Xenon : A New Tool In The Mythic Framework
Xenon is a Windows agent designed for the Mythic framework, inspired by tools like Cobalt Strike. It is currently in an early stage of development and is not considered operationally secure (OPSEC safe), meaning it may contain memory leaks and other issues that could lead to crashes. Despite these limitations, Xenon offers several features that make it useful for...
OSCP : Navigating The Essential Toolkit For Penetration Testing
The OSCP (Offensive Security Certified Professional) certification is a highly respected credential in the cybersecurity industry, focusing on hands-on penetration testing skills. To achieve this certification, candidates must demonstrate proficiency in using various tools and techniques to identify vulnerabilities and exploit them. Here's an overview of some key tools and their functions relevant to OSCP: Network Enumeration And Scanning Nmap: A...
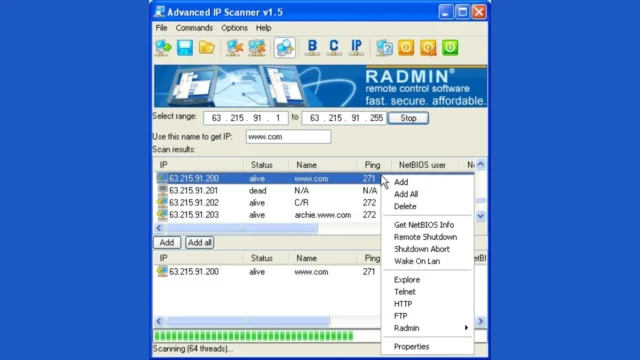
Famatech Advanced IP Scanner Or Advanced Port Scanner Usage
Famatech offers two powerful network management tools: Advanced IP Scanner and Advanced Port Scanner. Both tools are designed to enhance network security and management capabilities, but they serve different purposes. Advanced IP Scanner Advanced IP Scanner is a free, fast, and user-friendly tool for scanning IP addresses and ports within a Local Area Network (LAN). It provides detailed information about network...
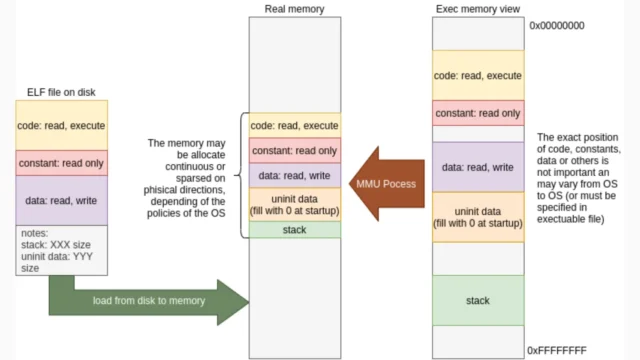
ELF Loader And PS5-JAR-Loader : Tools For Enhanced Functionality
In the realm of PlayStation 5 (PS5) development, two significant tools have emerged to enhance the console's capabilities: the ELF Loader and the PS5-JAR-Loader. These tools leverage exploits in the PS5's BD-J layer to enable the execution of custom code, offering developers and enthusiasts a way to extend the console's functionality beyond its standard limits. ELF Loader The ELF Loader is...
C2IntelFeeds: Real-Time C2 Infrastructure Tracking for Threat Intelligence
What is C2IntelFeeds? C2IntelFeeds is an open-source intelligence project that provides real-time Command and Control (C2) infrastructure data. Using data from Censys and custom detection signatures, it identifies and tracks malicious C2 servers, domains, and IP addresses that threat actors use for cyberattacks. By leveraging these feeds, security teams can detect threats earlier, improve incident response, and block malicious infrastructure before...
goLAPS : The Ultimate Guide To Managing LAPS Passwords with Golang
goLAPS is a tool designed to interact with the Local Administrator Password Solution (LAPS) in a domain environment. It allows users to retrieve and set LAPS passwords for domain-joined computers using simple binding over LDAP and LDAPS protocols. This project was inspired by pyLAPS and serves as a learning exercise in Golang. Capabilities Of goLAPS Retrieve LAPS Passwords: goLAPS can fetch...
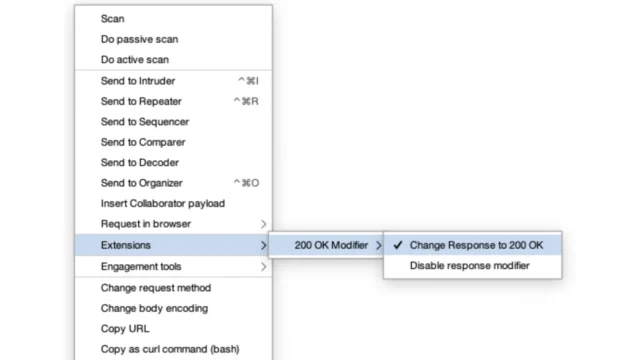
200-OK-Modifier : Mastering Web Application Analysis And Penetration Testing
The 200-OK-Modifier is a versatile Burp extension that allows users to modify server response codes in real-time, specifically changing them to "200 OK." This capability is particularly useful in web application testing and penetration testing scenarios where manipulating server responses can help identify vulnerabilities or simulate specific conditions. Functionality The primary function of the 200-OK-Modifier is to intercept and alter HTTP...
NullGate : Advancing Evasion Techniques In Windows Exploitation
NullGate is a sophisticated project designed to leverage NTAPI functions using indirect syscalls, incorporating the FreshyCalls method with a novel approach to dynamic syscall number retrieval. It also employs a unique technique to bypass Windows Defender's memory scanning, making it a powerful tool for process injection. Key Features Of NullGate Indirect Syscalls: NullGate uses indirect syscalls to invoke NTAPI functions, providing...
WebHunt : A Dive Into Web App Testing For Bug Bounty Hunting
WebHunt is an innovative project that focuses on web application testing, particularly for bug bounty hunting. It leverages powerful tools like Burp Suite to identify vulnerabilities in web applications. Here's a closer look at how WebHunt functions and the tools it utilizes. Introduction To WebHunt WebHunt is not to be confused with WebHunt.io, a B2B growth agency specializing in AI-driven lead...
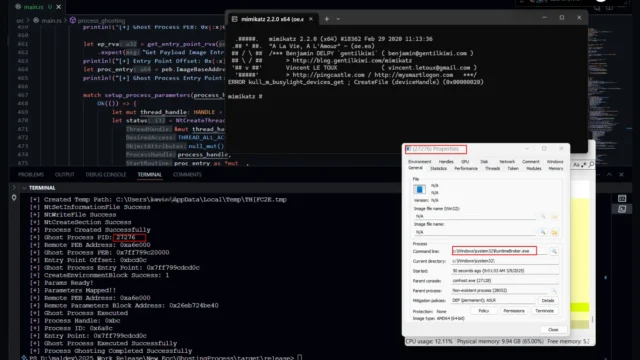
Process Ghosting In Rust : Crafting Evasive Applications On Windows
Process ghosting is a sophisticated technique used to evade detection by security tools on Windows systems. It involves creating a temporary file, marking it for deletion, and then executing its contents from memory without leaving a persistent file on disk. This method allows malicious code to run undetected, as traditional security software often relies on scanning files on disk. How...