The Student’s Guide to Cyber Security – 9 Top Tips to Prevent Yourself From Hackers
The rise of the Internet has brought tremendous benefits to people’s education. But, it also makes people targets to hackers and theft of sensitive information, which is why every student must learn about online cyber security at some point. These days, almost every student owns a smart device or a laptop. This immense use of technology brings up devastating...
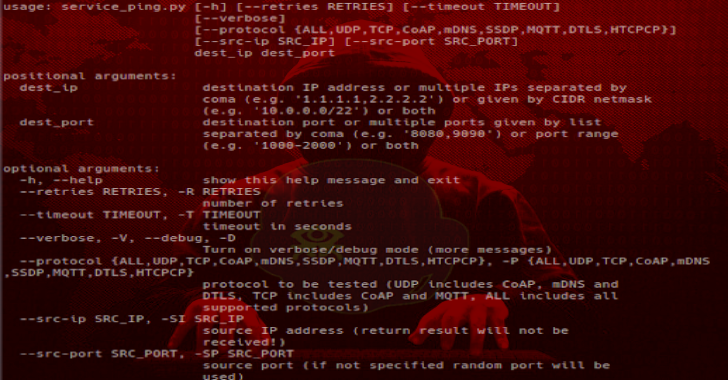
Cotopaxi : Set Of Tools For Security Testing Of Internet Of Things Devices Using Specific Network IoT Protocols
Cotopaxi set of tools for security testing of Internet of Things devices using protocols like: CoAP, DTLS, HTCPCP, mDNS, MQTT, SSDP. Requirements Currently Cotopaxi works only with Python 2.7.x, but future versions will work also with Python 3. If you have previous installation of scapy without scapy-ssl_tls, please remove it or use venv. Installation of main libraries: scapy-ssl_tls (this will install also scapy in...
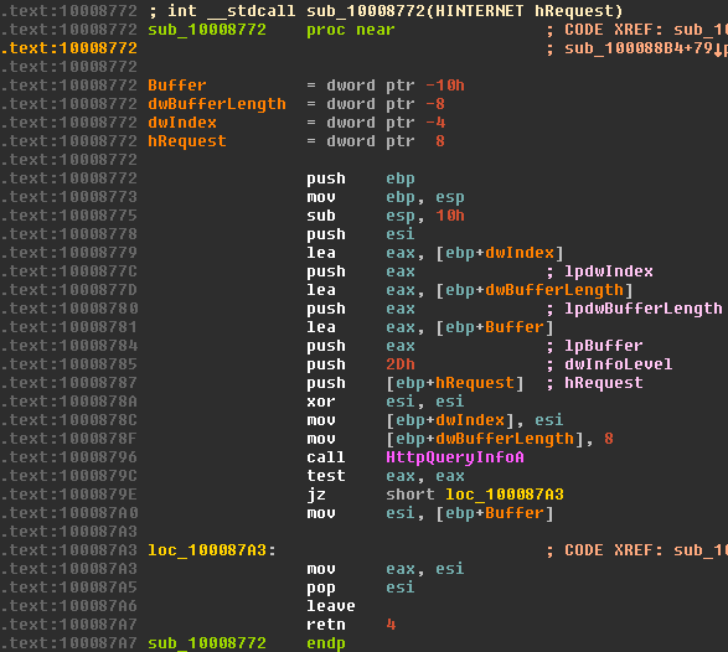
Auto_Re : IDA PRO Auto-Renaming Plugin With Tagging Support
Auto_re dummy-named functions, which have one API call or jump to the imported API. Before After Also Read - UniFuzzer : A Fuzzing Tool For Closed-Source Binaries Based On Unicorn & LibFuzzer Assigning TAGS to functions accordingly to called API-indicators insideSets tags as repeatable function comments and displays TAG tree in the separate view Some screenshots of TAGS view: How TAGs look in unexplored...
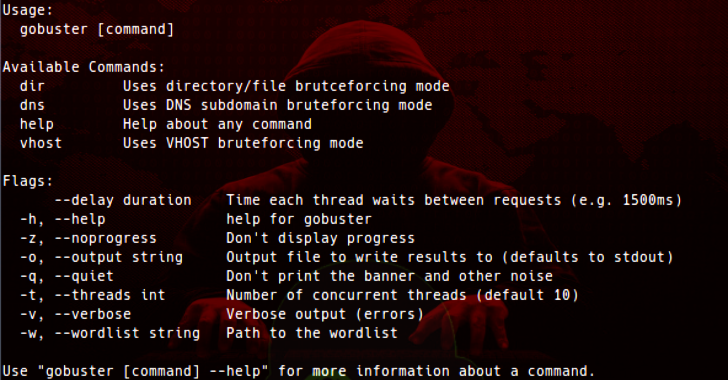
GoBuster : Directory/File, DNS & VHost Busting Tool Written In Go
Gobuster is a tool used to brute-force like URIs (directories and files) in web sites, DNS subdomains (with wildcard support) and Virtual Host names on target web servers. WHY!? Something that didn't have a fat Java GUI (console FTW).To build something that just worked on the command line.Something that did not do recursive brute force.Something that allowed me to brute force...
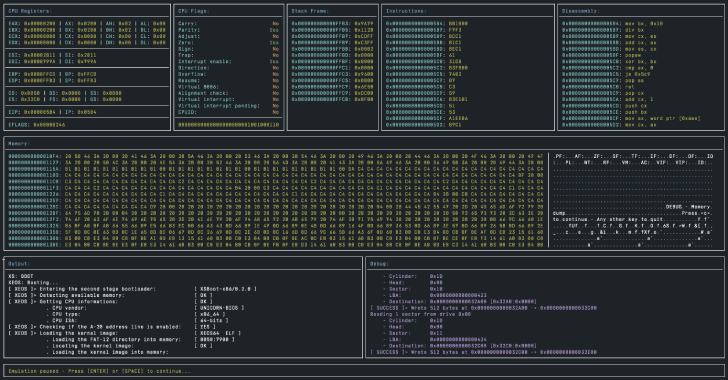
Unicorn-Bios : Basic BIOS Emulator for Unicorn Engine
Unicorn-Bios is a basic BIOS emulator/debugger for Unicorn Engine. Usage Usage: unicorn-bios BOOT_IMGOptions: --help / -h: Displays help.--memory / -m: The amount of memory to allocate for the virtual machine (in megabytes). Defaults to 64MB, minimum...
UniFuzzer : A Fuzzing Tool For Closed-Source Binaries Based On Unicorn & LibFuzzer
UniFuzzer is a fuzzing tool for closed-source binaries based on Unicorn and LibFuzzer. Currently it supports fuzzing 32-bits LSB ELF files on ARM/MIPS, which are usually seen in IoT devices. Features very little hack and easy to buildcan target any specified function or code snippetcoverage-guided fuzzing with considerable speeddependence resolved and loaded automaticallylibrary function override by PRELOAD Build Reverse the target binary and find interesting functions for...
RITA : Real Intelligence Threat Analytics
RITA is a real intelligence threat analytics. RITA is an open source framework for network traffic analysis. The framework ingests Bro/Zeek Logs in TSV format, and currently supports the following major features: Beaconing Detection: Search for signs of beaconing behavior in and out of your network DNS Tunneling Detection Search for signs of DNS based covert channels Blacklist Checking: Query blacklists...
How To Prevent Hacking in 2020
Hacking is a term that refers to an unauthorized intrusion into a computer network or system. Hackers may alter a computer system and its security features to accomplish fraudulent and illegal goals, depending on the functions of the devices connected to the network. The entire procedure may involve several different techniques, like password cracking and installing malware. You can use...
Eaphammer : Targeted Evil Twin Attacks Against Wpa2-Enterprise Networks
EAPHammer is a toolkit for performing targeted evil twin attacks against WPA2-Enterprise networks. It is designed to be used in full scope wireless assessments and red team engagements. As such, focus is placed on providing an easy-to-use interface that can be leveraged to execute powerful wireless attacks with minimal manual configuration. To illustrate just how fast this tool is,...
Postenum : Tool For Basic/Advanced Privilege Escalation Techniques
Postenum is a clean, nice and easy tool for basic/advanced privilege escalation vectors/techniques. The tool is intended to be executed locally on a Linux box. Be more than a normal user. be the ROOT. USE ./postenum.sh ./postenum.sh -s ./postenum.sh -c Also Read - SIEM – A Beginner’s Guide to Security Information and Event Management Tools Options -a : All -s : Filesystem...