Octosuite : Advanced Github OSINT Framework
Octosuite is an open-source lightweight yet advanced osint framework that targets Github users and organizations. With over 10+ features, octosuite only runs on 2 external dependencies (for the GitHub alt) and 1 dependency (for the PyPI package). And returns the gathered intel in a well and highly readable format. Installation Clone from Github git clone https://github.com/rly0nheart/octosuite.git cd octosuite pip install -r requirements.txt Install from PyPI pip...
Gitbleed_Tools : For Extracting Data From Mirrorred Git Repositories
Gitbleed_Tools, this repo contains shell scripts that can be used to download and analyze differences between cloned and mirror Git repositories. For more information about the underlying quirk in Git behavior, please visit read our blog post. What Do These Scripts Do? These scripts will clone a copy of the given Git repository, both as regular clone and mirrored ("--mirror") option. It...
Hcltm : Documenting Your Threat Models With HCL
Hcltm is a tool for Documenting Your Threat Models With HCL. There are many different ways in which a threat model can be documented. From a simple text file, to more in-depth word documents, to fully instrumented threat models in a centralized solution. Two of the most valuable attributes of a threat model are being able to clearly document...
KNX-Bus-Dump : A Tool To Listen On A KNX Bus Via TPUART And The Calimero Project Suite
KNX-Bus-Dump is a popular building automation protocol and is used to interconnect sensors, actuators and other components of a smart building together. Our KNX Bus Dump tool uses the Calimero java library, which we contributed to for the sake of this tool, to record the telegrams sent over a KNX bus. Particularly, our tool accesses the KNX bus through...
ScheduleRunner : A C# Tool With More Flexibility To Customize Scheduled Task
ScheduleRunner is a Scheduled task is one of the most popular attack technique in the past decade and now it is still commonly used by hackers/red teamers for persistence and lateral movement. A number of C# tools were already developed to simulate the attack using scheduled task. I have been playing around with some of them but each of them...
Tiktok-Scraper : TikTok Scraper. Download Video Posts, Collect User/Trend/Hashtag/Music Feed Metadata
Tiktok-Scraper is used to Scrape and download useful information from TikTok. This is not an official API support and etc. This is just a scraper that is using TikTok Web API to scrape media and related meta information. Features Download unlimited post metadata from the User, Hashtag, Trends, or Music-Id pagesSave post metadata to the JSON/CSV filesDownload media with and without the watermark and save...
Fennec : Artifact Collection Tool For *Nix Systems
Fennec is an artifact collection tool written in Rust to be used during incident response on *nix based systems. fennec allows you to write a configuration file that contains how to collect artifacts. Features A single statically compiled binary Execute any osquery SQL query Execute system commands Parse any text file using regex Ability to collect system logs and files Return data in structured manner Support multiple...
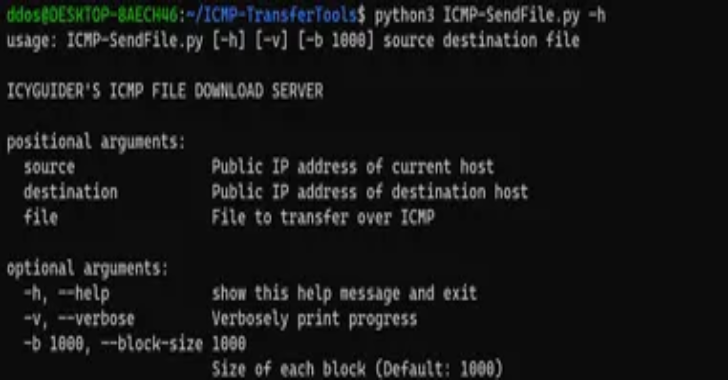
ICMP-TransferTools : Transfer Files To And From A Windows Host Via ICMP In Restricted Network Environments
ICMP-TransferTools is a set of scripts designed to move files to and from Windows hosts in restricted network environments. This is accomplished using a total of 4 different files, consisting of a python server and powershell client for each transfer direction (Download & Upload). The only dependency required is Impacket for one of the python scripts. It can be installed via pip...
Covert-Control : Google Drive, OneDrive And Youtube As Covert-Channels – Control Systems Remotely By Uploading Files To Google Drive, OneDrive, Youtube Or Telegram
Covert-Control systems remotely by uploading files to Google Drive, OneDrive, Youtube or Telegram using Python to create the files and the listeners. It allows to create text files, images, audio or videos, with the commands in cleartext or encrypted using AES. covert-googledrive.py - Control systems uploading files to a public folder in Google Drive.covert-onedrive.py - Control systems uploading files to...
FormatFuzzer : A Framework For High-Efficiency, High-Quality Generation And Parsing Of Binary Inputs
FormatFuzzer is a framework for high-efficiency, high-quality generation and parsing of binary inputs. It takes a binary template that describes the format of a binary input and generates an executable that produces and parses the given binary format. From a binary template for GIF, for instance, FormatFuzzer produces a GIF generator - also known as GIF fuzzer. Generators produced by FormatFuzzer are highly efficient, producing thousands of valid test inputs per second...












.png)
.png)
.png)