Perform a Smurf attack and a Distributed Denial of Service (DDoS) attack on a on whole IPv6 network using smurf6
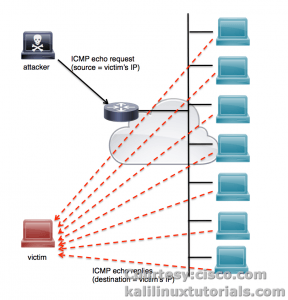
Smurf6 is a tool to perform a smurf attack on IPv6 network. A smurf attack is a type of DOS attack where an attacher pings the Broadcast address with a spoofed address of a victim. Eventually all nodes in the network gets an ICMP ping request from the victim’s ip address. As a result all the hosts reply back to the victim IP-address making it a DDoS attack. In IPv4 this attack will not be successful in most of the modern routers & switches. But iPv6 is still vulnerable. Take a look at the following image for better understanding of this attack.
Smurf6 sends a whole lot of ICMP Ping requests to the multicast address in IPv6(Instead of Broadcast in IPv4) with the spoofed IP address of the victim. Eventually all the nodes gives echo replies to the victim host making it a DDoS.
Reference : http://searchsecurity.techtarget.com/definition/smurfing
http://www.cisco.com/web/about/security/intelligence/guide_ddos_defense.html
Homepage: https://www.thc.org/thc-ipv6/
Note: This tutorial was written when Kali 1.0.9 was the latest. In newer versions (Kali Sana & Kali Rolling) the command has changed to atk6-tool. For example you are using smurf6, in newer version becomes atk6-smurf6.
Options
Syntax: smurf6 interface victim-ip [multicast-network-address]
Example: smurf6 eth0 8ea0::001a [8ea0::00/64]
Lab : Perform a Smurf attack on an IPv6 network.
This is pretty simple with smurf6. All you have to do is to find out the network(IPv6) range, and some hosts. Even if you didn’t get any hosts, smurf6 works perfect flooding the entire network with ICMP6 requests. Check out the post on passive discovery to see how to discover IPv6 hosts & network.
https://kalilinuxtutorials.com/ig/passive_discovery6/
Note: This is a vandalizing DDoS attack. The authors of this article or the tool itself are not responsible in any ways for the consequences faced if misused. Use this only on a test network or with a Proper Agreement if in case you want to execute on a live environment.
Scenario: To be frank with you this is very much vandalizing. This crashes all systems in the target network and not only the victim host. For this simple tutorial I had to prepare a lot because the carrying out this attack kills everything in the network. So I had to move into the live machine in order to complete this tutorial. Lets see how.
Coming to the point, I have 2 VMs and a network which supports both IPv4 & IPv6
- IPv4 Network Range : 192.168.0.1/24
- IPv4 Network Range : fc00::00/64
- Attacker Kali Linux (VM): IP:192.168.0.102/24, fc00::05/64
- Victim RHEL 7 (VM): IP: 192.168.0.110/24, fc00::03/64
- Windows 8.1 PRO (Real System): IP: 192.168.0.100/24, fc00::04/64
Let’s proceed.
command: smurf6 eth0<replace with yours> fc00::03 [fc00::00/64] <replace with yours>
Wait for 1 minute and you can see everyone in the office going crazy…!
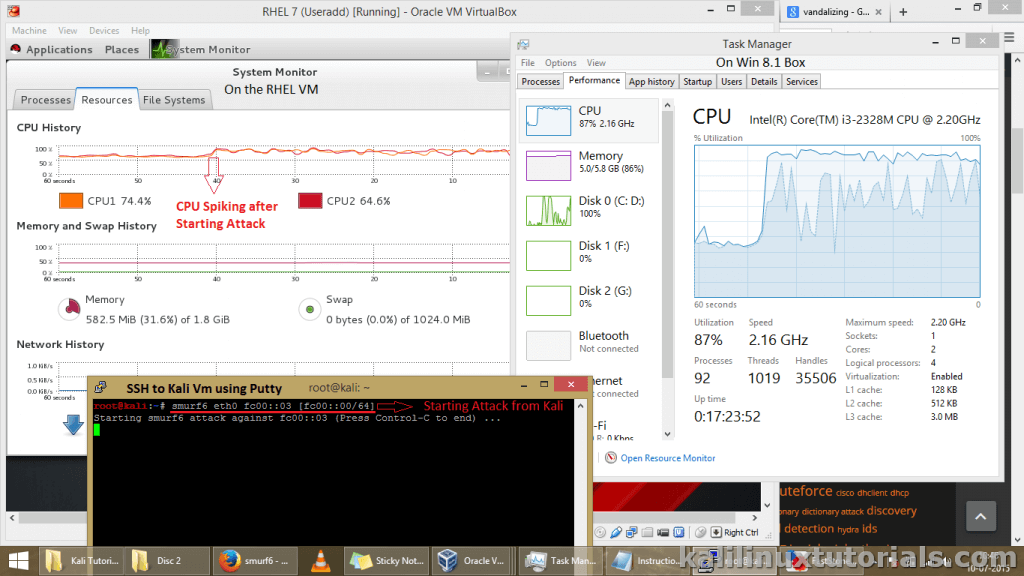
I was able to take only one screenshot. Also, I was performing the attack by taking a SSH session from the Kali box. Otherwise every VMs would crash including my real machine and nothing I could do expect but to take off the power cable. Et… Voila…
Take a good look at the following screenshot, observe my notations on each Windows. You can see the CPU spiking after the attack has been launched.
I am not sure of the reason Offsec included this under Stress testing. Maybe, we can check how much the network & network equipments can take by observing the time taken for every nodes on the network to crash. Or if the network is large and contains large no of hosts & services like Windows AD etc, we can test whether the gateway can handle everything at once or whether something is done to prevent pinging to broadcast address. For now the simplest countermeasure for this attack is to stick with IPv4 and disable IPv6 on internal networks.
Well Enjoy IPv6 Smurfing while it Lasts and don’t forget to subscribe & follow us.












.png)
