Wi-Fi tools keep getting more and more accessible to beginners, and the Ehtools Framework is a framework of serious penetration tools that can be explored easily from within it.
This powerful and simple tool can be used for everything from installing new add-ons to grabbing a WPA handshake in a matter of seconds. Plus, it’s easy to install, set up, and utilize.
How to install?
cd ehtools
chmod +x install.sh
./install.sh
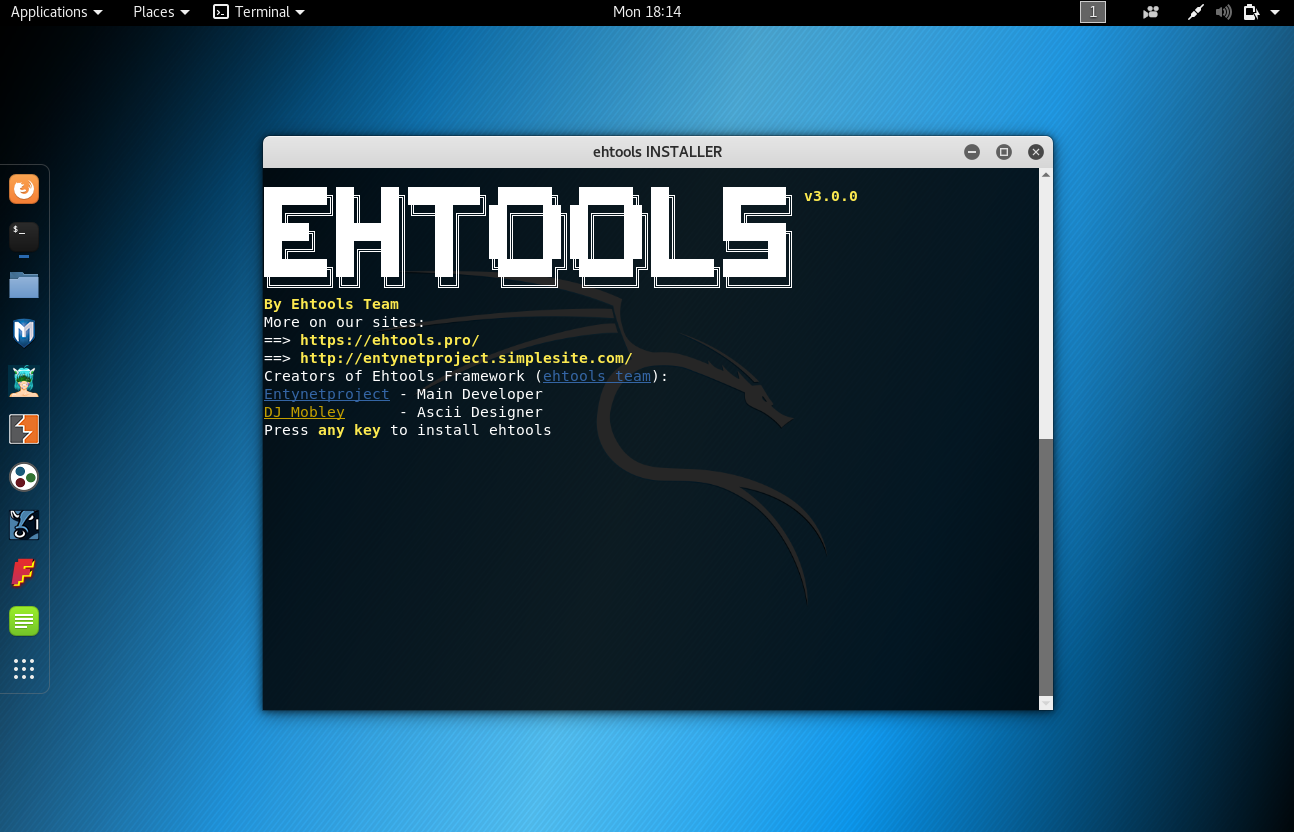
Selecting version of framework
INFO: After executing install.sh it will be ask you to select version of Ehtools Framework – PRO os LITE. Select LITE if you did not buy Ehtools Framework PRO. If you bought Ehtools Framework PRO, select PRO.
./install.sh
What version of Ehtools Framework do you want to install?(pro/lite):
If you did not buy Ehtools Framework PRO, select LITE! If you bought Ehtools Framework PRO, select PRO! (version)>
If you select Ehtools Framework PRO, you will need to activate it with your Ehtools Activation Key that you need to bought on the ehtools site. If you have Ehtools Activation Key, read the following instructions.
Also Read – Constellation : A Graph-Focused Data Visualisation & Interactive Analysis Application
How to activate ehtools PRO?
This key you can buy on the ehtools site for one dollar! This key is used to activate ehtools PRO enter it in the input field of the activation key in the file install.sh and then you can install ehtools and use it only for educational purposes!
WARNING: The key works only one week then it changes! You need to have time to enter it before it is updated!
./install.sh
- Enter your ehtools activation key!
- You can buy it on the ehtools site!
- (activation_key)>
Also, we do not recommend to change the source code of ehtools because it is very complex and you can mess up something and disrupt the framework!
WARNING: We do not recommend to change ehtools source code because you can disrupt framework!
How to uninstall ehtools ?
ehtools -r
WARNING: Do not do it if you want to reinstall ehtools PRO which you bought, do not do it because you will need to buy it one more time!
Attacking frameworks
Most new Wi-Fi hacking tools rely on many of the same underlying attacks, and scripts that automate using other more familiar tools like Aireplay-ng are often referred to as frameworks. These frameworks try to organize tools in smart or useful ways to take them a step beyond the functionality or usability of the original program.
An excellent example of this are programs that integrate scanning tools like Airodump-ng, attacks like WPS Pixie-Dust, and cracking tools like Aircrack-ng to create an easy-to-follow attack chain for beginners. Doing this makes the process of using these tools easier to remember and can be seen as sort of a guided tour. While each of these attacks is possible without the hand-holding, the result can be faster or more convenient than trying to do so yourself.
An example of this we’ve covered is the Airgeddonframework, a wireless attack framework that does useful things like automating the target selection process and eliminating the time a user spends copying and pasting information between programs. This saves valuable time for even experienced pentesters but has the disadvantage of preventing beginners from understanding what’s happening “under the hood” of the attack. While this is true, most of these frameworks are fast, efficient, and dead simple to use, enabling even beginners to take on and disable an entire network.
UX/UI impruvements for beginners
The Ehtools Framework starts by merely typing the letter ehtools or eht into a terminal window, then it asks for the name of your network interfaces after the first run.
It uses the names you supply to connect to the tools needed to execute any attacks you select. Aside from that initial input, the majority of the possible attacks can be performed merely by choosing the option number from the menu.
This means you can grab a network handshake or download a new hacking tool like Pupy by just selecting from one of the menu options.
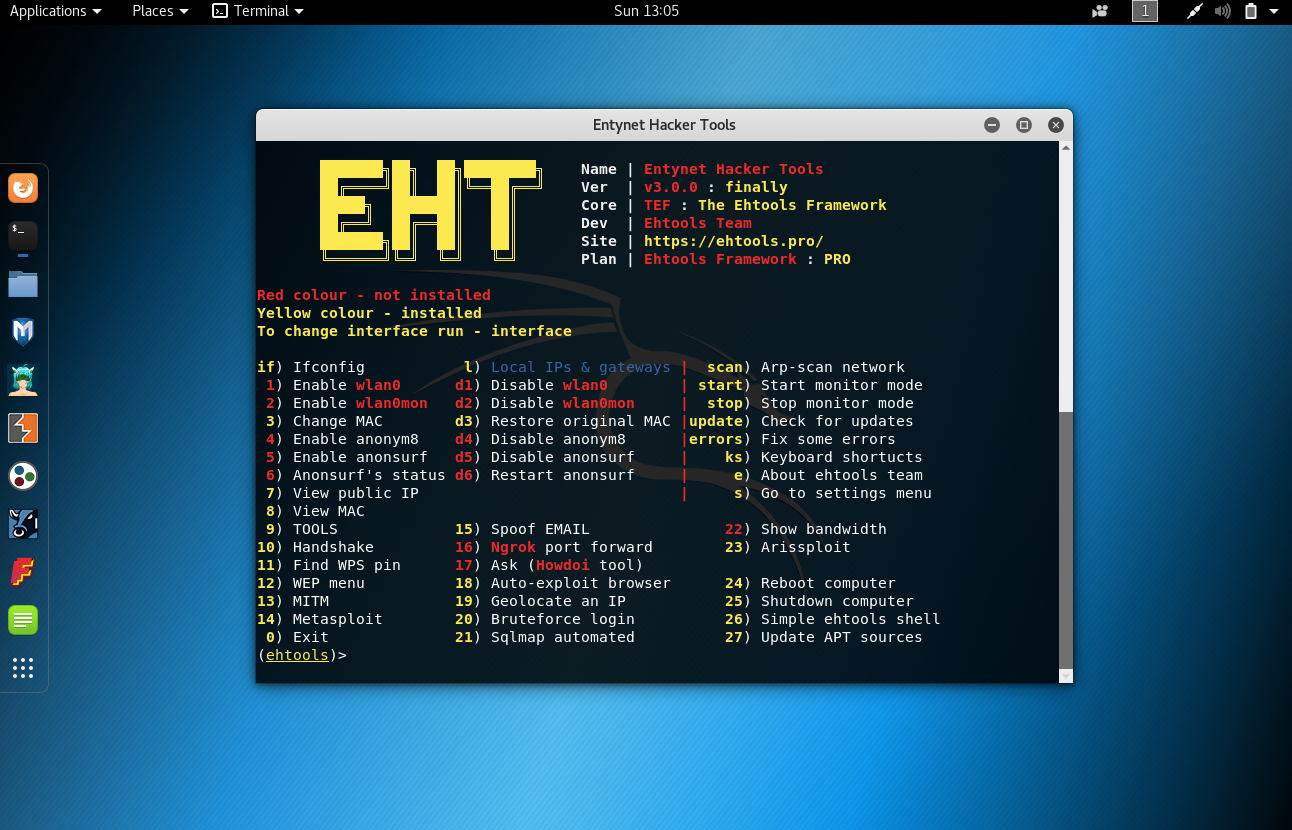
Use basic networking tools
To begin, we can access data about the network we’re currently connected to, as well as any network interfaces, from the main menu. Here, we can find local information by just typing l to pull up local IP information, as seen below.
This allows us to do things like scan the network for other devices. This part of Ehtools Framework gives us better visibility on a network and situational awareness of what devices are around us. The various information can be broken down as follows:
(ehtools)> if
INFO: Runs ifconfig and gives the names and information about all network devices.
(ehtools)> 1
INFO: Enable wlan0.
(d1 disables it)
(ehtools)> 2
INFO: Enable wlan0mon.
(d2 disables it)
(ehtools)> 3
INFO: Randomize or set the MAC address to a specific value.
(ehtools)> 7
INFO: View the public IP address your computer is leaving on sites you visit.
(ehtools)> 19
INFO: Look up the physical address of a given IP address to determine it’s relative location.
(ehtools)> scan
INFO: Start an ARP scan on the network to discover nearby devices.
(ehtools)> start
INFO: Start monitor mode on the wireless network adapter.
(ehtools)> stop
INFO: Stop wireless monitor mode on the network adapter.\
Install new tools
Part of the fun of Ehtools Framework is how easy it is to add new tools to our arsenal. To demonstrate this, let’s download Pupy, a Python-based RAT designed to take control of other computers on the network. We can select option 9 to access the list of tools in Ehtools Framework.
INFO: Our framework has more than 100 packages in ehtools archive (on server this archive: 2.3 Tb)!
From the next menu, the tools are broken down into major categories, with options for managing the installation of scripts. The options presented are:
- Wi-Fi tools (tools for attacking wireless networks).
INFO: Wi-Fi options this is tools for attacking wireless networks and network databases.
- Remote access (tools for getting remote access to other devices and remotely managing them).
INFO: Remote access means tools for getting access to other devices and remotely managing them.
- Information gathering (collecting intelligence on people or website).
INFO: Information gathering tools, tools for collecting intelligence on peaple or website.
- Website tools (tools for exploiting or attacking sites).
INFO: Website tools, tools for exploiting or attacking sites and network databases.
- Other (a miscellaneous collection of other hacking tools)
INFO: Other tools this is collection of miscellaneous hacking tools.
You can also manage your installed tools by accessing option 6. To download Pupy, we’ll go to option 2, which is remote access. Here, we will see a list of different tools for remote access, and we can select option 3 for Pupy.
INFO: Ehtools quick access, this is when you run ehtools and for example ehtools -r to remove ehtools!
Run it to open quick access menu:
ehtools -o
Run it to update ehtools:
ehtools -u
Run it to remove ehtools:
ehtools -r
Run it to make handshake:
ehtools -h
Run it to open WPS menu:
ehtools -w
INFO: For this shortcuts you will not need enter your ehtools password!
More than 58 tools for pentesting installed by default
INFO: More than 58 options installed by default you can find in ehtools, this is tools such as MetaSploit, WireShark and other tools!
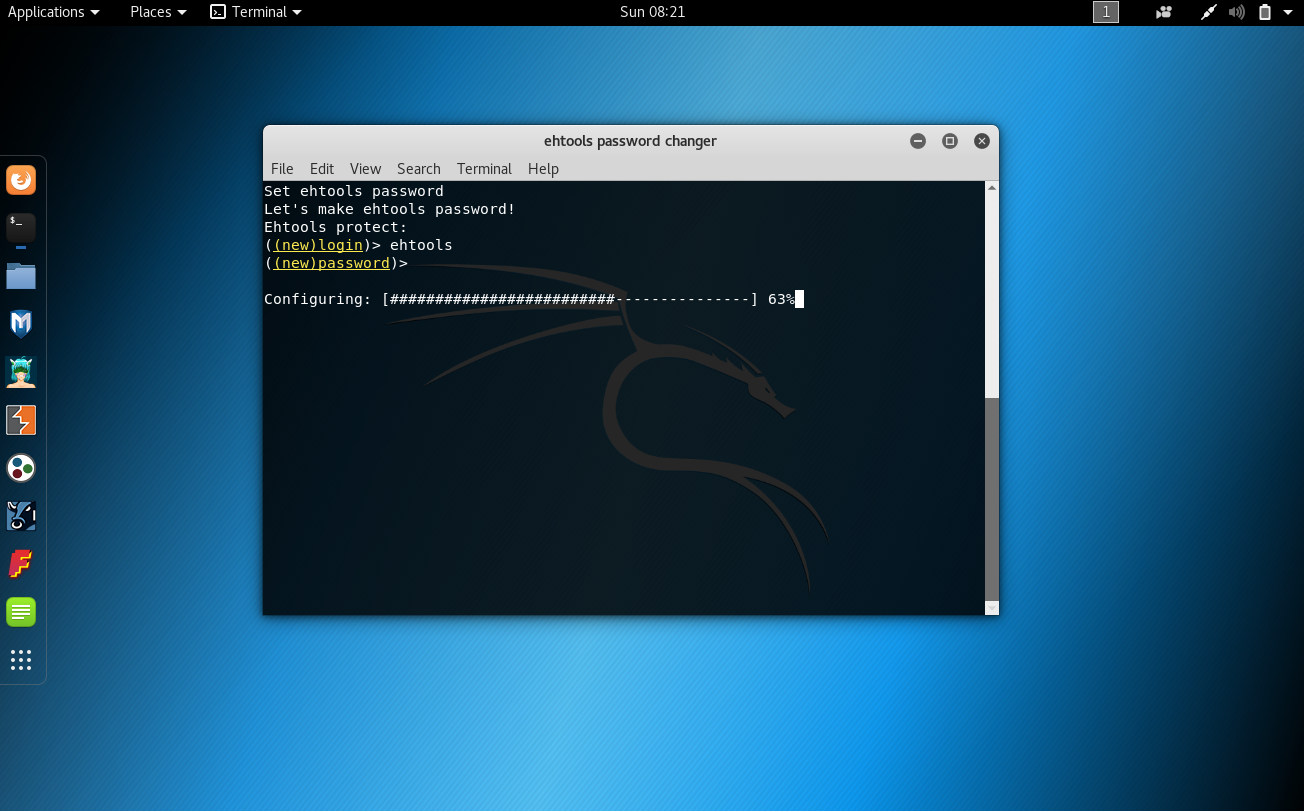
Password protection and config encryption
INFO: In version 2.1.6 we added pasword protection, we added it for users who think that his/her friend or parents will turn into ehtools and will remove or destroy it. Only for this people we create password protection for Ehtools Framework 🙂
Easy in learning and this is the best framework for beginners
INFO: Ehtools Framework’s TUI is very simple for beginners, you can start attack on the local network by choosing an option from main menu. It is very simple, is not it?
UX/UI impruvements for beginners
INFO: It uses the names you supply to connect to the tools needed to execute any attacks you select! Aside from that initial input, the majority of the possible attacks can be performed merely by choosing the option number from the menu. This means you can grab a network handshake or download a new hacking tool like Pupy by just selecting from one of the menu options!
More than 100 tools you can install from ehtools or ehtoolslite
INFO: Our framework has more than 100 packages in ehtools archive (on server this archive: 2.3 Tb)!
System Requirements
Full root access and access to /root folder
INFO: All ehtools files and folders will copy to /root, /bin and /etc system folders, for copy ehtools data to your system needed root access!
Bourne-again shell and Gnome-terminal shell
INFO: Bourne-again shell and Gnome-terminal shell needed for ehtools GUI and also without Gnome-terminall shell modules such as (eht1, eht2 and etc.) will not work!
Good internet connection for server support (only ehtools PRO)
INFO: The server support for ehtools PRO is one of system requirements, it is needed for collect information about ehtools crashes and it is also needed for check product status such as (you bought ehtools/you did not buy ehtools)
Uiecache – (uninstall ehtools cache) the utility that can help you to clean/uninstall ehtools cache like login logs or .config files!
Usage: uiecache [OPTION…]
Copyright (C) 2019, Entynetproject. All Rights Reserved.
–all Uninstall all ehtools cache.
(standart old uiecache)
–path Uninstall ehtools cache from your path.
(uninstall cache from path)
–restart Restart all ehtools processes and services.
(restart ehtools system)
–help Give this help list.
How to protect ehtools
Do it with install.sh:
COUNCIL: Create login and password from install.sh (defaults: login: ehtools password: sloothe)
Do it when you are going to exit from ehtools:
COUNCIL: When you are going to exit framework, exit with shortcuts – 0 or exit.
Do not do it when you are going to exit from ehtools:
WARNING: Do not just close ehtools window!