EarlyCascade : Revolutionizing Process Injection To Outmaneuver Endpoint Security
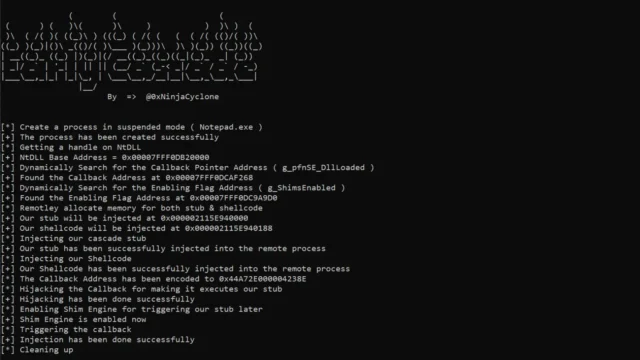
EarlyCascade is a cutting-edge process injection technique developed by Outflank to evade modern Endpoint Detection and Response (EDR) systems. This method operates during the early stages of process creation, injecting and executing malicious code before EDRs initialize their user-mode detection measures. By leveraging the Shim engine and hijacking its callback, EarlyCascade achieves stealthy execution while minimizing detection risks. Key Features...
Understanding Userland Exec : A Comprehensive Overview
Userland Exec is a sophisticated technique that replaces the current process image within the existing address space with a new one. Unlike the traditional execve system call, userland exec achieves this without altering kernel-level process structures, meaning that utilities will still report the original process name. This feature makes it particularly useful for scenarios requiring stealth or executing binaries...
Binary Ninja Ollama Plus : Elevating Code Analysis With Advanced Features For Security Professionals
The Binary Ninja Ollama Enhanced plugin is an advanced tool tailored for developers and reverse engineers, offering enhanced functionality for binary analysis. Originally developed by Austin Haggard, this version has been significantly upgraded by Dani Martinez (dan1t0) to improve compatibility and add new analysis features. Key Enhancements Improved Compatibility: The plugin replaces the original Ollama library with the Python requests library,...
Niri : Revolutionizing Window Management With Scrollable Tiling On Wayland
Niri is a scrollable-tiling Wayland compositor designed to offer a unique and efficient window management experience. Built from the ground up, it introduces several innovative features tailored for modern workflows while maintaining compatibility with various hardware configurations. Key Features Scrollable Tiling: Windows are arranged in columns on an infinite horizontal strip. Opening a new window does not resize existing ones, ensuring...
Understanding Reqwest : A Comprehensive Rust HTTP Client
Reqwest is a robust and ergonomic HTTP client library for Rust, designed to simplify web interactions in both synchronous and asynchronous contexts. Its extensive feature set makes it a go-to choice for developers building HTTP-based applications. Key Features Of Reqwest Async and Blocking Clients: Reqwest supports both asynchronous (non-blocking) and synchronous (blocking) HTTP requests. The asynchronous client leverages Rust's async/await syntax, ideal for...
Gitoxide : Harnessing Rust For Next-Generation Git Operations
Gitoxide is a modern, pure-Rust implementation of Git, designed to offer a future-proof, high-performance alternative to traditional Git tools. Its primary goal is to provide developers with a robust, efficient, and user-friendly experience while maintaining compatibility with Git's on-disk format. Below, we explore its key functions and features. Core Features And Tools Gitoxide provides two main command-line tools: gix: A low-level tool...
ChromeStealer : A Tool For Extracting Chrome Passwords
ChromeStealer is an educational tool developed by @bernKing20 to demonstrate how to extract and decrypt stored passwords from Google Chrome on Windows systems using C/C++. The project aims to address gaps in existing resources by providing a functional and detailed implementation. Key Features And Functionality ChromeStealer focuses on decrypting passwords stored locally by Google Chrome. Chrome uses the AES-GCM algorithm for...
DCOMUploadExec : A Tool For Lateral Movement Exploits Using IMsiServer
DCOMUploadExec is a proof-of-concept (PoC) tool designed to exploit the Distributed Component Object Model (DCOM) for lateral movement within a network. By leveraging the IMsiServer interface, this tool demonstrates how attackers can abuse Windows Installer's COM functionality to execute payloads on remote systems. Below is an overview of its functionality, usage, and limitations. Overview Of DCOMUploadExec DCOMUploadExec consists of two key...
Overview Of CPAL : Cross-Platform Audio Library
CPAL (Cross-Platform Audio Library) is a low-level, pure Rust library designed for audio input and output. It provides developers with tools to interact with audio devices across multiple platforms, making it a versatile choice for building audio-related applications. Below is an overview of its key features, supported platforms, and usage. Key Features Audio Host and Device Management: Enumerate supported audio hosts and...
WhacAMole : A Comprehensive Malware Analysis Tool
WhacAMole (WAM) is a cutting-edge tool designed for in-depth memory and process analysis to detect, investigate, and document anomalies caused by malware. It offers unparalleled capabilities for cybersecurity professionals to uncover hidden threats and analyze suspicious behaviors within system processes. Here’s an overview of its functions and features: Core Functionality WhacAMole operates by analyzing memory regions, processes, and modules in real-time....