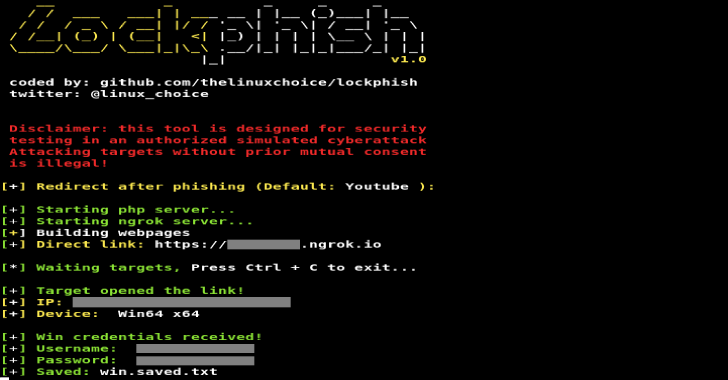
APPLICATIONS
HOT NEWS
Most Popular Hacking Tools in 2018
Hacking tools used by security professionals to detect vulnerabilities in network and applications. Here you can find the Comprehensive Penetration testing tools list that...
© kalilinuxtutorials.com 2025