019 (community edition is fine)...
We provide you with the latest Kali Linux & Penetration testing tools.
Contact us: admin@kalilinuxtutorials.com
© @Kali Linux Tutorials - 2024









.webp)