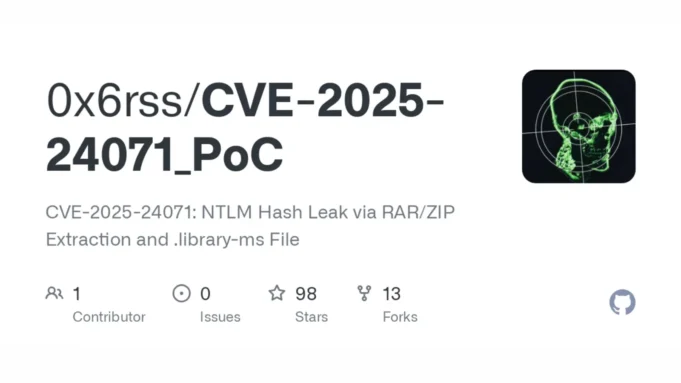
CVE-2025-24071 is a critical vulnerability in Microsoft Windows File Explorer that allows attackers to capture NTLM hashed passwords without user interaction.
This vulnerability exploits the automatic processing of specially crafted .library-ms files within compressed archives like RAR or ZIP.
The Proof of Concept (PoC) tool, CVE-2025-24071_PoC, demonstrates how attackers can exploit this flaw using a simple Python script.
Functionality Of The CVE-2025-24071_PoC Tool
- Generation of Malicious .library-ms Files: The PoC tool generates a
.library-msfile containing a malicious SMB path. This file is then embedded within a RAR or ZIP archive. - Automatic NTLM Hash Leak: When the archive is extracted, Windows Explorer automatically processes the
.library-msfile. This triggers an NTLM authentication handshake with an attacker-controlled SMB server, leaking the victim’s NTLMv2 hash without requiring any user interaction beyond extracting the file. - User Input Requirements: The tool requires minimal input from the attacker, including the target file name and the attacker’s IP address. This information is entered when running the Python script: python
python poc.py # Enter file name: your_file_name # Enter IP: attacker_IP - Exploitation Potential: The leaked NTLM hashes can be used for pass-the-hash attacks or offline NTLM hash cracking, significantly compromising network security.
Implications And Mitigation
- Active Exploitation: The vulnerability is being actively exploited in the wild, with threat actors like “Krypt0n” linked to its exploitation. This underscores the urgency of patching affected systems.
- Mitigation Measures: Microsoft addressed CVE-2025-24071 in its March 2025 Patch Tuesday updates. Users are advised to apply these patches immediately to prevent exploitation.
In summary, the CVE-2025-24071_PoC tool highlights the severity of the NTLM hash leak vulnerability in Windows File Explorer, emphasizing the need for prompt patching and security updates to protect against such threats.