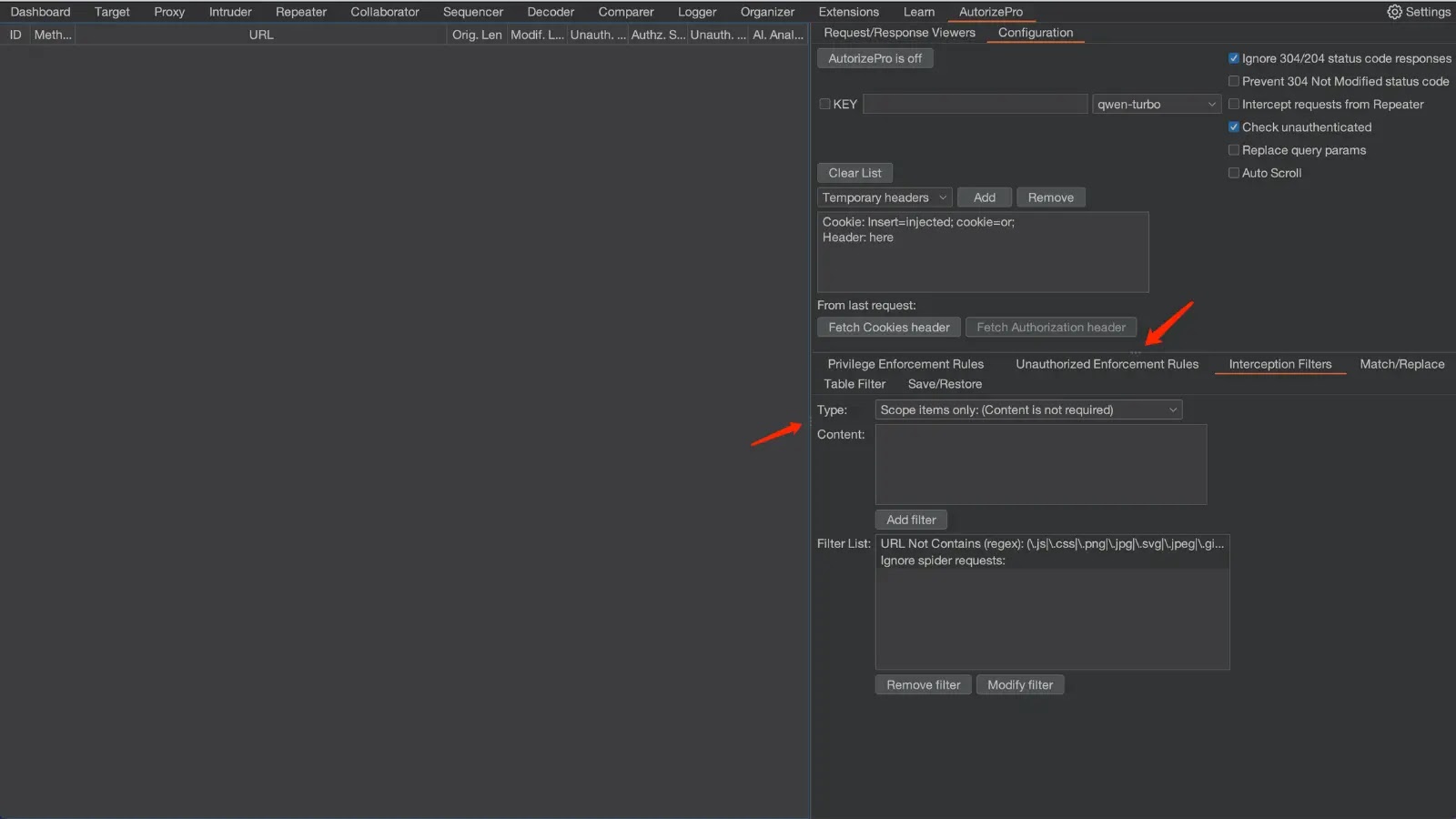
APPLICATIONS
HOT NEWS
Polars : A High-Performance DataFrame Library
Polars is a cutting-edge DataFrame library designed for high-speed data manipulation and analysis.
Written in Rust and leveraging the Apache Arrow columnar format, Polars...
© kalilinuxtutorials.com 2025