How Does a Firewall Work Step by Step? What Is a Firewall and How Does It Function?
Introduction
Every second, millions of data packets travel across the internet. These packets carry everything from emails and website data to confidential business transactions. Unfortunately, not all of this traffic is safe. Hackers, malware, and other cyber threats constantly attempt to infiltrate networks and steal valuable information.
One of the most important tools used to protect against these attacks is a firewall. A firewall acts as a gatekeeper that monitors and controls what enters and exits a network. In this article, you will learn exactly what a firewall is, how a firewall works step by step, and why it is so important for cybersecurity. This guide is designed for beginners and explained in a simple and practical way.
What Is a Firewall?
A firewall is a security system that sits between your internal network and the outside world. It inspects the data that flows in and out of your network and decides whether to allow or block it based on predefined rules.
Think of a firewall as a security guard standing at the entrance of a building. The guard checks the identification of everyone who tries to enter and denies access to anyone who is not authorized. Similarly, a firewall ensures that only safe and legitimate traffic can pass through while blocking harmful or suspicious traffic.
Main Functions of a Firewall
- Traffic Monitoring: Constantly observes all data entering and leaving the network.
- Access Control: Decides which data packets are allowed or blocked.
- Protection Against Threats: Stops hackers, viruses, and malware from entering.
- Logging and Reporting: Records activities for security analysis and audits.
Types of Firewalls
There are different types of firewalls used to provide varying levels of protection:
Packet-Filtering Firewalls
These are the simplest type. They inspect individual data packets and allow or block them based on set rules such as IP addresses, ports, and protocols.
Stateful Inspection Firewalls
These are more advanced. They not only check individual packets but also track ongoing connections to ensure that the traffic is part of a valid, established session.
Next-Generation Firewalls
Modern firewalls include features like deep packet inspection, application-level filtering, intrusion prevention, and real-time threat intelligence.
Proxy Firewalls
These act as intermediaries between users and the internet. They mask the internal network and filter traffic at the application layer.
How Does a Firewall Work Step by Step?
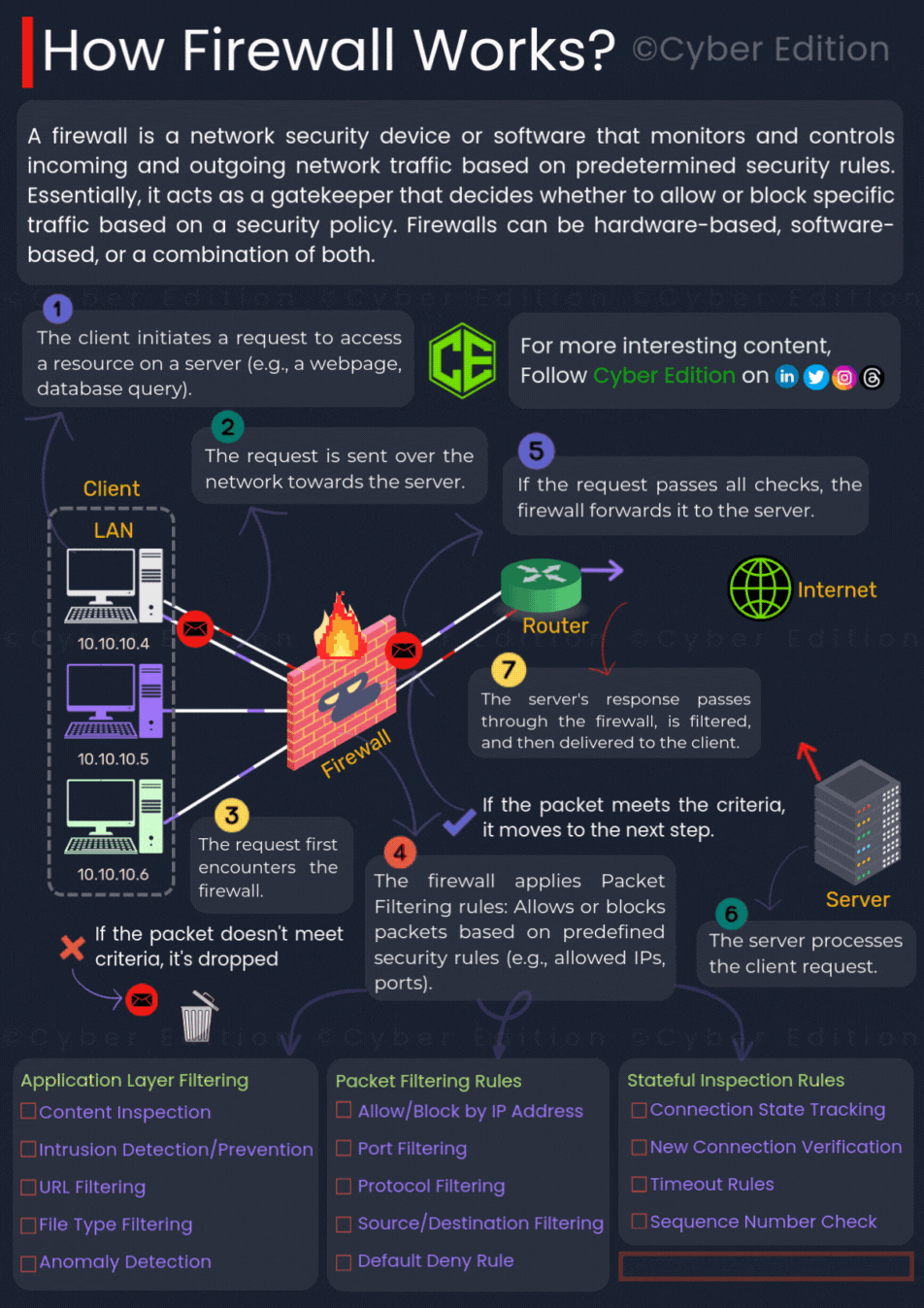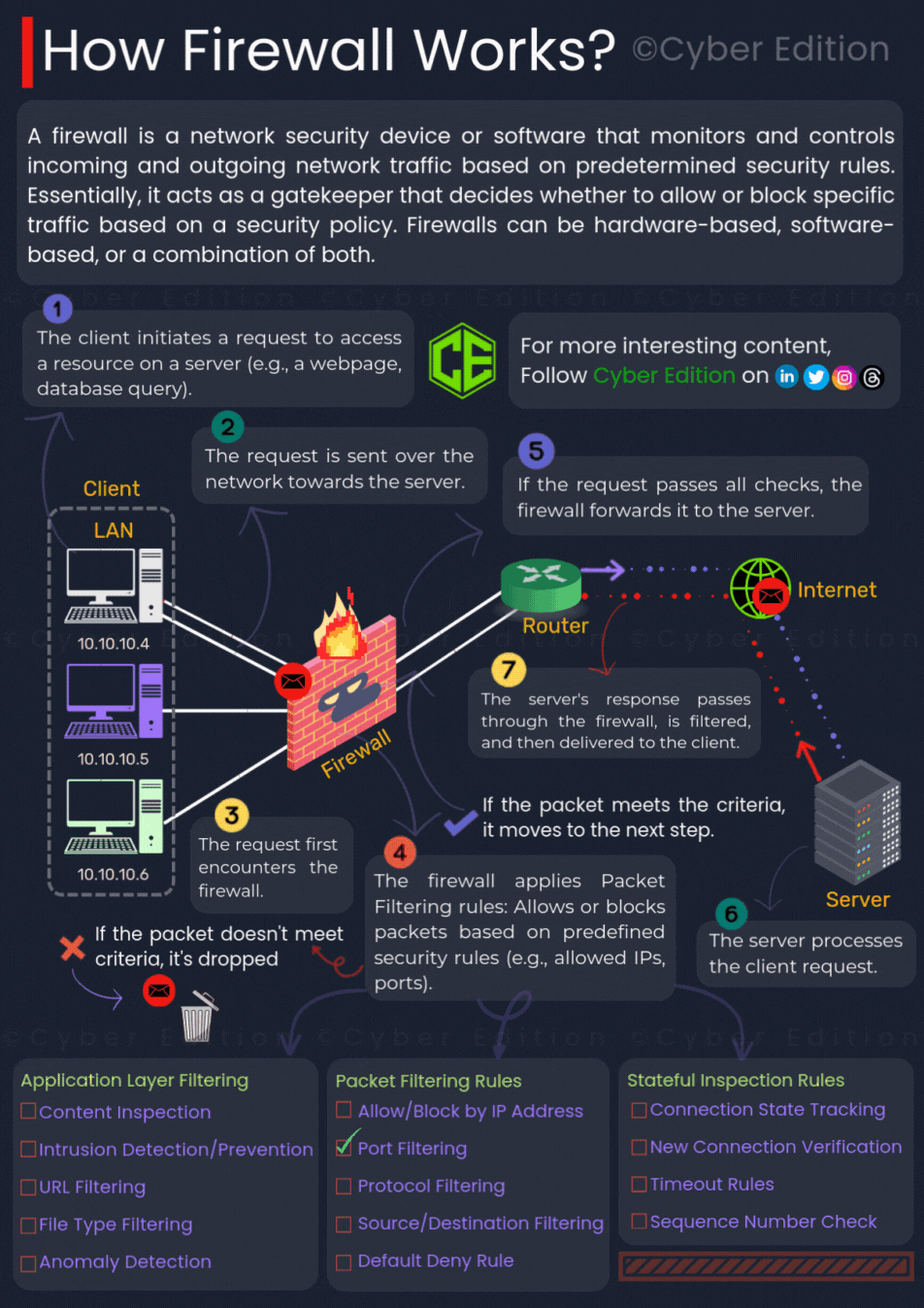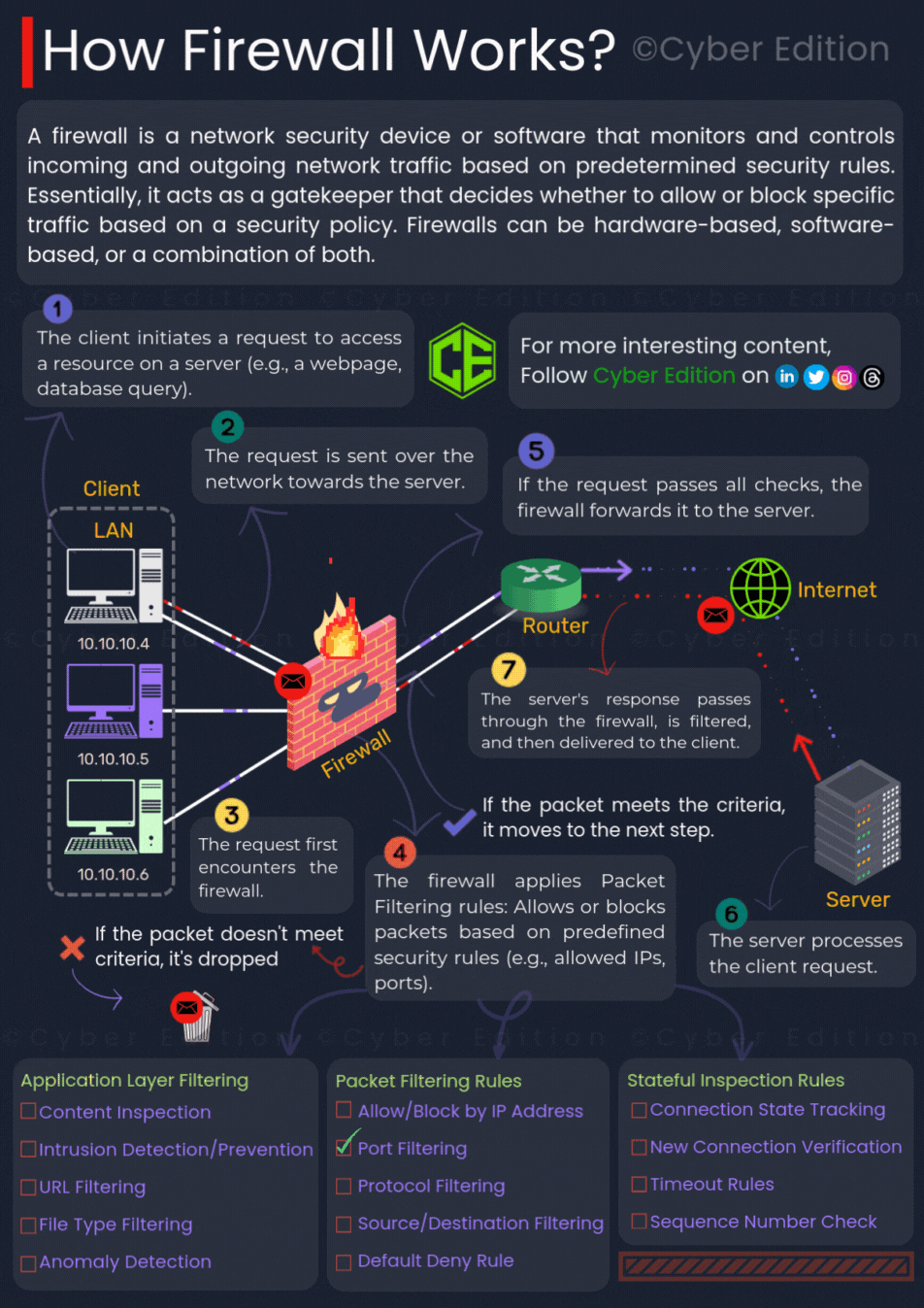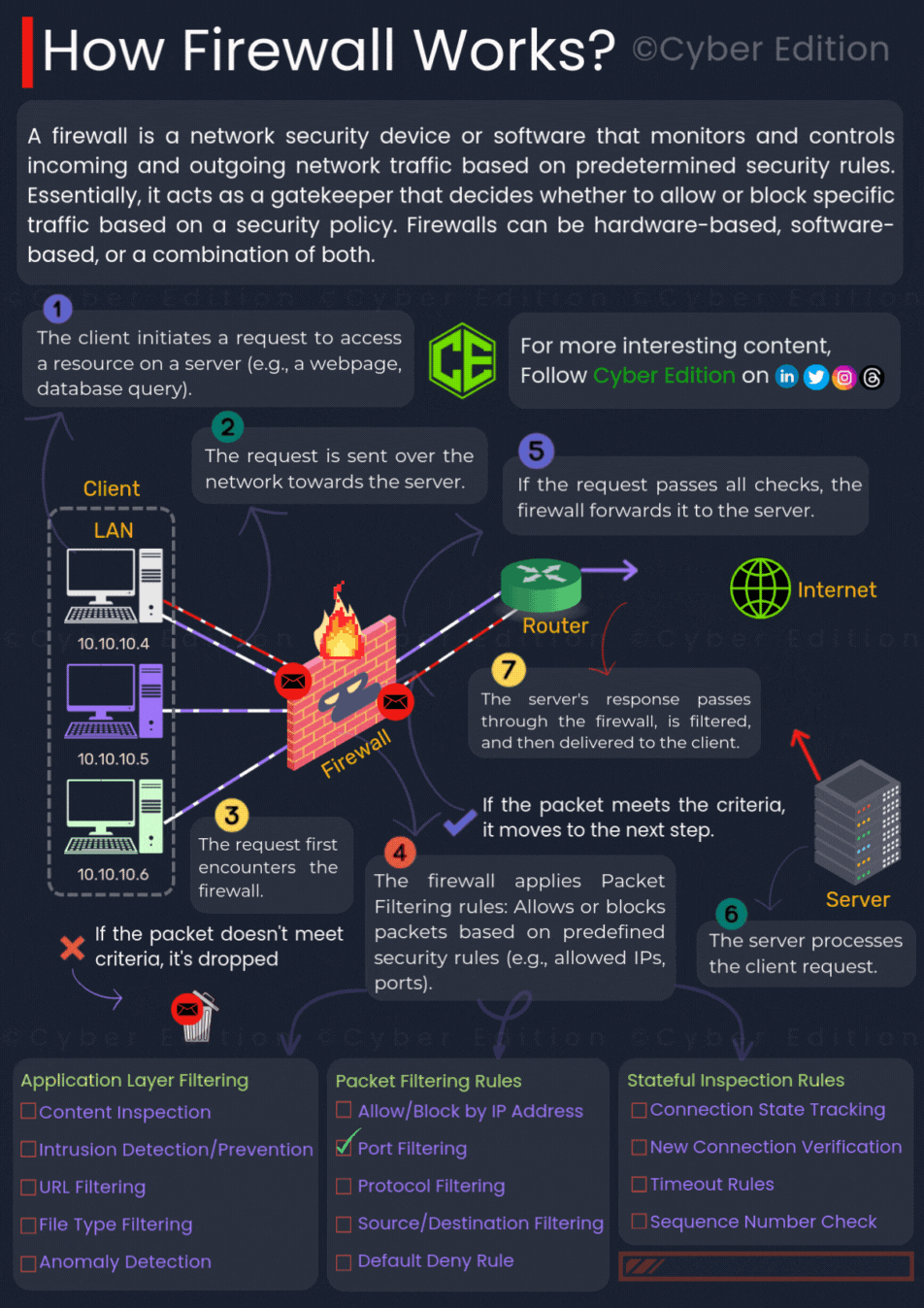
Provided image clearly illustrates the process of how a firewall works. Let us break down each step in detail:
Step 1: A Client Sends a Request
When a user tries to access a resource such as a website, email server, or online service, their device generates a data packet. This packet contains information like the destination address, source address, and the requested service.
Step 2: The Request Travels Through the Network
The packet moves through various networking devices like routers and switches on its way to the destination server. At this stage, the packet has not yet been checked for safety.
Step 3: The Packet Reaches the Firewall
Before the packet can enter the internal network, it arrives at the firewall. The firewall is positioned as a protective barrier between internal systems and external networks. It is the first checkpoint that decides whether the packet should proceed or be stopped.
Step 4: Firewall Applies Filtering Rules
The firewall examines the packet using security rules that have been configured by the network administrator. These rules may include:
- Allowing or blocking based on IP address
- Allowing or blocking based on network ports (for example, port 443 for secure web traffic)
- Allowing or blocking based on protocols like HTTP, HTTPS, FTP
- Applying a default deny policy, which blocks all traffic that does not match approved criteria
If the packet does not meet these conditions, it is discarded immediately.
Step 5: Stateful Inspection and Deep Analysis
Modern firewalls go beyond basic filtering. They perform stateful inspection, which means they:
- Keep track of active connections to ensure each packet belongs to a legitimate session.
- Check new connection attempts against known safe or unsafe patterns.
- Detect anomalies such as unexpected packet sequences or abnormal behavior.
This ensures that even if a packet looks harmless individually, it will be blocked if it is part of a suspicious pattern.
Step 6: Packet is Forwarded to the Server
If the packet passes all checks, the firewall forwards it to the destination server. The server then processes the request, such as loading a web page or providing requested data.
Step 7: Server Response Returns Through the Firewall
When the server sends a response back to the client, the firewall inspects this outgoing traffic as well. This double-check ensures that only safe and authorized data leaves or enters the network, providing two-way protection.
Advanced Firewall Capabilities
Modern firewalls often include additional security features:
- Application Layer Filtering: Examines the actual content of data packets, blocking harmful files or applications.
- Intrusion Detection and Prevention: Identifies and stops attacks as they happen.
- Anomaly Detection: Recognizes unusual traffic patterns that may indicate ongoing threats.
- Content Filtering: Blocks access to malicious or unwanted websites.
Why Are Firewalls Important?
Firewalls play a vital role in cybersecurity for several reasons:
- They prevent unauthorized access: Only trusted users and systems can communicate with your network.
- They block malware and ransomware: Harmful software is stopped before it can infect systems.
- They help with compliance: Many industries require firewalls to meet security standards.
- They provide visibility and control: Security teams can monitor activity, analyze threats, and respond quickly.
Conclusion
A firewall is not just a basic barrier but an intelligent, dynamic security tool that continuously monitors and filters network traffic. By understanding how a firewall works step by step, even beginners can appreciate its importance in protecting data and systems from modern cyber threats.
Whether you are protecting a personal home network or a large corporate infrastructure, a properly configured firewall is one of the most critical components of a strong cybersecurity strategy.
Also read: Revolutionizing Web Security With Advanced Firewall Capabilities













.webp)


