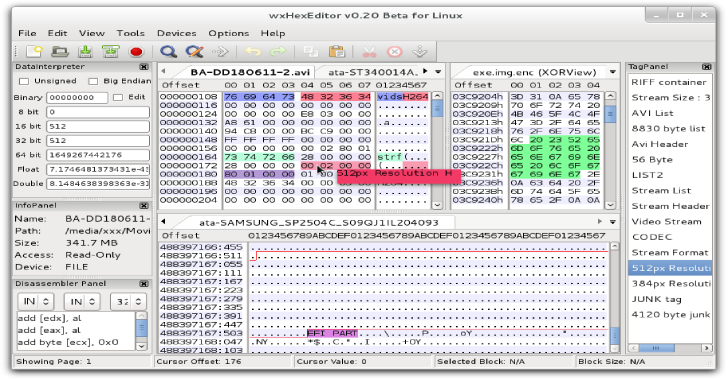
wxHexEditor : Official GIT Repo For Devices On Linux, Windows & MacOSX
wxHexEditor is a Hex Editor / Disk Editor for Huge Files or Devices on Linux, Windows and MacOSX. It is not an ordinary hex editor, but could work as low level disk editor too. If you have problems with your HDD or partition, you can recover your data from HDD or from partition via editing sectors in raw hex.You can...
When technology tempts you to cheat on your partner
There is nothing wrong with having a Facebook or WhatsApp account, nor with having friends of the opposite sex, as long as you behave with them as an honest and committed person. There is also nothing wrong with visiting http://smstrackers.com/tracking-someones-facebook-messages-is-now-possible/ to anticipate the infidelity but we must trust our partner. The Internet, in many ways, has come to make life...
DeathRansom : A Ransomware To Bypass Technics For Educational Purposes
DeathRansom is a ransomware developed in python, with bypass technics, for educational purposes. What is a ransomware? A ransomware is malware that encrypts all your files and shows a ransom request, which tells you to pay a set amount, usually in bitcoins (BTC), in a set time to decrypt your files, or he will delete your files. How it works? First, the script...
Nuclei : A Fast Tool For Configurable Targeted Scanning
Nuclei is a fast tool for configurable targeted scanning based on templates offering massive extensibility and ease of use. It is used to send requests across targets based on a template leading to zero false positives and providing effective scanning for known paths. Main use cases for it is during initial reconnaissance phase to quickly check for low hanging fruits...
Print-My-Shell : Process Of Generating Various Reverse Shells
Print-My-Shell is a python script, wrote to automate the process of generating various reverse shells based on PayloadsAllTheThings and Pentestmonkey reverse shell cheat sheets. Using this script you can easily generate various types of reverse shells without leaving your command line. This script will come in handy when you are playing CTF like challenges. Available Shell Types BashPerlRubyGolangNetcatNcatPowershellAwkLuaJavaSocatNodejsTelnetPython Git Installation #clone the repo$ git...
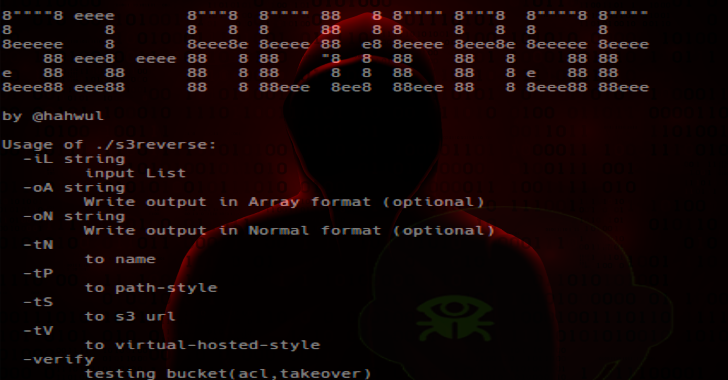
S3Reverse : Format Of Various S3 Buckets
S3Reverse is a format of various s3 buckets is convert in one format. for bugbounty and security testing. Install $ go get -u github.com/hahwul/s3reverse Usage Input options Basic Usage Usage of ./s3reverse:-iL stringInput List-oA stringWrite output in Array format (optional)-oN stringWrite output in Normal format (optional)-tNto name-tPto path-style-tSto s3 url-tVto virtual-hosted-style-verifytesting bucket(acl,takeover) Using from file $ s3reverse -iL sample -tNudemy-web-upload-transitionalgithub-cloudgithub-production-repository-file-5c1aebgithub-production-upload-manifest-file-7fdce7github-production-user-asset-6210dfgithub-education-webgithub-jobss3-us-west-2.amazonaws.comoptimizelyapp-usa-modeast-prod-a01239fdocswipely-merchant-assetsadslfjasldfkjasldkfjalsdfkajsljasldfcbphotovideocbphotovideo-eupublic.chaturbate.comwowdvrcbvideouploadtestbuckettesttest Using from pipeline $ cat sample | s3reverse...
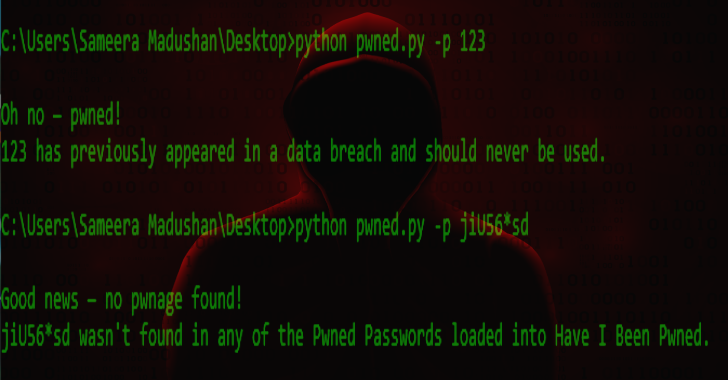
Pwned : Simple CLI Script To Check If You Have A Password
Pwned is a simple command-line python script to check if you have a password that has been compromised in a data breach. This script uses haveibeenpwned API to check whether your passwords were leaked during one of the many breaches of online services. This API uses k-Anonymity model that allows a password to be searched for by partial hash in...
Project iKy v2.5.0 – Tool That Collects Information From An Email
Project iKy is a tool that collects information from an email and shows results in a nice visual interface. Installation Clone repository git clone https://gitlab.com/kennbroorg/iKy.git Install BackendRedisYou must install Redis wget http://download.redis.io/redis-stable.tar.gztar xvzf redis-stable.tar.gzcd redis-stablemakesudo make install Python stuff and CeleryYou must install the libraries inside requirements.txt python3 -m pip install -r requirements.txt Install FrontendNode First of all, install nodejs. Dependencies Inside the directory frontend install the dependencies cd frontendnpm install Wake...
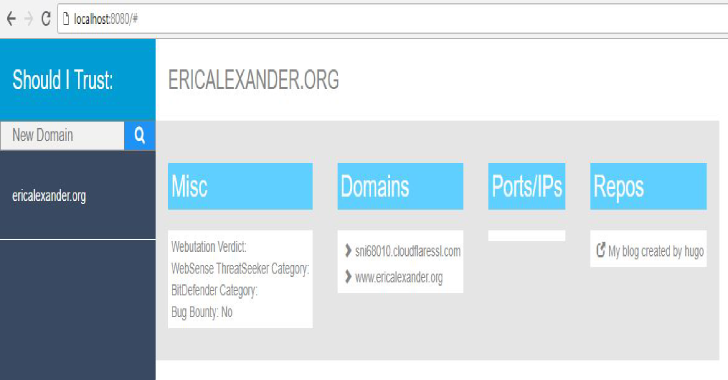
Should-I-Trust : OSINT Tool To Evaluate Trustworthiness Of A Company
Should-I-Trust is a tool to evaluate OSINT signals for a domain. You're part of a review board that's responsible for evaluating new vendors. You're specifically responsible for ensuring new vendors meet compliance and security requirements. Standard operation procedure is to ask for one or all of the following: SOC report, VSAQ, CAIQ, SIG/SIG-Lite. All vendors will not have these reports...
5 Simple Ways to Hack Gmail Accounts 2020
Gmail is one of the highly secured email platforms and the Gmail hack is not an easy process until and unless you having any of these 5 spy tools. A person’s Gmail account can hold a lot of crucial information. It can tell you all about the person’s recent activities and much more. Moreover, most of the online accounts...